Reviewed by BitHead (discussion thread here).
When this review started at the beginning of August 2012, Internet Evidence Finder (IEF) was a project of Jad Saliba of JADSoftware. At that time the version was 5.41.
The interface was simple, and IEF was an easy to use tool that found a lot of artifacts and displayed them in an easy to follow report.
In the middle of August I was contacted by Adam Belsher of JADSoftware and told there was going to be a few major changes coming to JADSoftware. A week later Saliba announced “JADsoftware has a new identity, including a new company name – Magnet Forensics.”In his first blog post on the Magnet Forensics site, Saliba wrote, “A lot has changed since I launched JADsoftware and first developed Internet Evidence Finder (or IEF) while working as a police officer and forensic examiner. After a couple of years juggling both jobs, I realized IEF had enormous potential to help you perform better investigations, so I decided to dedicate myself to developing the software full-time. The growth the company has experienced since then has exceeded my highest expectations.”
And there were a lot more changes than just the name.
The install is a relatively straight forward Windows install that consists of accepting the EULA and clicking “Next” a bunch of times.
One item that I did question during the install is the .Net 4 install. The installer showed .Net4 was not installed. I was pretty sure it was and looked in my Programs and Features and it showed the .Net 4 Client Profile was installed, however the installer adds .Net 4 Extended (and an unpatched version at that). And even though I have Microsoft C++ 2008 Redistributable, the installer also installs Microsoft C++ 2005 (patched).
Launch the program for the first time and the name change is evident. However, just as in previous versions, I have to question the need for the “splash screen” that seems to be there only as a reason to show off the name. There could just as easily be a two second timer on a splash screen that takes you straight to the program interface.

The interface is slightly different than previous versions. Also, in the current version the first step is to select your search location rather than choosing your exam type.
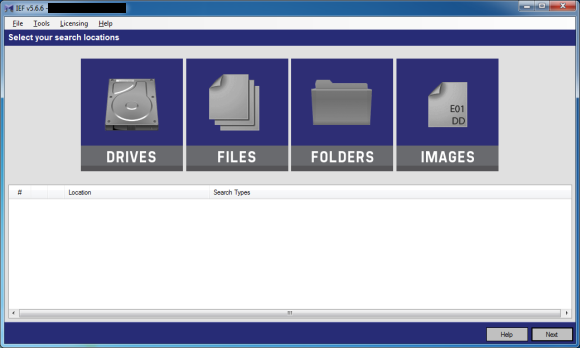
The change in the interface also eliminates the annoyance in the previous version where you could see the partition or volume you could search, but unless the examiner clicked to highlight it the next button remained greyed out.
Like previous versions there are several presets for what is to be searched. Following are screenshots of what each preset searches.
The first choice is a “Full Search”.
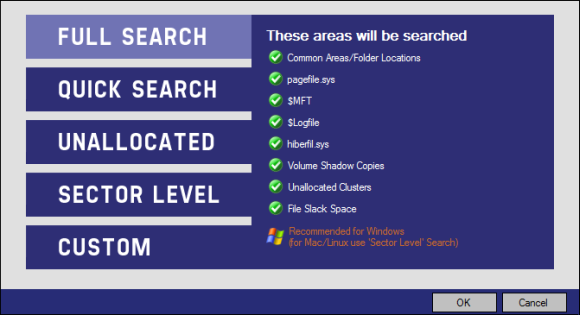
Next is a “Quick Search”.
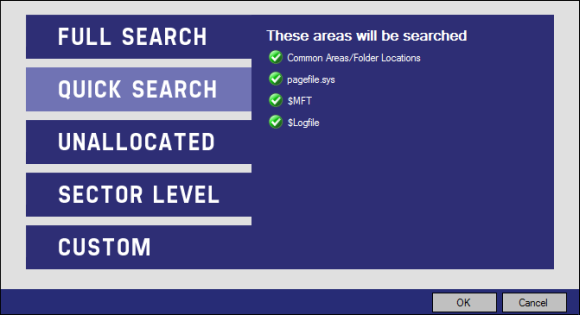
The next choice is a search of “Unallocated”.
