by Oleg Skulkin & Igor Shorokhov
The release of Android Nougat has brought new challenges to mobile forensic examiners: the smartphones running this version most likely have encrypted partitions with users’ data, their bootloaders are locked and classic custom recovery acquisition, which is widely used especially for Samsung smartphones, may not work anymore. But thankfully, things are not always this bad for the examiners. From time to time we find some interesting and original ways to extract data on the physical level from the smartphones we examine. And of course it’s very important to share the knowledge, so we decided to show you a way to perform a physical acquisition of a Samsung Galaxy S7 smartphone running Android 7.0.
The most challenging part of the acquisition process of this device is that it has an encrypted user data partition, and this is the most important part of the smartphone’s memory, as it contains user-created content, so even if we perform a chip-off extraction, we’ll get a quite useless image.
The method we are going to use is pretty like the custom recovery method with one exception – there is no custom recovery. And yes, this method works for bootloader locked devices!
You will need:
- a modified version of ODIN
- an engineering boot image
- rooting script and files
- luck
Let’s go!
- Put the device in the Download mode
- Start modified ODIN on your workstation
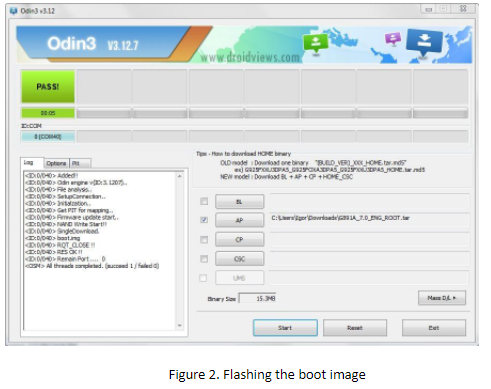
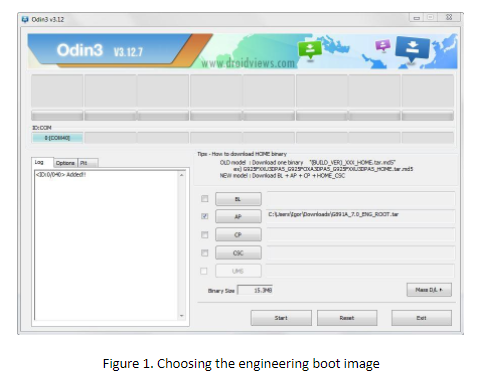
- Connect the device to your workstation and choose the appropriate boot image, look at the following figure:
4. Click ‘Start’ and wait till the process is finished. There is some magic: if there is a passcode, flashing this boot image resets it. So you can enable USB-debugging now.
5. Unpack the files for rooting and start ‘root.bat’. Now the smartphone is rooted and ready for physical acquisition.
We are going to use Magnet ACQUIRE to image the phone, but you can use the tool of your choice.
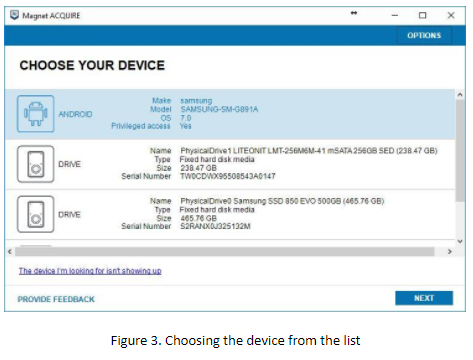
Start ACQUIRE and choose the right device. As you can see in the figure, our device has privileged access. What does that mean? It’s rooted and ACQUIRE detects it.
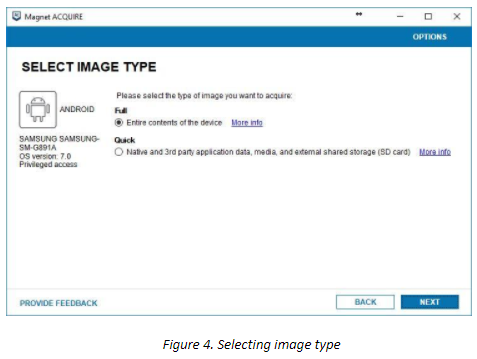
As our device has privileged access, we can choose ‘Full’ image type and get the entire contents of the smartphone – the physical image.
