In the pantheon of computer forensic analysis, practitioners are often faced with many problems that require innovative solutions. Every case or incident presents us with new challenges, new approaches, new work-arounds and new exploits. For many years, the practice of utilizing virtual computing machines in forensic analysis has been an accepted practice to help re-create and document the user environment as the suspect or target of an investigation would have used it. As many in the field will no doubt agree, the tools for effectively creating, using and documenting a virtual computer machine from a forensic image file have met with varied success. Due to the *virtual* instability in the forensic computing market, UK-based MD5 has developed a robust and user-friendly tool: Virtual Forensic Computing (VFC) by MD5.

System Requirements
As with any tool, VFC comes with specific system requirements that are recommended as a minimum. So, what do you need to run VFC on your system? The system requirements are listed below, but as we’ll detail later in this review, the flexibility of your system will also help a great deal in how effective your use of VFC will be.
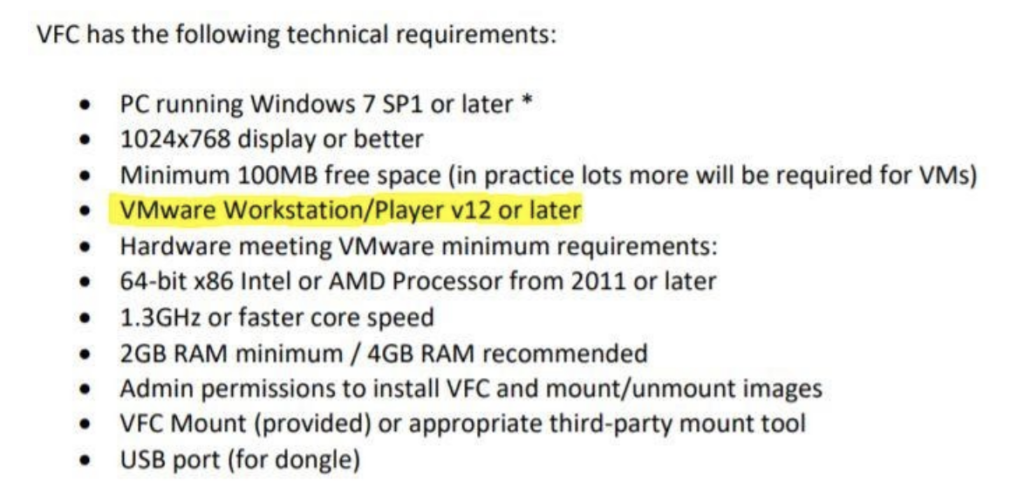
These system requirements were taken directly from the VFC quick-start guide. Please note that use of VFC requires installation and licensing for VMWare on your system as well as highlighted above.
For our testing of VFC by MD5, we utilized two raw (DD) images – one Windows XP system and one Windows 10 system.
Step 1: Image Mounting
In order to use most (or all) virtual systems, you will first need to locate and mount the image(s) you wish to analyze. VFC comes equipped with a disk or image mounting utility called VFC Mount that makes this process easy. Simply find the disk attached to your forensic analysis system that contains the image(s) you’d like to mount and tell VFC Mount which image it is. VFC does the rest for you, quickly and automatically, including detection of the operating system of your write-blocked image.
