The DFIR Lab team at Binalyze have their finger on the pulse of the cybersecurity ecosystem to ensure that our DRONE assisted compromise assessment module within AIR always includes the latest IOCs.
In addition they are always working on an ambitious roadmap of new features and enhanced capabilities to ensure that we are improving our product and providing new and innovative DFIR solutions that make their lives easier from the moment the investigation starts.
Read more to learn how Mitre Att&ck scanning and mapping can help you protect your organization from cyber threats. With DRONE, get detailed insights into the tactics and techniques used by attackers, and gain visibility into suspicious activity on your network.
We are delighted to say that in our latest release the DRONE module was upgraded to enhance its scanning capabilities by using the MITRE ATT&CK scanner. This addition aids the DFIR investigation by categorizing DRONE-identified IOCs and Malware against certain MITRE tactics and categories. This makes it even quicker and easier to understand the intent of certain IOCs and start appropriate remediation.
What Exactly is MITRE ATT&CK?

MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques, based on real-world observations.
The ATT&CK knowledge base is used as the foundation for the development of specific threat models and methodologies. These cover the private sector, government organizations, and in the cybersecurity product and service communities.
The idea behind the creation of MITRE ATT&CK, was to help tackle the ever evolving threats faced every day — by bringing communities together to develop more effective cybersecurity solutions. ATT&CK is an open platform and immediately we could see a massive opportunity in bringing this knowledge into AIR.
What is the Mitre Att&ck Scanner Feature?
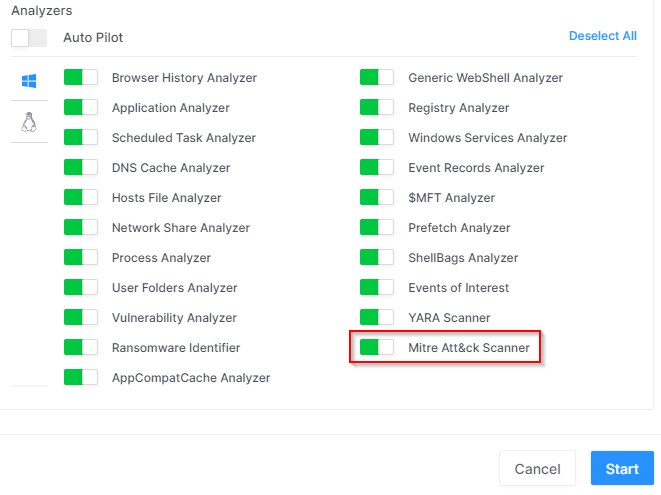
From version 2.9.0 the MITRE ATT&CK scanner has been added to the available analyzers built into DRONE.
The integration of this new analyzer delivers additional benefits of additional YARA rules for detecting potential Indicators of Compromise (IoC) or TTPs (Tactics, Techniques and Procedures).
These rules come embedded into DRONE as part of the new analyzer. As at January 2023, we’re supporting more than 300 new generic rules, with additional rules being added constantly by the DFIR lab team.
The MITRE ATT&CK scanner is now yet another way of piecing together critical information as part of an investigation using DRONE.
Thanks to the exhaustive R&D work carried out by our world-class DFIR Lab team, the DRONE MITRE ATT&CK scanner combines a high level of detection rate for malicious indicators with an extremely low false positive rate.