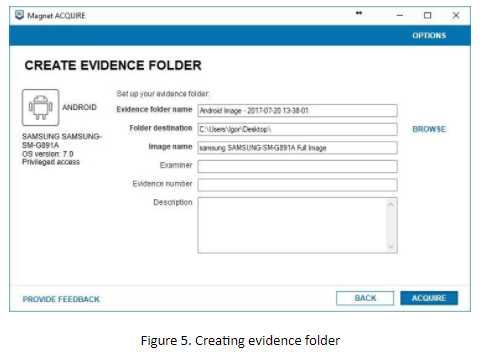
Finally choose the destination folder and image name, and fill in other available fields. Click the ‘ACQUIRE’ button and the imaging process will start.
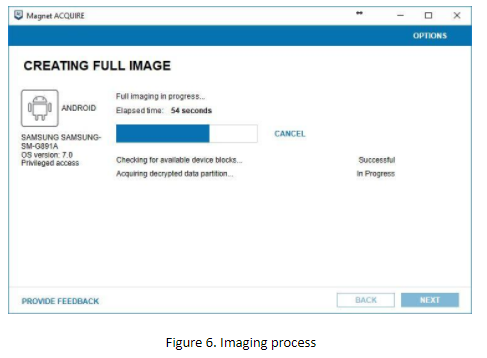
As you can see on figure 6, ACQUIRE is imaging a decrypted (!) data partition.
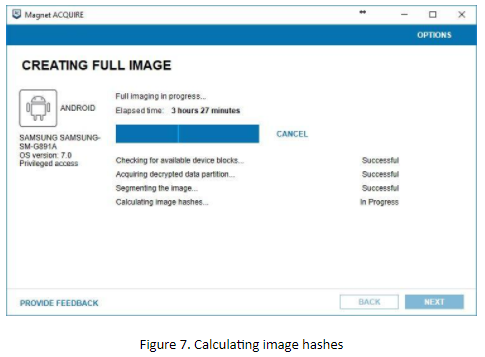
In our case, it took 3 hours and 27 minutes to create the image (without calculating image hashes).
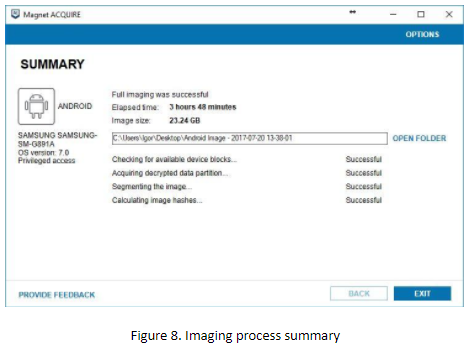
The whole process took 3 hours and 48 minutes – we got a 23.24 GB SM-G891A image.
Let’s make sure it’s really decrypted and process it with Magnet AXIOM.
First, start AXIOM Process and create a new case.
Choose the evidence source and artifacts type you want AXIOM to extract. As we are dealing with a smartphone image, we’ve chosen all mobile artifacts.
Click “ANALYZE EVIDENCE” button to start processing.
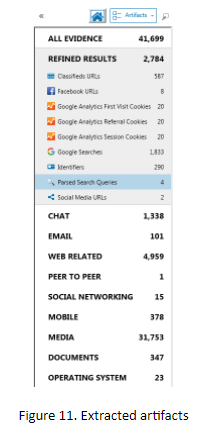
Once the image is processed, you’ll see that it’s really decrypted: we have lots of different forensic artifacts extracted by AXIOM, as shown in figure 11.