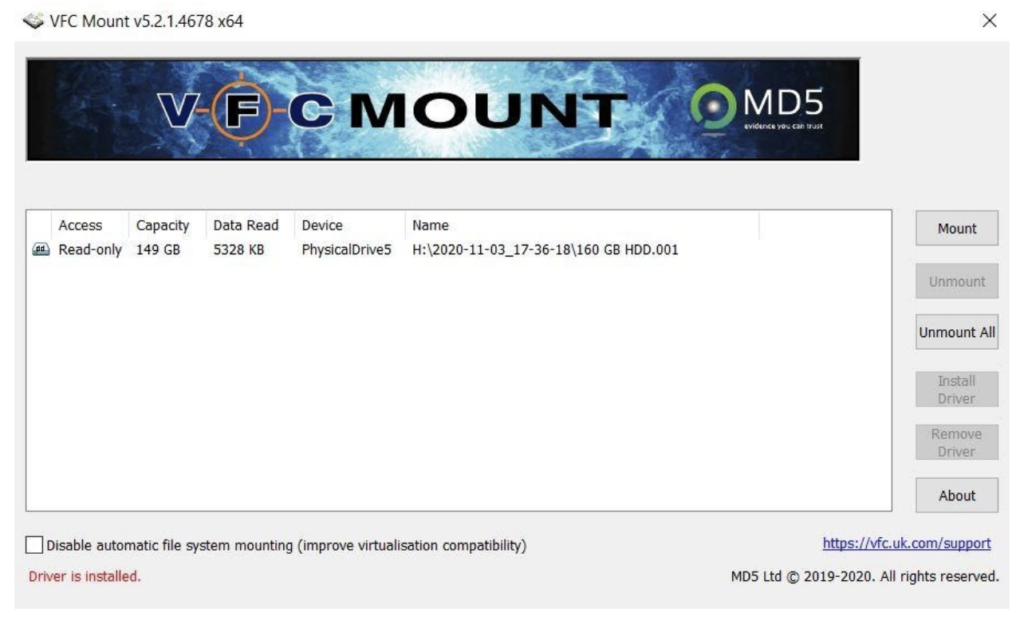
Naturally, once the image is mounted, you’ll also be presented with the disk in Windows Explorer, which you can browse on your local machine as the case parameters dictate.
Starting Up Your Virtual Forensic Machine
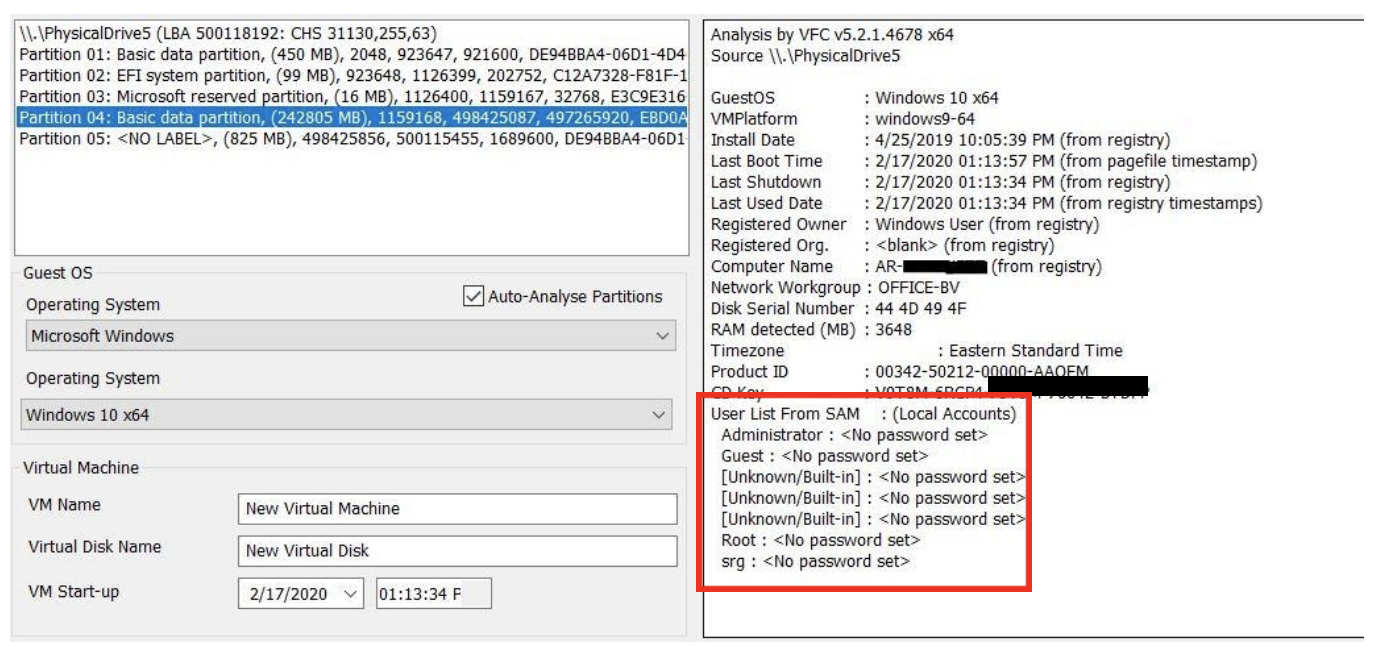
After mounting your image, one of the nice initial features in VFC is the immediate display of your virtual system’s properties, mainly derived from the Windows registry. This quick snapshot of your system is really useful, not only for general knowledge, but for also for basic documentation. Here are our Windows 10 test system properties as presented in VFC:
