Hold the phone… and the drone, and the GPS device, and the disk! Upon receiving MSAB’s software product XRY v9.4.3 and its compatible viewer, XAMN v6.1, we had full intentions of pulling out and dusting off a few of our test mobile devices (some that we knew the passwords and pins for and some that we did not) and attempting as many extractions as possible. We were pleasantly surprised when we saw that there was device support for over 34,000 devices. These devices range from disks, drones, GPS and media devices to mobile modems, phones, and SIM cards.
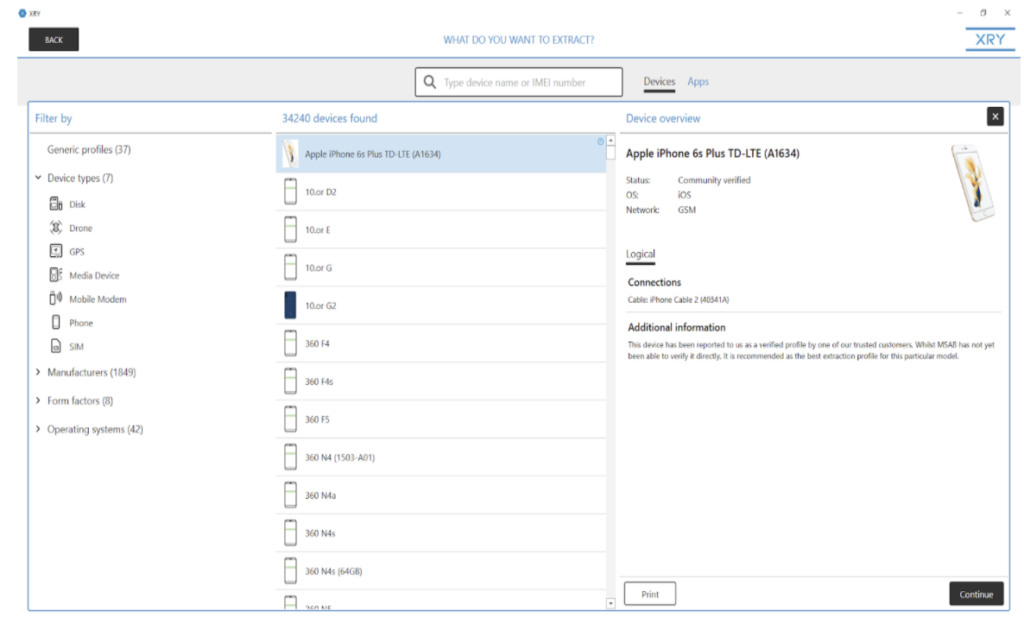
While we still only tested extractions on two mobile devices, an iPhone 6s Plus (A1634) and Samsung Galaxy S4 (SGH-I337), we did thoroughly browse the impressive selection of all of the available extraction options. If you are an XRY customer, a full list of supported devices can be found here. If not, you can request a copy of supported mobile devices from support@msab.com.
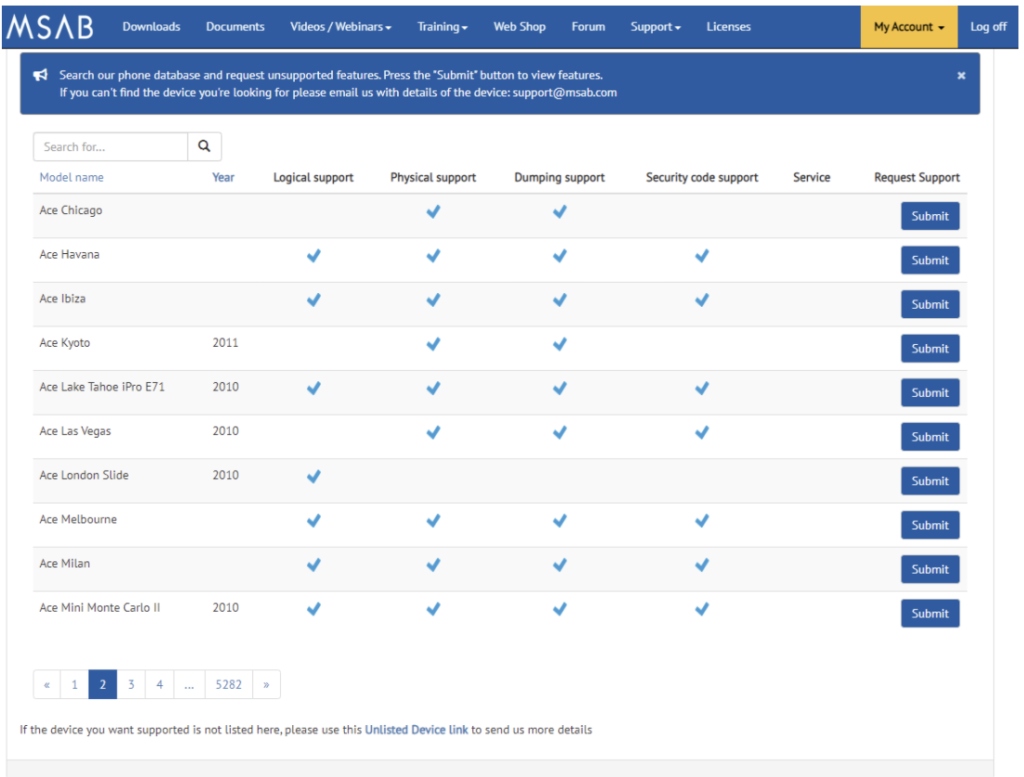
An example of the impressive selection is the over 20 different cloud account extraction options. Not only is there a tremendous amount of acquisition options, but also step-by-step guides on how to acquire these accounts, along with warnings written in red to alert the examiner of the necessary precautions that must be taken before acquiring a cloud account. Supported cloud extractions include:
- Box
- Create Token Option (Box, Dropbox, Facebook, Foursquare, Google, iCloud, iCloud Backup, LinkedIn, Microsoft Cloud, RunKeeper, Twitter, Yahoo)
- Dropbox
- Foursquare
- Google Takeout
- iCloud Backup
- iCloud
- Microsoft Cloud
- OkCupid
- RunKeeper
- Snapchat
- Telegram
- Viber
- Yahoo
Another really great feature is the option to choose the type of device you are looking to extract based on its form factor, a great way to narrow down your options while looking for the right extraction profile. Among the form factor options we have: Block, Clamshell, Flip, Glasses, Slider, Swivel, Touch, and Watch, all with accompanying pictures and arrows to help the examiner make their decision.
