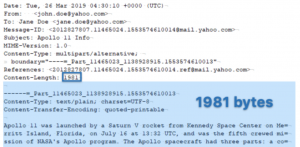
Using The Content-Length Header Field In Email Forensics
by Arman Gungor
As forensic examiners, we often have to analyze emails in isolation without the benefit of server metadata, neighbor messages, or data from other sources such as workstations. When authenticating an email in isolation, every detail counts—we review