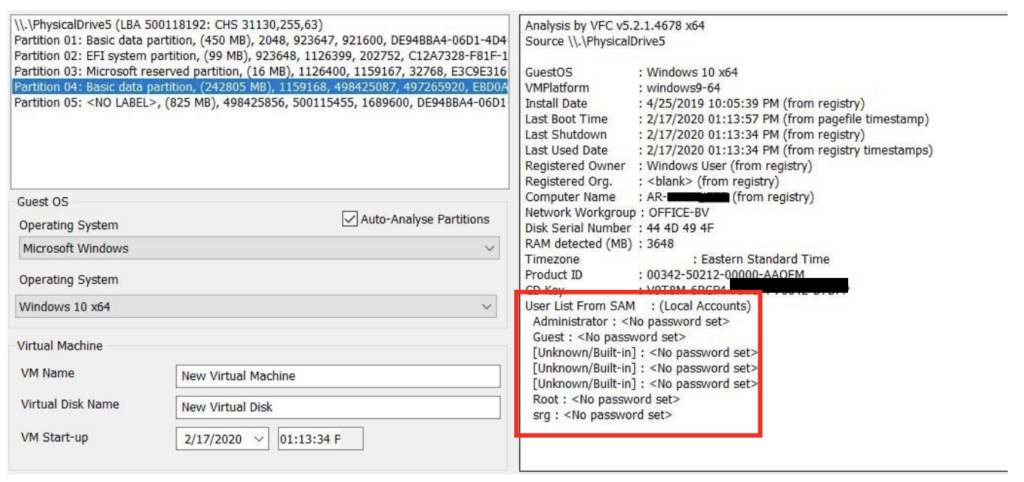
Note that the user accounts and their password status are included in this quick snapshot, but this should always be validated. VFC also allows you to set the virtual machine date and time, which is a nice feature when documenting your analysis and making screen captures of your findings.
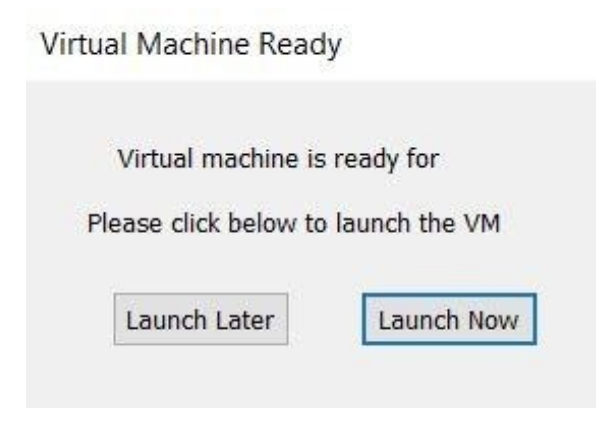
At this point, to start up our virtual machine, we simply tell VFC to launch and it fires up simply and effectively.