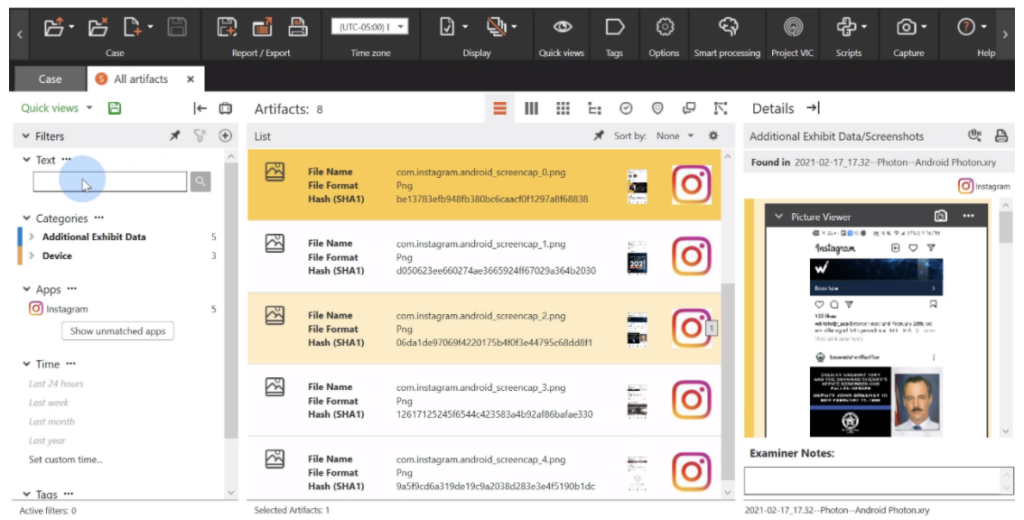
The final extraction method, an outstanding addition to the product, is the “Android Photon” extraction method. This handy feature allows the examiner to gather application data from the device, where Photon extracts and decodes the application data, such as chat threads, Instagram feeds, etc. and takes screenshots while it is extracting. As the examiner, you have the option to choose the number of screenshots you want to take of an entire feed or thread, where you can choose “All” contents down to a single screenshot. You also have the option to choose what direction you want XRY to scroll through the thread. And better yet, once loaded into XAMN and with the help of the integrated OCR functionality, you can search through the text of the feeds from the global search feature.
The following picture was obtained through a tutorial video provided by MSAB, as we did not attempt to test the Photon feature ourselves at this time.
As digital forensic investigators you are probably all too familiar with the intensity of resources that are required for many forensic software programs during the processing and indexing of artifacts. While XRY will no doubt work much more efficiently with increased performance factors such as more RAM, Core Processors, and an upgraded graphics card, it will work with the following minimum requirements, which can be found on MSAB’s Customer Portal FAQs page:
- Windows 8/10
- Intel 6th Generation (Core i3 or above) or equivalent
- 8GB RAM
- 500 GB HDD
- Screen Resolution: 1600×900
- Microsoft .NET Framework 4.7.2
iPhone 6s Plus (A1634) Extraction
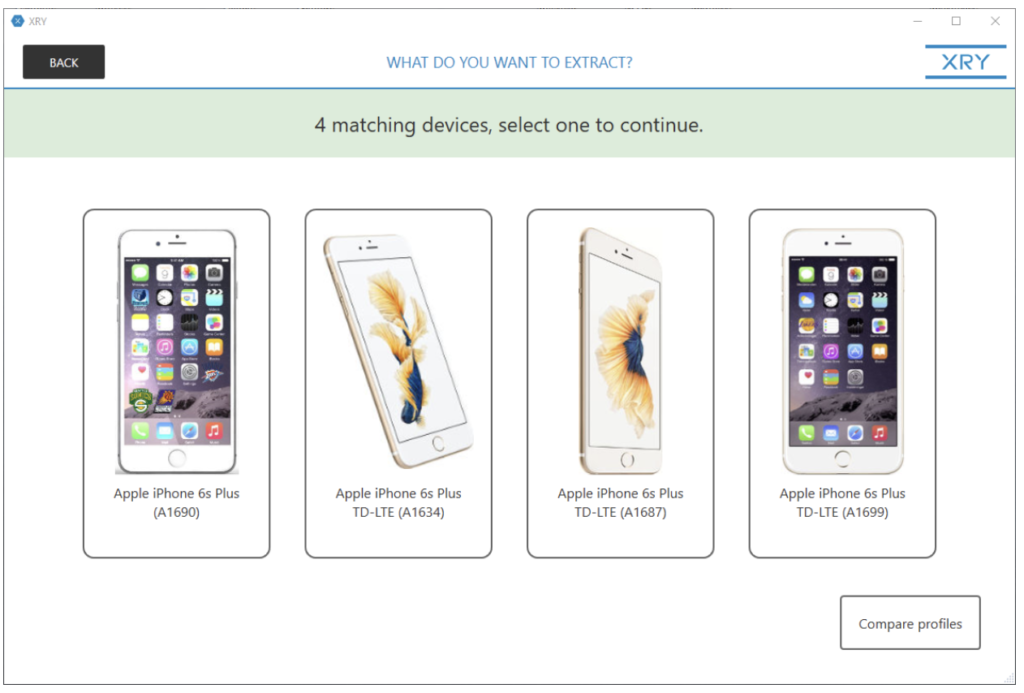
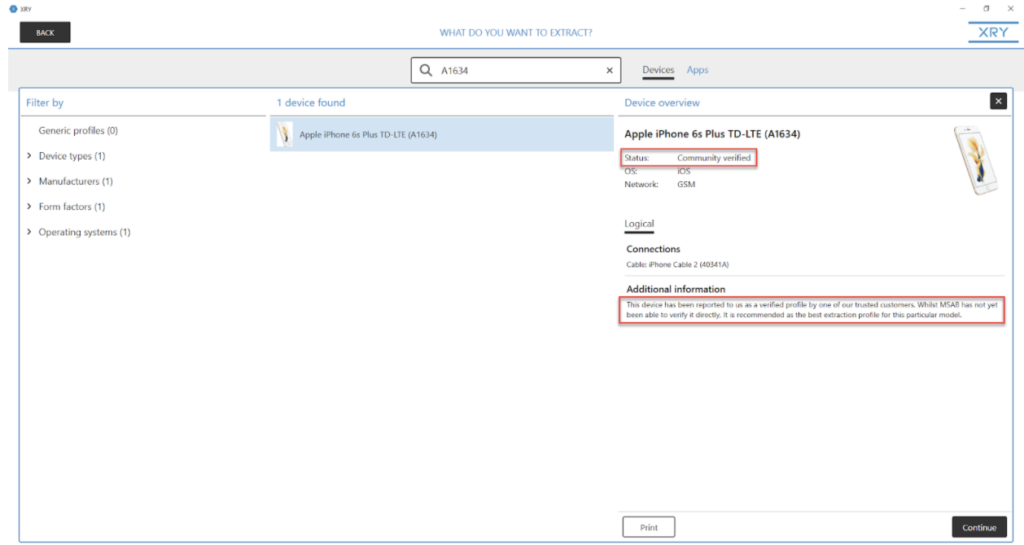
