From FileVault To T2: How To Deal With Native Apple Encryption
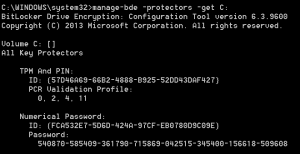
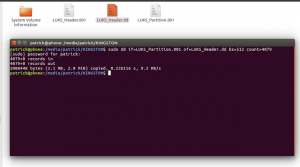
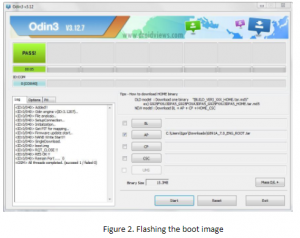
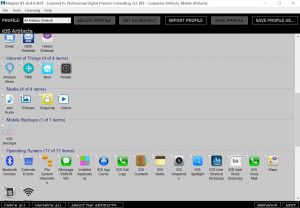
While Apple’s commitment to user privacy and security remains their priority, the field of computer forensics faces a solid challenge when it comes to extracting evidence from encrypted Apple devices.
This article provides comprehensive insights into Apple’s native encryption, covering… Read more