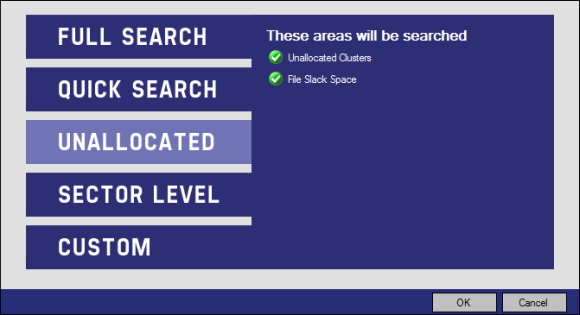
A “Sector Level” search.
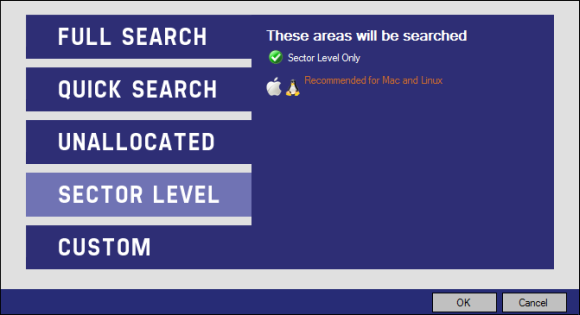
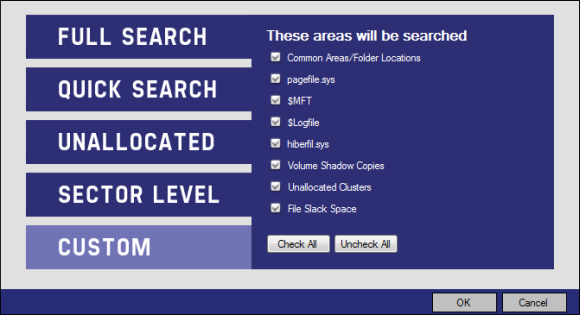
And last a “Custom” search where you can select the areas to be searched.
Test
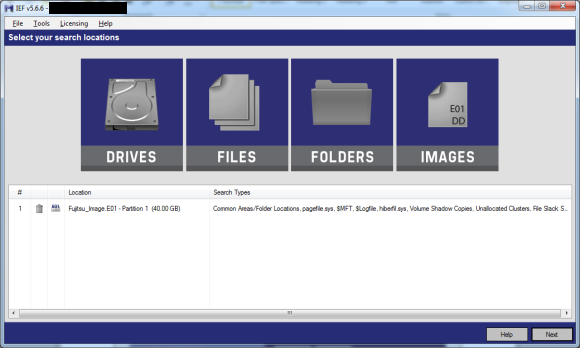
In this test example I ran a Full Search on an E01 image.
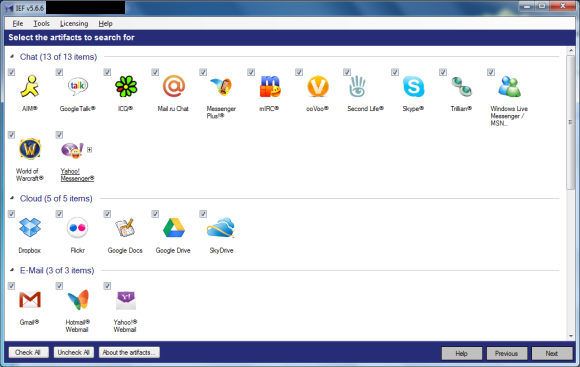
There are many artifacts that can be searched for in IEF. The following two screenshots (the list is long and required multiple screenshots to get everything in) show the categories: Chat, Cloud, E-Mail, Mobile Backups, Peer-to-Peer, Social Networking, and Web History.