Each device within XRY has a general info pane with information such as recommended cable for connection, status of acquisition profile, OS, and carrier network. For this device, as shown below, the profile has been community verified as the best extraction profile for this particular model, meaning whilst it has not been verified directly by MSAB, it has been verified by one of their trusted customers.
This is a nice touch to give examiners a warm and fuzzy feeling when it comes to selecting the appropriate profile for your device, where sometimes selecting a generic profile may in fact give you more data than a profile designed for your specific device. It is a great way to show that profiles have been vetted and have been determined to be the best source for your acquisition.
While walking through the step-by-step guides of our initial acquisition, we noticed that we had the option to view pre-scanned data, a feature that attempts to pre-scan a device that has been plugged in to give the examiner an indication of the types of data resident on the device before they even begin their extraction. This is a great time saver for the examiner so they know what type of extraction may best suit their needs, without wasting time trying other extraction methods first.
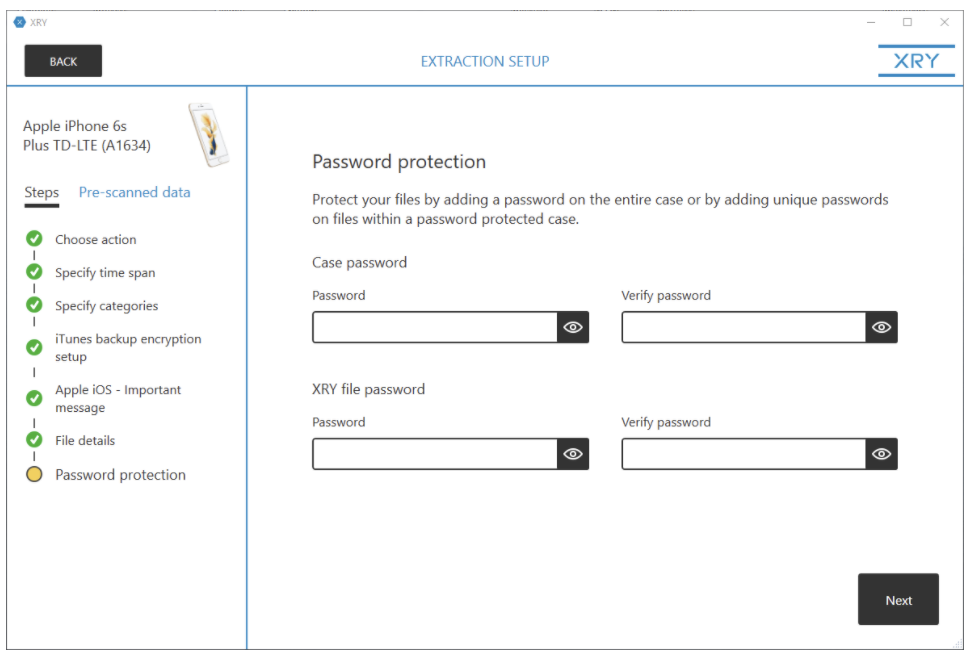
After we identified the timeframe we wanted to extract specific categories from such as calls, contacts, device data, media and more, we had the option to either encrypt our backup or not. (An encrypted backup will sometimes give the examiner the possibility to extract more data.) A warning to alert the user they need to trust the forensic workstation is also present, a helpful reminder to ensure the acquisition goes as planned. As we wrap up our initial extraction setup, we come to the final section labeled “Password Protection.” XRY gives us the option to password protect our case files as well as our XRY files. Way to go, MSAB!