Generic Password Reset
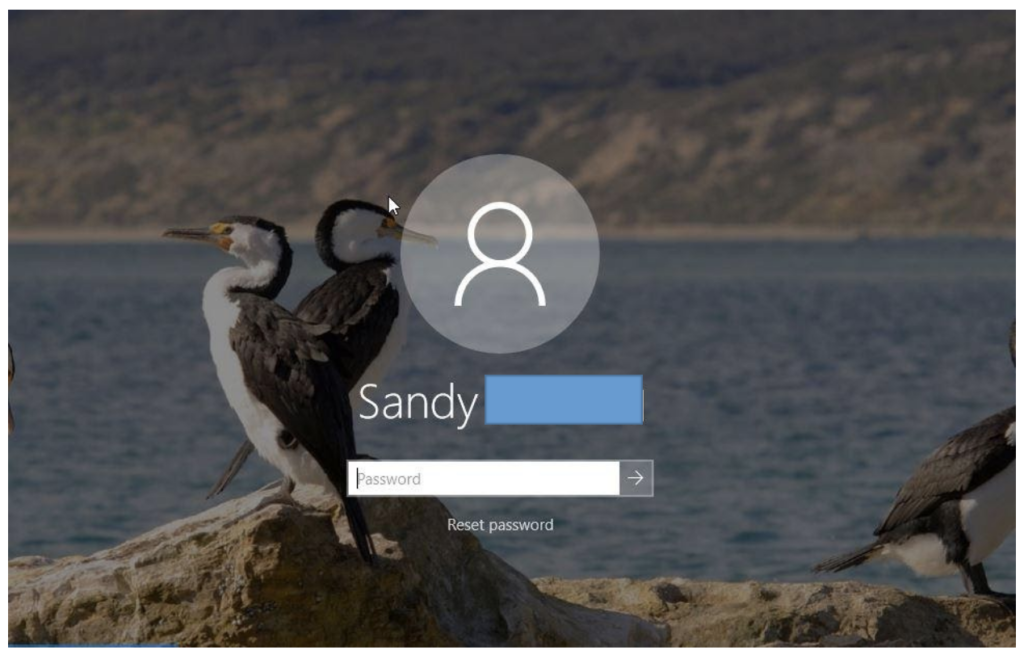
Most users secure their systems with a password. As such, VFC comes with a built-in password bypass utility that is user friendly, fast and (amazingly) actually works! When the virtual machine starts up, we are presented with a command line-like window asking if we’d like to use this utility or simply minimize the window. Naturally, if the account is not password-protected, we have no need for this. But in our Windows 10 test, even though the system properties reported our main user account as not being password protected, upon startup of the VM, it was. Fortunately, we have a tool within VFC to deal with this issue.
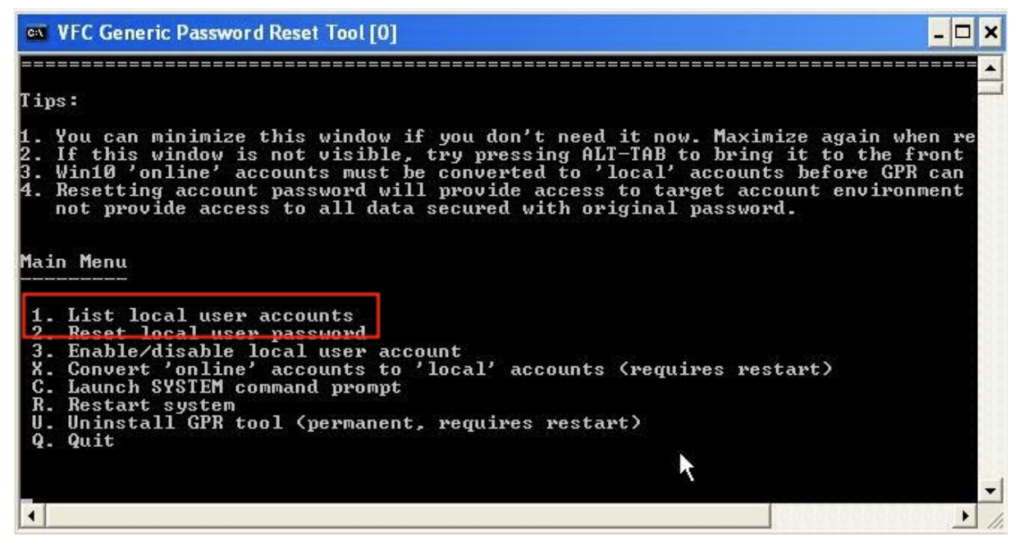
The Generic Password Reset Tool menu requires us to tell VFC which user account password we’d like to reset, then choose what password we’d like to use. If we have forgotten or didn’t note the list of user accounts, we can get a listing of that prior to selection as well.
When we selected option 2, we referred to our list of users. The only unique user was “srg”, so we told VFC that was the account password we wanted to reset and entered “1234” as the new account password when prompted. Then… voilà!