If you have Yahoo Messenger selected you will see the following informational message:
Moving on, the examiner is presented with a screen where output information and case info is selected.
Select browse and choose your case folder. This is where I ran into another annoyance with IEF; there is no way to create a new folder. (LAST MINUTE NOTE: This has been fixed in 5.6.8)
Once the destination and case information is input the examiner clicks the aptly named “Find Evidence” button (which I am certain brings a chuckle to anyone that has read Harlan Carvey’s Windows Forensic Analysis book).
IEF provides a Search Status window, although the “Time Remaining” indicator is a bit baffling as the numbers climb up and down on each item being searched. Also it should be noted that the time remaining is the time for each item and not the overall time.
IEF also launches the Report Viewer window which updates as new artifacts are found.
The 40 GB test image I used took just over 51 minutes to process.
The Report Viewer shows the number of artifacts found by IEF.
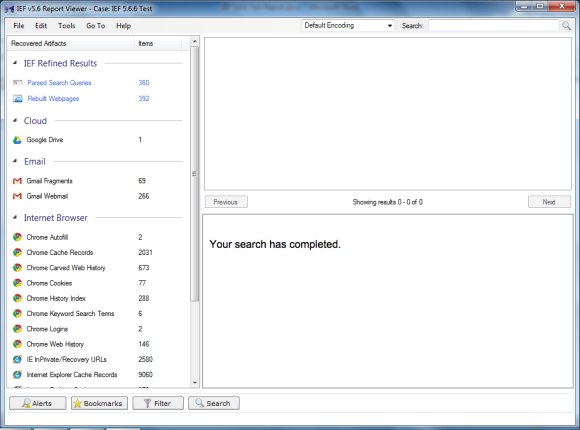
At this point I ran out of time and closed the IEF Report Viewer for the night. Which brings up my segue to re-opening a case in Report Viewer.
When you create a report you get a folder called “Portable Case casename” which contains a Windows installer Install IEF Report Viewer.exe so a case can be passed to an investigator, attorney, client, etc.
The install is straightforward.
Again if the client does not have MS Visual C++ 2005 Redistributable it will be installed along with the base IEF program.
On completion your investigator will be presented with the IEF Report Viewer.
Open the case and the Report Viewer populates with the results from the case. One gremlin I did encounter, you would think the report is in the Portable Case folder where the installer for the viewer is located. However if you load the case from that folder you get a message at the top of the Report Viewer window “Case: Error Getting Case Info”. The results in the Recovered Artifact pane are the same, but the case info is not populated correctly. If you open the case from the case folder the case information populates correctly.
When you open a case IEF provides a helpful hint to those unfamiliar with the program in the lower right pane of the Report Viewer.
Following are samples of the results from the artifacts. I did not take screen shots of every artifact because by the time I redacted them, there was really no point in showing them. Suffice to say, IEF can present a lot of information.