Throughout the extraction we can watch XRY as it attempts to acquire the forensic artifacts from the device as well as keeping an eye on the status of the process with the built-in log viewer. The log viewer is quite intuitive and gives the examiner detailed information such as the index number, what module is being used, and whether or not it completed successfully, as well as the exact time a module and specific analysis took place.
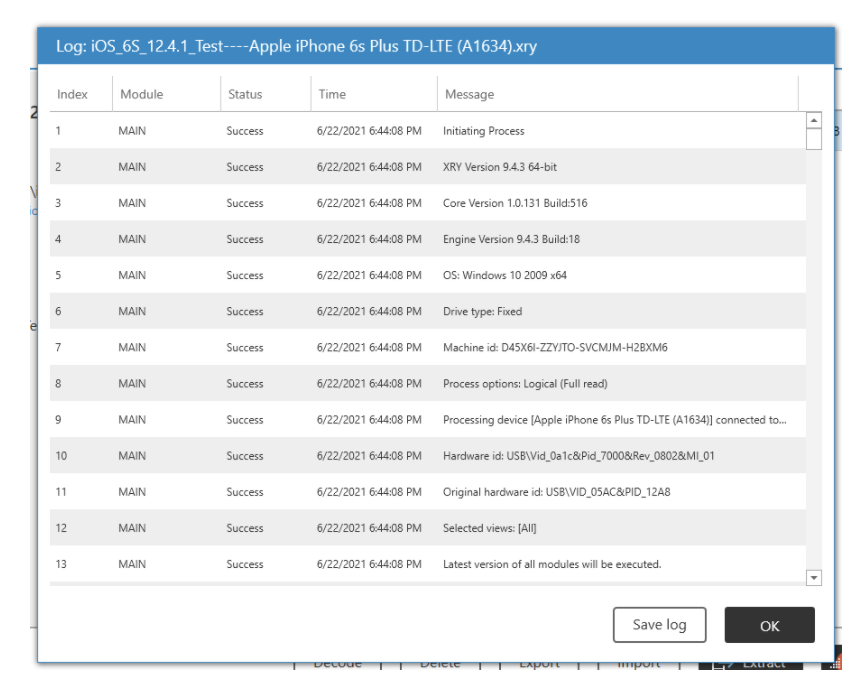
Upon the completion of our initial extraction, we are presented with a window that we can look through as a digital forensic examiner, to see if the information we hoped to gain from our acquisition is present before using time and resources to analyze our artifacts.
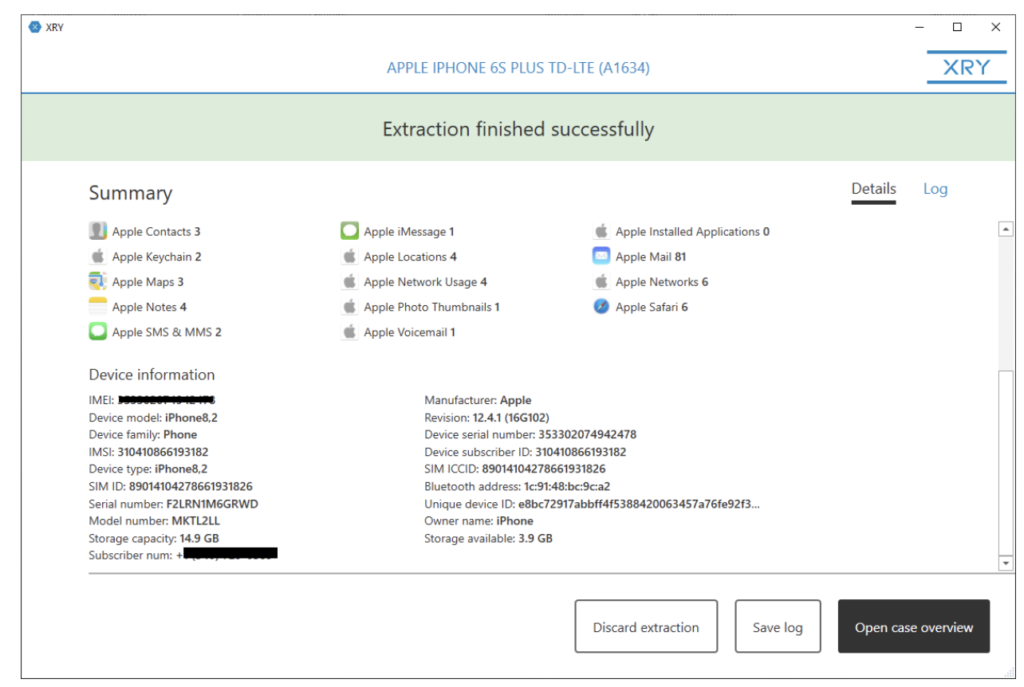
Once an extraction is complete within XRY, we are prompted with the Summary page. This is an extremely helpful feature for the examiner, as it not only gives us an idea of what was collected, but also the necessary device identifiers for our investigations. On this page, we can also choose to move forward and open case overview in XAMN and view and save our log files, or if the information that we had hoped to gain from the extraction is not present, we have the option to discard the extraction and start again.