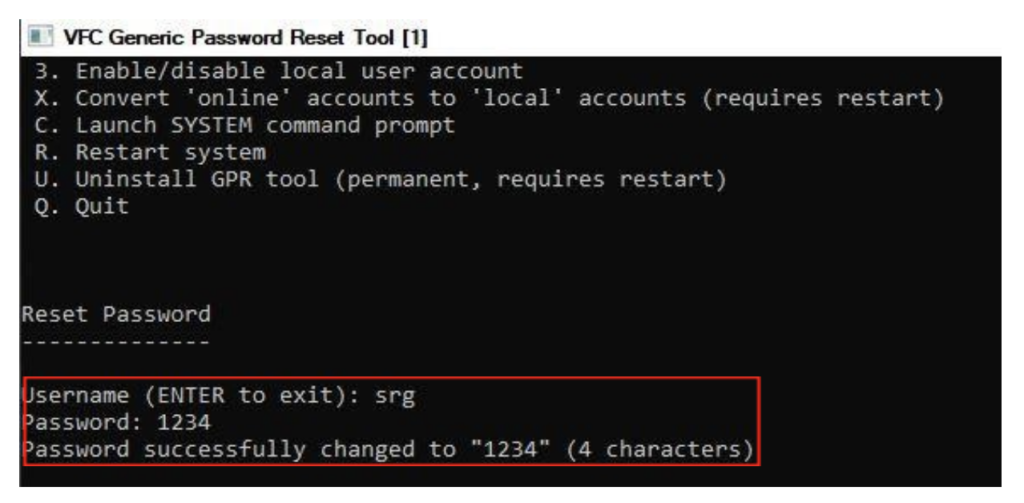
As soon as that was completed, we were able to log into the password-protected account using our new password with ease. This entire process was intuitive, easy-to-use and fast!
VFC User Options And Experience
As stated earlier, VFC requires use of VMWare to function, so many of the user options that are available to us are associated with VMWare, not VFC. These include native screen captures; the ability to disregard or include external devices; and network settings. However, VFC offers some case-specific customization for use as well. One of these areas is the settings on our virtual machine. VFC allows us the ability to customize options such as processor and RAM use, as well as other areas to help optimize the use of our new virtual computer during analysis.
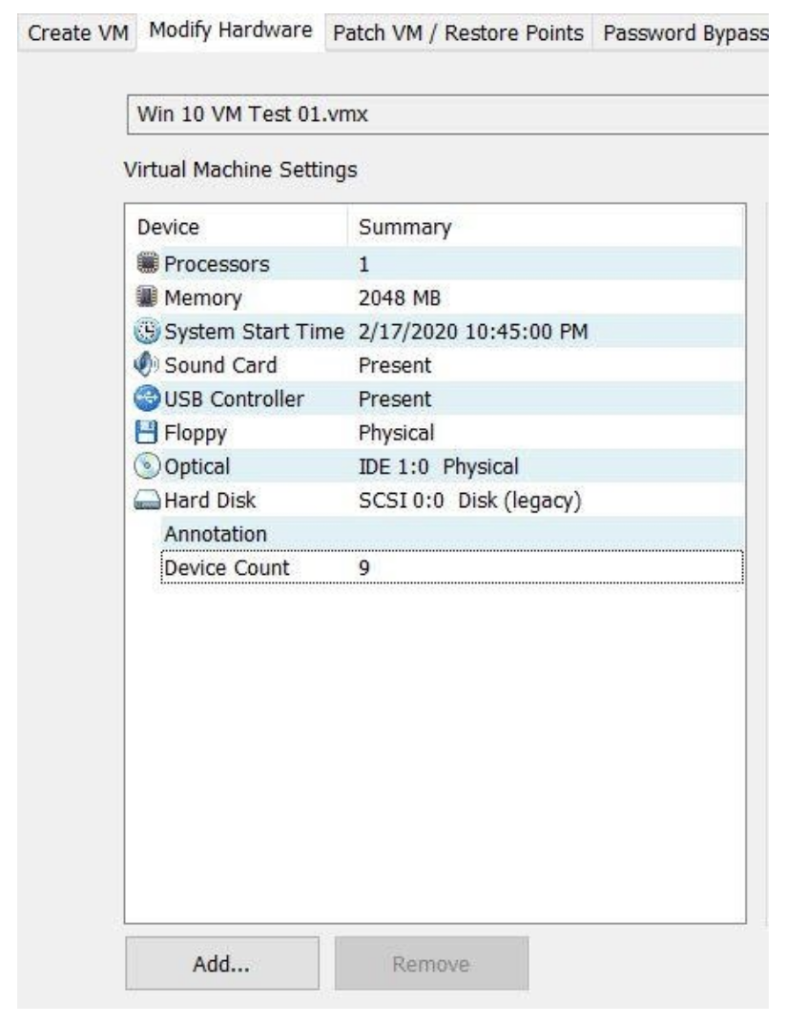
Other customizable options include the ability to auto-detect the operating system of your image, screen resolution for your VM, and default RAM usage. If you use VFC regularly in your analysis, you can also save these settings and configurations so you can use them across the board in all forensic analysis using VFC.