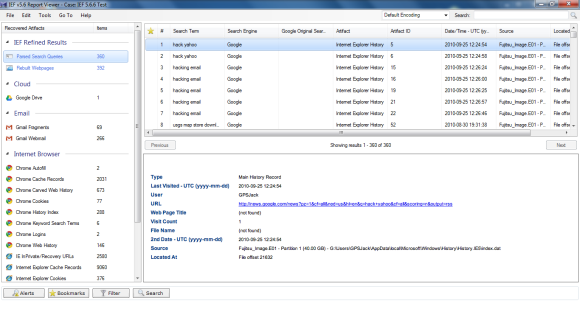
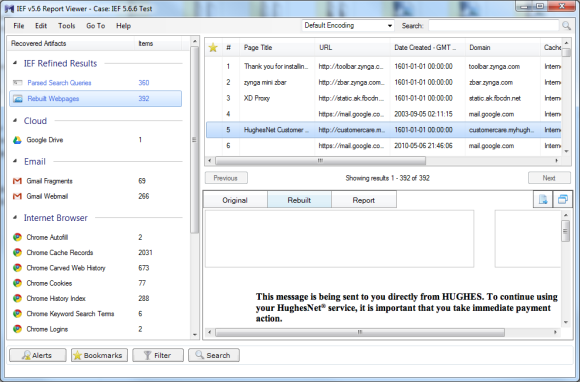
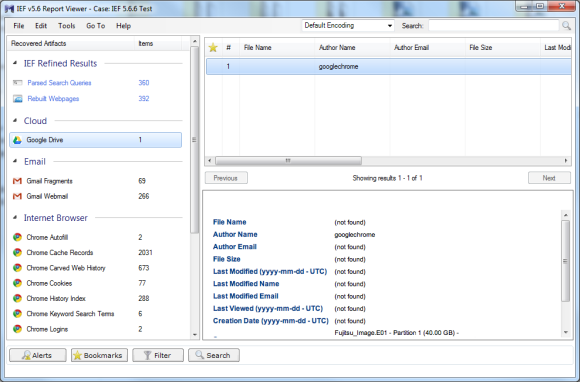
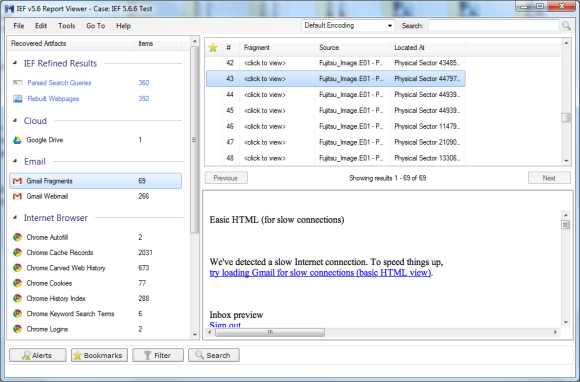
The folks at Magnet are very busy with new versions. As I noted at the beginning of this review I started with 5.41. And while the screen shots are of 5.6.6 I also tested 5.70.0054 and 5.71.0013. I thought it would be interesting to show how many more artifacts each subsequent version of IEF finds. The additional artifacts are not necessarily just more IE artifacts; IEF is evolving and able to find a wider variety of artifacts.
The following screen shots show the progression from 5.41 through 5.71.0013. (Please note that I am opening the results in the current version but showing the results of the search in each version).
5.41 results
5.5 results
5.64 results
5.66 results
5.7 results
5.71.0013 results
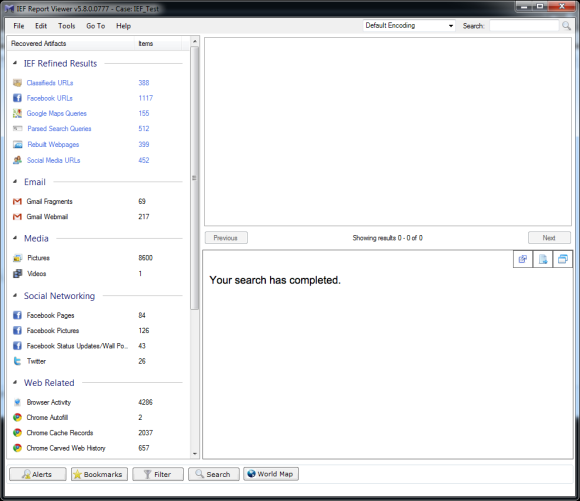
Although the screen shots show only a portion of the results, it is quite clear that each version is an improvement in both the type of artifacts and the number of artifacts.
In any review it is always good to compare a tool against other similar tools, however, one of the additional questions that I wanted to answer about IEF as it becomes more robust and is programmed to find more types of artifacts is how does it compare to single use tools.