Samsung Galaxy S4 (SGH-I337)
For this particular device, we wanted to see what kind of data and how many artifacts we could retrieve without knowing the PIN of the device. Upon launching XRY and selecting ‘Extract,’ using a generic Micro USB cable, we connected the S4 to our forensic workstation and waited for automatic device detection.
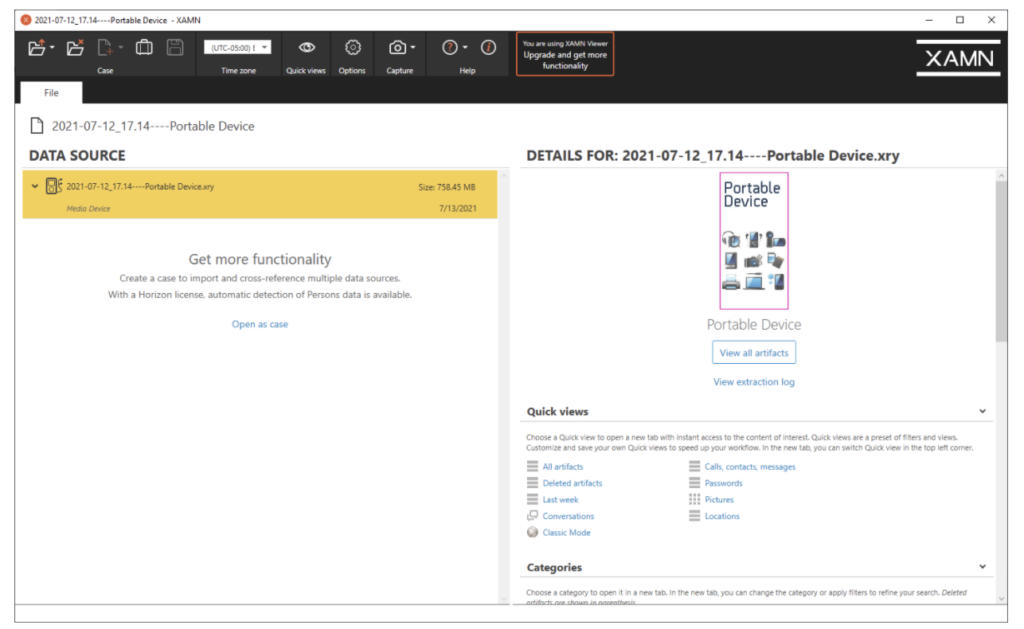
While we did not initially find our device profile automagically, we were presented with the “Portable Device” profile for extraction. The portable device profile allowed us to extract just under eight thousand artifacts to the device without the PIN! Win!
We then attempted to complete an extraction using the SGH-I337 profile, where we were able to extract a few device identifiers, but not nearly as much information as the portable device extraction, so we decided to focus our efforts here for the remainder of our XRY testing.
Let’s XAMN Our Artifacts
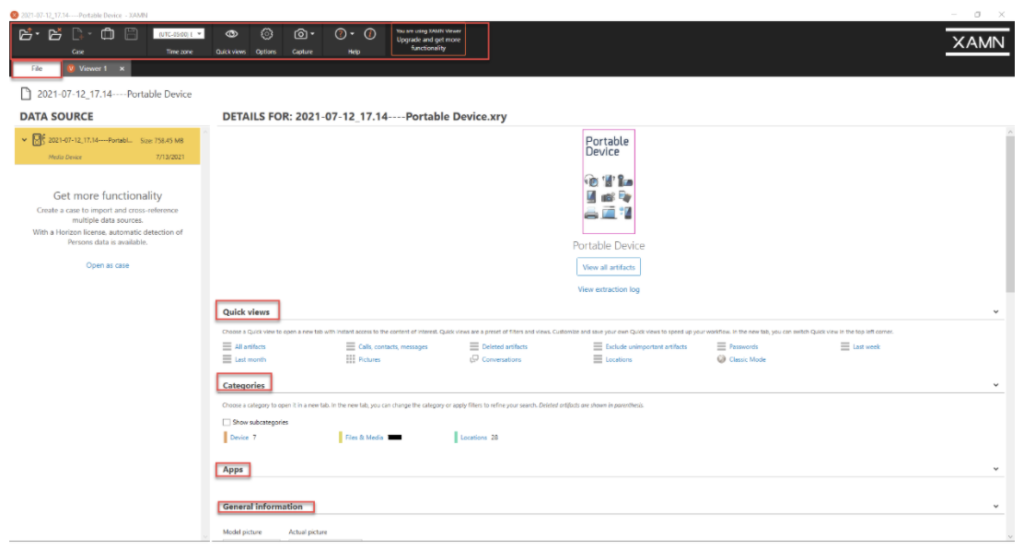
To begin, we took a look at the layout of XAMN. The color scheme, clear and concise naming standards for tabs, and extensive options made for an excellent first impression of XAMN. The main screen, upon loading an extraction into XAMN from XRY, presents a tab that is unable to be closed, called “File.”