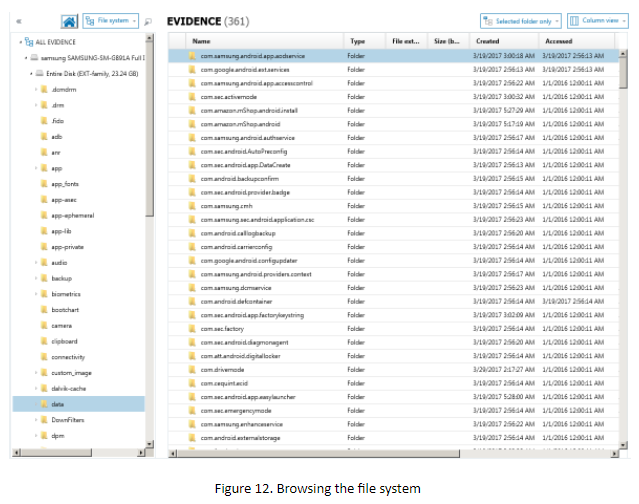
If you change Artifacts view to File System view, you can browse the file system and see once again that the image isn’t encrypted.
As you can see, sometimes it is quite useful to spend more time on research, as it can help to find new ways of physical imaging even for new devices with built-in anti-forensic technologies. Of course, the demonstrated technique isn’t as forensically sound as we would like it to be, but it’s better than trivial logical acquisition. Don’t forget to document everything you do thoroughly, especially dealing with non-standard acquisition techniques.
About the authors
Oleg Skulkin, MCFE, ACE, is a digital forensic examiner from Sochi, Russia. He is the author of Windows Forensics Cookbook (with Scar de Courcier) and Cyber Forensicator blog (with Igor Mikhaylov).
Igor Shorokhov, MCFE, ACE, OSFCE, is Chief Information Officer at Digital Forensics Corp.


















In step 4, you state:
“if there is a passcode, flashing this boot image resets it.”
To be clear, you are saying if the device has a passcode (and in my experience this is increasing true), this process will reset the _user data_ partition, correct?
Thx.
We used this method for 2 passcode-protected S7 devices, and no, flashing this boot image resets the passcode, but doesn’t reset the userdata partition.
Thx Oleg, super helpful and great content.
I have tried several times to complete this process and each time it fails. Need help!!!
Hi Bill! What’s wrong?
I can not root a Samsung G930T version 7.0 (US). I have followed the instructions and I always get a “fail”
I can send you a screen shot if I can send one on here or give me an email
Bill, you need another boot image, because you have different model, check XDA Developers to find it.
Does the boot file work for a SM-G935F or is it just for SM-G891A?
I thought that maybe the answer but didn’t know where else to look. Thanks for the info.
What is the patch Android installed in the phone you used for this experiment?
Can you repeat this experiment with a SM-G935F with a new patch?
Thank you
Oleg, is there a solution for sm-g930f or sm-g935f?
Great content and thanks a lot for sharing!
hi guys~~ thanks…
um.. Can I use this image on another model?
hi 🙂
Did you modify the Odin program? Or is it just the 3.12.7 version?
and.. Did you modify the boot.img??
How do I use it for other models??!!………
plz… 🙂
Once a android phone is rooted, can I get a decrypted image from any android phone?
Hellio,
is there solution for SM-G935F?
Thanks
Boss, excellent content. Is there any way to get magnet axiom for free? Or, is there any other tools that could be used? Thanks. Kalam
Downloads are gone…. Is it for the SM-G930F? It mean G891A, is this also a Samsung S7?
You need boot image for SM-G930F model
Example with SM-G935F
https://www.youtube.com/watch?v=2KsCBQ-aOjM&feature=youtu.be
A smartphone running Android 7 is really great becasue after the release of the Nogut the full view of android has been changed becasue of it new awesome features. I have loved the OS very much for its awesome features.
You write “There is some magic: if there is a passcode, flashing this boot image resets it.”
What if the phone is additionally secured via password before booting like described here https://www.androidexplained.com/galaxy-s7-enable-encryption/ ?
As far as I understand https://source.android.com/security/encryption/full-disk there is no “default_password” anymore and thus userdata can’t be read by this method.
Apologies for bumping an old blog, but I am having some issues.
I am able to follow the first section. where I download the image. on reboot though it still asks for a pin.
I am not sure what screen to be in to run root.bat? downloads still?
this is an encrypted device, so will this still work?
thank you
B
in You will need:
the links beside odin are outdated, could you please upload again e.g. to androidfilehost?
And are root images also for other samsung, like J530F available?
kind regards