One of the obvious competitors to IEF is NetAnalysis. I took the same test image and ran NetAnalysis and generated a “Group By Type Report” and got a 4827 page PDF report. One of the first things I discovered from that little test is that it is very difficult to compare the results of these two tools. For example IEF and NetAnalysis use slightly different names for the results. IEF uses the term Cache Records, NetAnalysis uses Cache. You would think that would be easy to compare, yet IEF breaks Cache Records out for IE, Mozilla, and Chrome; NetAnalysis has a lot of Cache records with not a whole lot to distinguish where the cache results were in the image. But there sure are a lot of them. So points to IEF for easy to read results and points to NetAnalysis for the volume of results.
Now I do not want you the reader to think I am knocking NetAnalysis because one of the results I often find important in a case is redirects which NetAnalysis explicitly calls out and IEF does not. [Editor's Note: IEF v5.8 now recovers redirect and “leak” records.]
One area where the two provide similar breakdowns is the reporting of IE InPrivate Browsing hits. IEF calls the results IE InPrivate/Recovery URLs where NetAnalysis calls the results “privacie”. For My test image IEF reported 2578 hits and NetAnalysis reported, well, a bunch because it does not provide a count of hits. After performing a bit of page counting I found NetAnalysis reported 9128 hits. So did NetAnalysis really find 6000+ more hits? Probably not 6000+, but maybe more (or maybe less), it is really difficult to tell. Where IEF reports the individual URL hits, NetAnalysis gives perhaps what can be described as a more granular break down and lists every CSS, JS, GIF, PNG, JPG, and on and on. [Editor's Note: The InPrivate records recovered by IEF are actual web visits from InPrivate mode (or from IE Recovery records), while the PrivacIE records NetAnalysis recovers (and now supported in IEF v5.8) are IE InPrivate Filtering records (from regular browsing).]
I think this shows just how different tools are and how dangerous it is to just compare for example the total number of hits a tool reports. I think some of the recent court cases in the U.S. have shown what a debacle it can become when one tool is pitted against another. (How many times did that search for “chloroform” really occur?)
All of this begs the question, Is IEF the best tool in the marketplace for finding remnants of Internet use? While I cannot say it is the best for each individual artifact, I find that for the cost IEF can find, classify, and report on a wide variety of Internet artifacts in a relatively quick manner. IEF does a great job (far better than the big forensic suites) and if an examiner does work that requires the examination of Internet artifacts, deserves a place in their toolbox.
IEF 5.8 Addendum
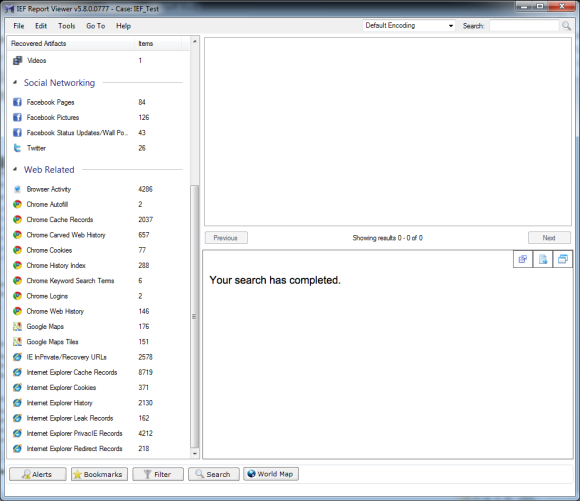
Magnet Forensic continues to push forward with changes to IEF. As seen in the following screen shots, there are several new artifacts IEF finds including new items in Chat, Cloud, Media, and Google Maps.

As shown in the IEF Report Viewer, Google Maps (Queries, Maps, and Tiles), Facebook Photos, and Web Videos are all new artifacts.
In addition to the standard file time information, the video artifact function appears to take a screen shot every 0:06 and also appears to calculate a “Skin Tone Percentage”. One thing I found disconcerting is the “Tags” found by IEF, because they are certainly not part of the metadata of the video.