The File tab can be looked at as a “Dashboard”, where an examiner can begin their investigation. It gives the examiner quick views, which are presented as: All Artifacts, Calls, Contacts, Messages, Deleted Artifacts, Passwords, Last Week, etc., which can be used to dive straight into the artifacts of interest rather than aimlessly browsing them. It also breaks down the different categories of artifacts that were discovered on the device, such as what applications are on the device, as well as general information regarding extraction and exhibit data.
Spread across the top of the XAMN interface, we are given an extensive number of administrative options which allow an examiner to open a case, close a case, import a case, create a new case, save a case, change the time zone for analysis purposes, change what artifacts are listed in quick views, capture a picture or video, search an online help page for XAMN customer support, and change the overall settings of XAMN with the Options setting.
We wanted to start this investigation by looking at some of the acquired artifacts to get a sense of how much of the data had geolocation information tied to it. What can sometimes be a daunting task with forensic acquisition tools is quickly achievable within MSAB’s XAMN viewer by selecting the artifacts that you want to examine and then viewing that data in the “Geographic” viewer, which filters out all of the selected artifacts containing geolocation data.
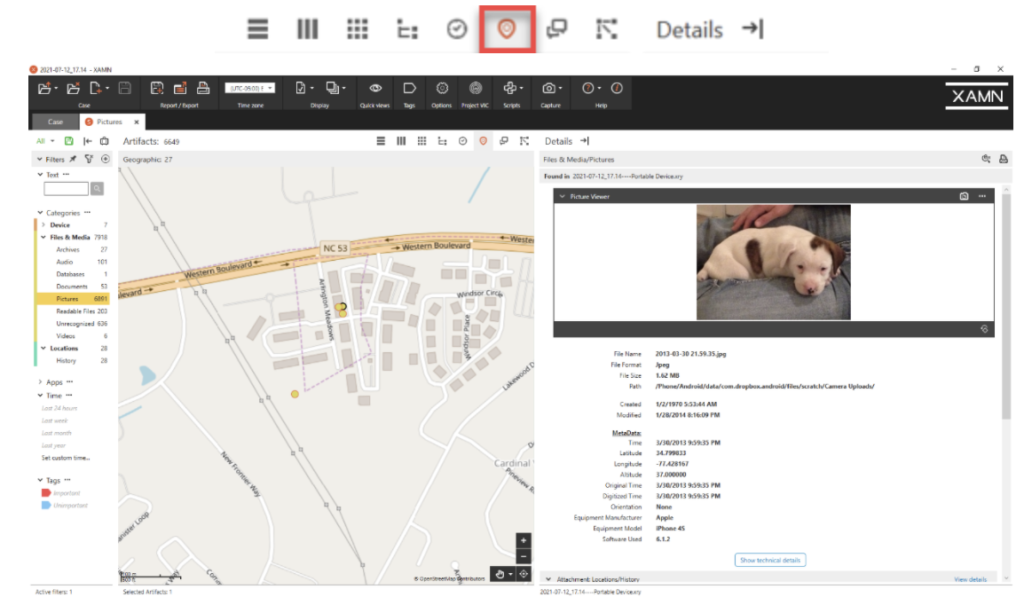
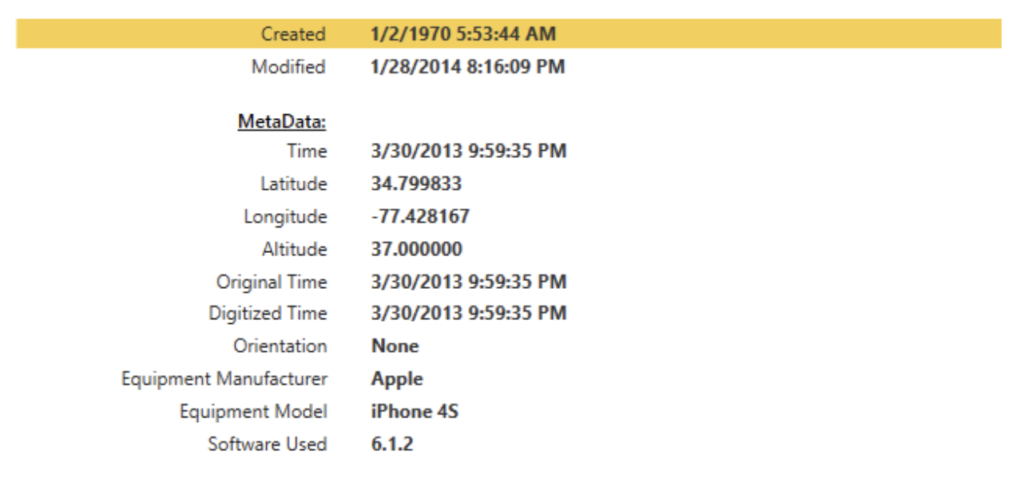
When selecting a specific artifact with geolocation data, we have the option to zoom in or out on the left-hand side of the interface on the online map segment and view the artifact of interest. If your forensic workstation is not connected to an internet connection, there is an option within the Options tab which allows for the download and installation of offline maps. This particular photograph of this adorable puppy has accompanying metadata, located on the right-hand side under the “Details” pane. This information includes: Created time, Modified time, Latitude/Longitude/Altitude, Manufacturer, Model, and Software version.