Our obsession over lightning fast performance ensures the MITRE ATT&CK scanner further helps analysts and investigators to speed up their investigations process, whilst providing them with clear signposting around intent.
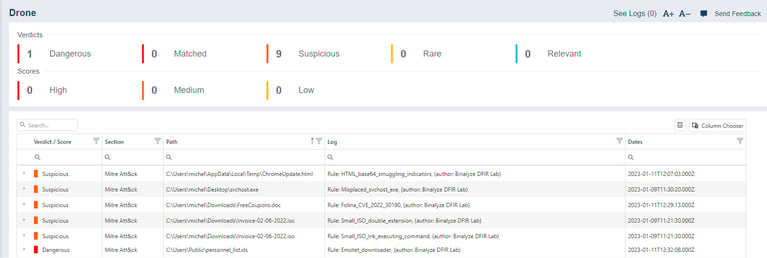
Image of the case report
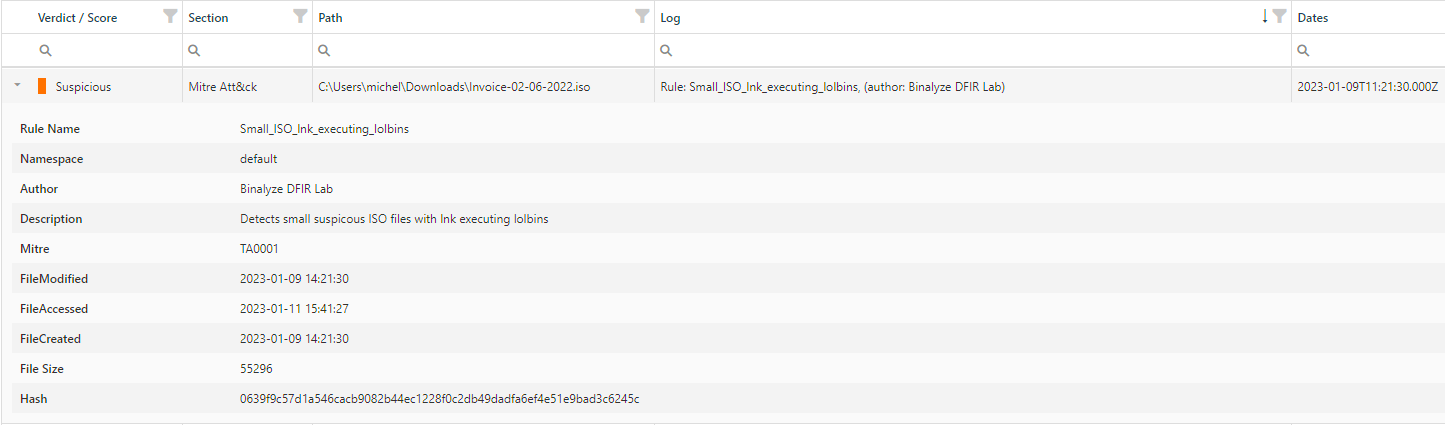
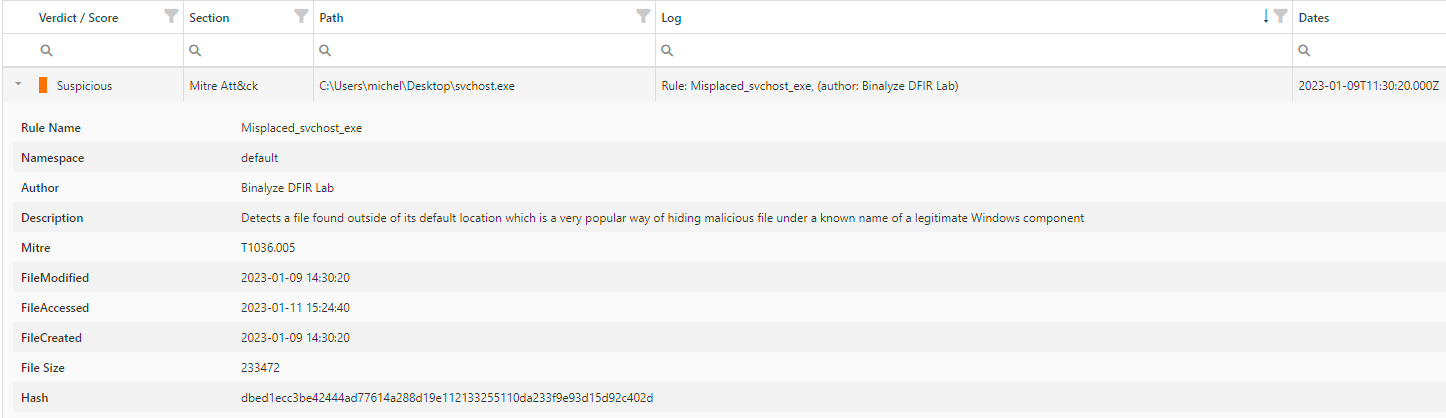
Detailed information for each verdict
What is the Benefit of the MITRE ATT&CK Scanner to AIR Users?
Looking at the DFIR process as a whole, with the MITRE ATT&CK scanner in place we’re now actively developing yet more ways to give analysts key pointers and direct signposting as to where and how any breaches may have occurred. As with all parts of AIR, we’ll continue to enhance this capability over time – helping to further reduce the time needed to complete these tasks and shortening overall investigation times and potential for loss of data and reputations.
With our comprehensive analyzers, customers will see the attack stages, the footprints of any attackers, and which of the Tactics in MITRE ATT&CK were used.
By using this option, they’ll have a greater understanding of what the attackers intentions were and what they’ve done in their systems. We then have three verdict levels representing how serious any discovered threat is.
Threat levels:
- Dangerous – a dangerous verdict will indicate specific malware families or TTPs that are only ever used by malware
- Suspicious – a suspicious verdict aims to highlight indicators that are more than likely to be used for malicious rather than legitimate purposes.
- Relevant – relevant is our lowest verdict level. This level is intended to show indicators that we can’t say for sure are malicious until they are thoroughly analyzed. A good example would be either a password protected archive or macro enabled document. These file types are typically used for legitimate purposes but in recent times have gained popularity amongst bad actors for exploitation
What Problem Does this Solve for AIR Customers?
During your analysis, the scanner will quickly and easily show you any easily compromised machines amongst your total estate of hundreds or thousands of endpoint machines. You’ll never again have to spend your time hunting for a needle in a haystack.
This addition to AIR, it’s yet another example of us looking at our customer’s pain points and proactively giving them the right tools to free up time to focus on other key parts of the DFIR investigation process.
To find out more about AIR and how it can help improve your DFIR case management, why not sign up for a free 14 day trial.