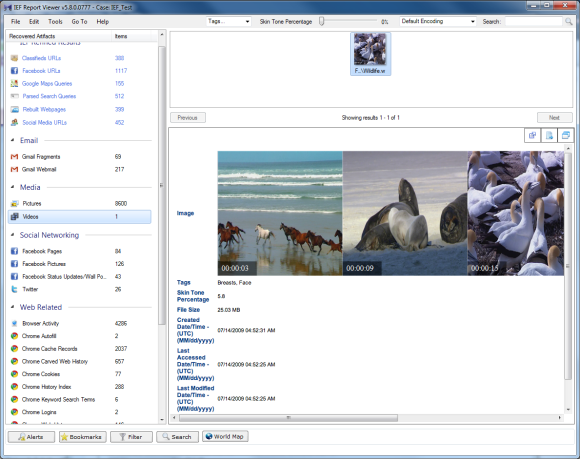
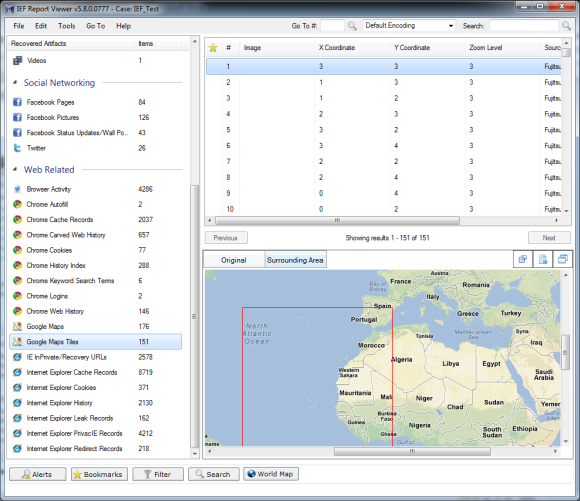
Google Maps and Google Maps Tiles are also new. And while I found almost all of the results in Google Maps to be relevant hits, there were some oddities. For example one of the hits was for the Windows 7 Compatibility Online Check and another for Yahoo Mail Help.
As shown below the tiles can show the original information including X and Y coordinates, but the Surrounding Area view is probably more helpful for many.
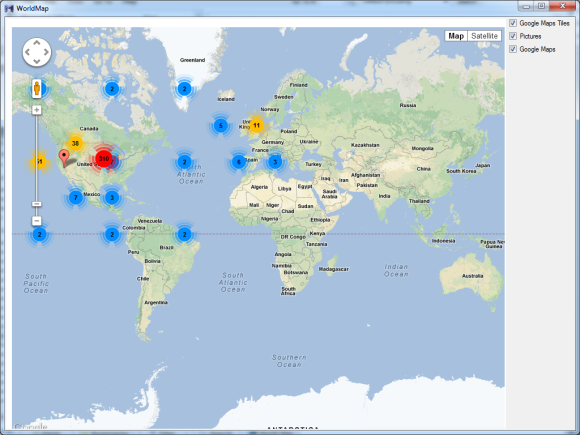
Clicking on the World Map button will plot all Google Maps, Google Maps Tiles, and picture coordinates on a world map for artifacts that have coordinates, creating clusters where a large number of plotted points exist.
A final thought. As IEF recovers more and more artifacts, I believe there is a need for more documentation about what artifacts are recovered, how the artifacts are recovered, and how the artifact is parsed (i.e., where did IEF get the Tag information?)
Looking at the example of the Tags for video files, there is no information about Tags in the Help file, so it would be impossible to say in a report how that information relates to the video. Another example is the InPrivate browsing information. While there is some documentation in the Help file it contains slightly different information from what the people at Magnet Forensics provided in their response to this review.
While it may seem a minor point, we tend to be in a profession that requires precision and knowing what a tool is doing is important. While hitting the “find evidence” button gives many of us a chuckle (and probably makes those that deride “Nintendo Forensics” cringe), we do have to defend our work and there is no way to defend something we cannot document.
This review can be discussed here.