XRY does an outstanding job of scraping the data that was collected from the mobile device for the production of metadata in such a clean manner within the interface.
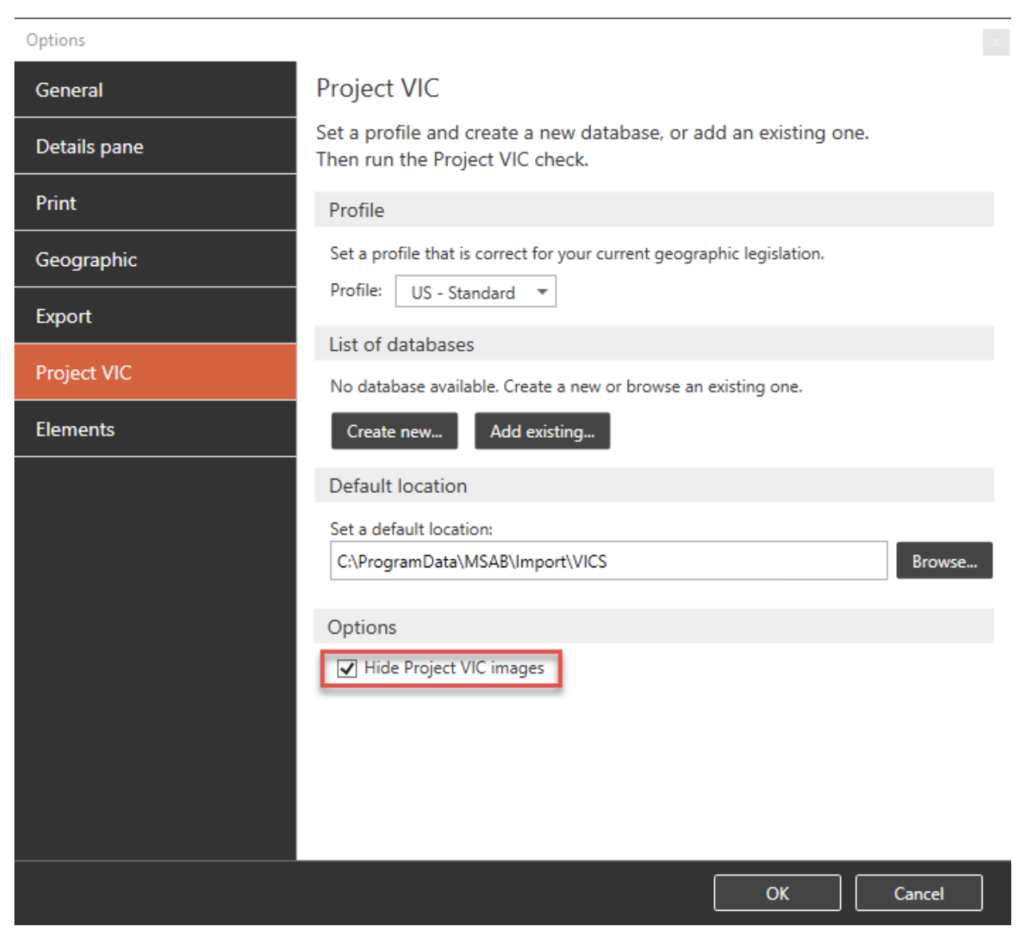
A small check box option at the bottom of this screen gives you as the examiner the ability to hide images that have been detected in your extraction as matching a Project VIC database artifact. While this is just a simple check box, this may be one of the most important examiner options available. Thank you MSAB, for giving us the ability to toggle this important option and for supporting your customers’ mental health!
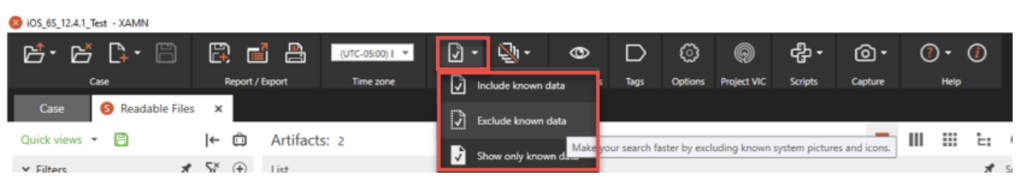
Switching over to the analysis of our iOS device, two of the options available to examiners that we thought were worth writing home about were the options to import and manage python scripts for analysis of information that may not have been deconstructed or represented as much as we would have liked, and the option to either include or exclude known data.
The option to exclude or include known data is a great option for helping to weed out known good or original data that may not necessarily be relevant to the case at hand, and may only hinder the investigator by crowding the display within XAMN. This could in fact work in the other direction as well, where an examiner may be looking for a pre-installed database file such as the sms.db file and they do not want to see the noise of all of the other artifacts that were recovered during the extraction. This setting is easily applied by selecting the document with the check box from the settings tab at the top of the XAMN interface, and choosing to either include known data, exclude known data, or show only known data.
