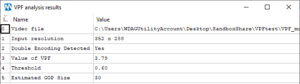
How to Search Images for Text Values Using OCR
Hello, everyone. Jordan here with the Oxygen Forensic training team. Today, I’m gonna show you how to search images for text values using optical character recognition. Let’s get started.
In today’s video, I’ll be discussing what OCR is and providing… Read more