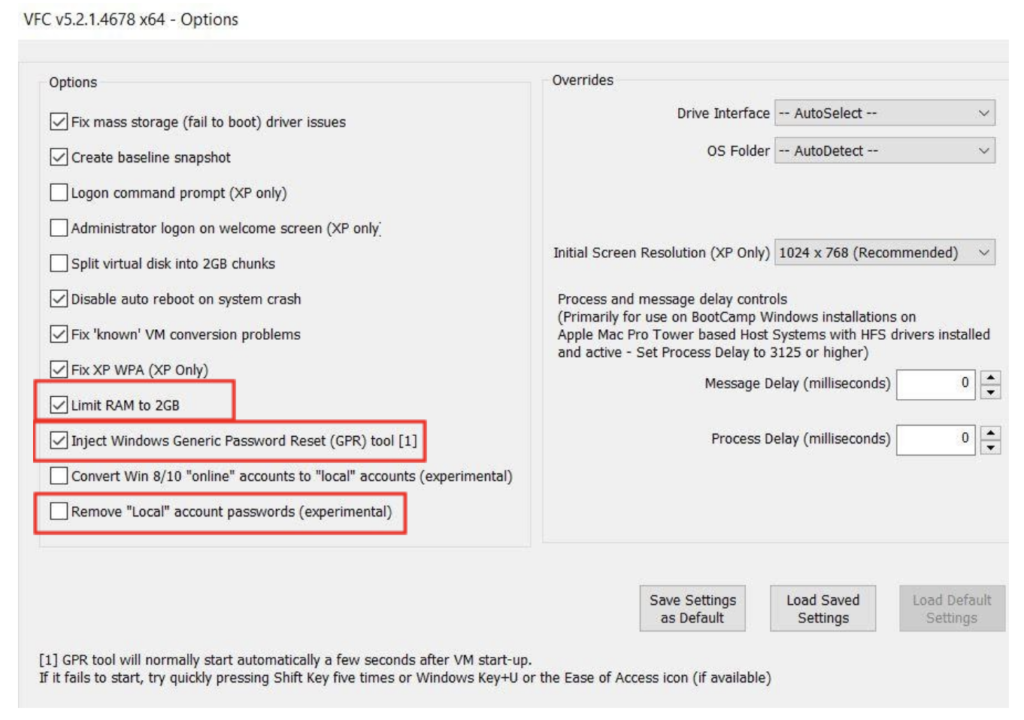
All of these options are built into VFC to ensure you can run your VM in the most optimal fashion possible for your particular case. With the inclusion of experimental features, we can conclude that the application development team for VFC at MD5 is hard at work adding additional functionality to the tool as well.
When you’re finished, shutting down VFC is as easy as shutting off your computer. The files associated with your virtual machine are saved in case you need to access them later and your image is un-mounted.
Conclusion
As digital forensic examiners, we’re always searching for the next best way to get the analysis done faster and more effectively. Much of the time, the concentration in our industry in this particular arena is focused on mobile devices. But Virtual Forensic Computing by MD5 has taken what has previously been a computer forensic practice that was met with moderate difficulty by some and made it simple to use, robust in functionality and effective in analysis. If your current virtual machine setup has you fiddling with coding and command line prompts that are cumbersome or don’t allow you the ability to customize your machine for maximum effectiveness, try out VFC by MD5. You may find it the solution to a problem you didn’t know you had!