Adding or managing Python scripts can be done by maneuvering only a few tabs over from the known data tab discussed above. Once you have imported or managed your scripts, one important note is that you must be in an Elements tab in order to run your scripts against your data.
The option to be able to add your own Python scripts is probably one of the most beneficial technical options available to us within XAMN. As digital forensic investigators, Python scripts are continuously used by the broader community and commonly shared as open source. A simple search for what it is you are trying to accomplish in the form of a Python script will likely be found by someone in our community. Nice work MSAB for giving investigators the choice to manipulate the way the data is being presented from the extracted contents, in their own way!
Report Creation
The next phase of our investigation was to begin the process of creating a report to portray our findings in a clean and well-formatted deliverable. The creation of a report in any forensic suite is one of the most important aspects of our forensic analysis. We can find the smoking gun within a case, but if we do not know how to translate our findings into a manner in which can be read and understood by someone who is not technical, it will all have been for naught.
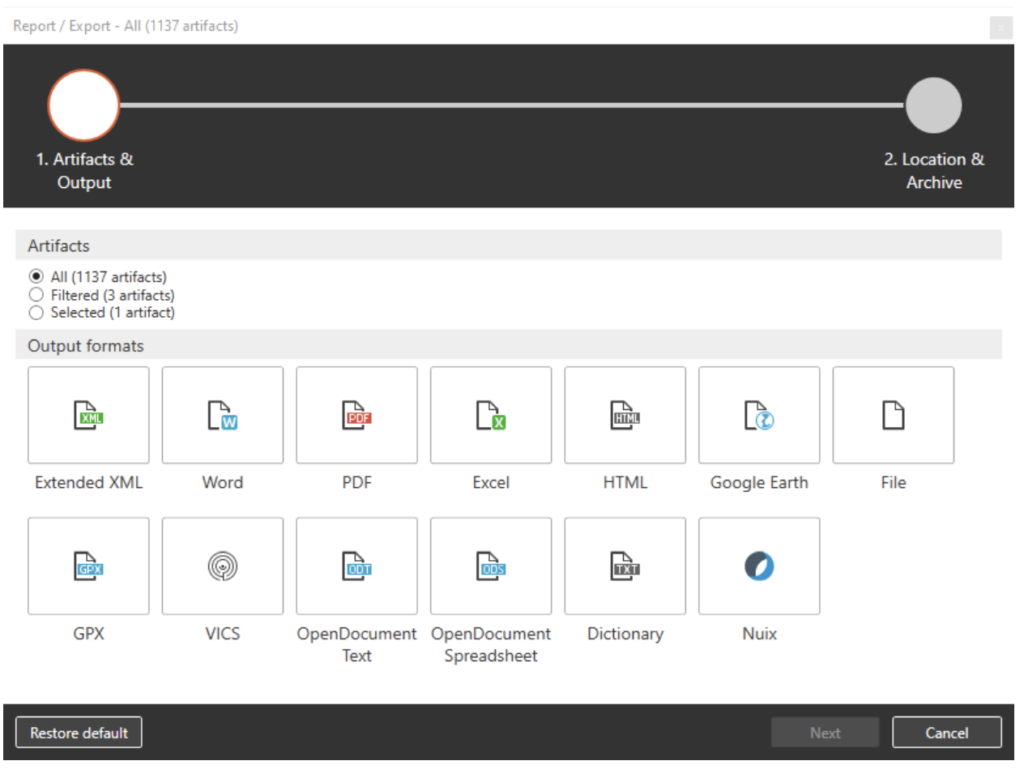
To put it more simply, reports can and will make or break your investigation. XAMN does a really great job at presenting a large amount of output format options, giving the examiner the ability to even customize the layout of a report, along with many other great features. When it comes to report creation within XAMN, investigators are provided with the following options for output formats: XML, Word, PDF, Excel, HTML, KML, File, GPX, VICS, OpenDocument Text & Spreadsheet and Dictionary file, as well as Nuix format for integration into Nuix.
Conclusion
After a considerable amount of time diving through MSAB’s flagship XRY & XAMN digital forensic software products, it is safe to say that they are a welcomed addition to any examiner’s toolkit. XRY offers an extensive number of resources and help files to guide examiners through challenging cases, ensuring that customers are well taken care of.
One aspect of XRY that we did not get to test was the customer service response time and ability to answer tough questions by our examiners. However, we are confident that based on the little interaction we have had with MSAB, and the gratuitous amounts of supporting documentation, they would meet expectations there as well.
XRY has met and exceeded expectations and opens a whole new realm of possibility for examiners to manipulate, present, and report findings for our investigation.
About The Author

Jared Luebbert is a Digital Forensics Expert and Litigation Support Professional with years of experience performing digital forensic collection and analysis worldwide. He is the founder and lead examiner of Gateway Forensics, a veteran-owned digital forensics company located in Maryland. Jared has worked on cases from a variety of industries including Energy, Manufacturing and High Technology, Medical, and Real Estate. He has assisted clients with patent infringement damages assessments, financial fraud, civil and criminal law matters, mobile device & computer forensics, intrusion detection, and incident response. Find him on LinkedIn or Twitter.