Mike: If somebody would be kind enough in the chat to let me know that you can hear me, that would be grateful. Maria, can you hear me?
Maria: I can hear you, Mike. Can you hear me as well?
Mike: Fab! Yes. System works. Look at that. Technology! OK, we’re sharing screens. So let’s have a look at the time. Yeah. It’s 15:00 Central European time, 14:00 UK time. So let’s get this underway. Just so you can see us (got double screen, so I have to look the different way.) Can everyone see that? If I stop my screen for a second and stop showing screen…then you see our webinar screens. Hopefully you can. My name is Mike Dickinson, and this…I am talking to you from our MSAB office in the United Kingdom in Reading. And this is my colleague Maria.
Maria: Hello everyone and welcome to the webinar. My name is Maria Spånberg, I’m sitting in Stockholm and I’m responsible for professional services within MSAB. I dunno, Mike, were you sharing something now because I can only see the cameras?
Mike: No, I stopped sharing so I could make sure that people could see the camera. So I’ll…
Maria: OK. All good then.
Mike: So let’s see if we can do that. Hopefully you can see the screen now.
Maria: Yep.
Mike: Great. OK. As you said, my name’s Mike Dickinson. I am the chief business development officer for MSAB and (I’m gonna put my monitor there, I’m just getting used to technology, bear with me.) Thank you all for attending. I can see we have quite a few people and a few people more joining as we are speaking. So it looks like we had about 160 attendees register for this event, so we’re expecting a few more. So just give it a couple more seconds while we’re waiting. This is a webinar about frontline, about how we are changing models on digital forensics for mobile forensics to the future. So just to check you’re in the right place, just in case. We are recording this session. (I better check.) So if any colleagues want to see it later, we can always get you a link sent out, and I think we’ll make this video available on a video channel to watch later date, should anybody need it. I think I can…gosh, there’s still people joining! So I guess downloading go to webinar means there’s a few things to do.
So it’s three minutes past, let’s get underway and I will start the session, if that’s okay with everybody. If you’ve got any questions or you have any requests, just please put something in the chat. I may not be able to react immediately, but I will talk to it especially. This is gonna be more of a conversation between myself and Maria because we’re in two different locations, so we’re gonna talk about our experiences with digital forensics and frontline and particularly what’s happening in the UK, which needs to be at the forefront of this move to what we call frontline, and I’ll explain that terminology to you in a minute.
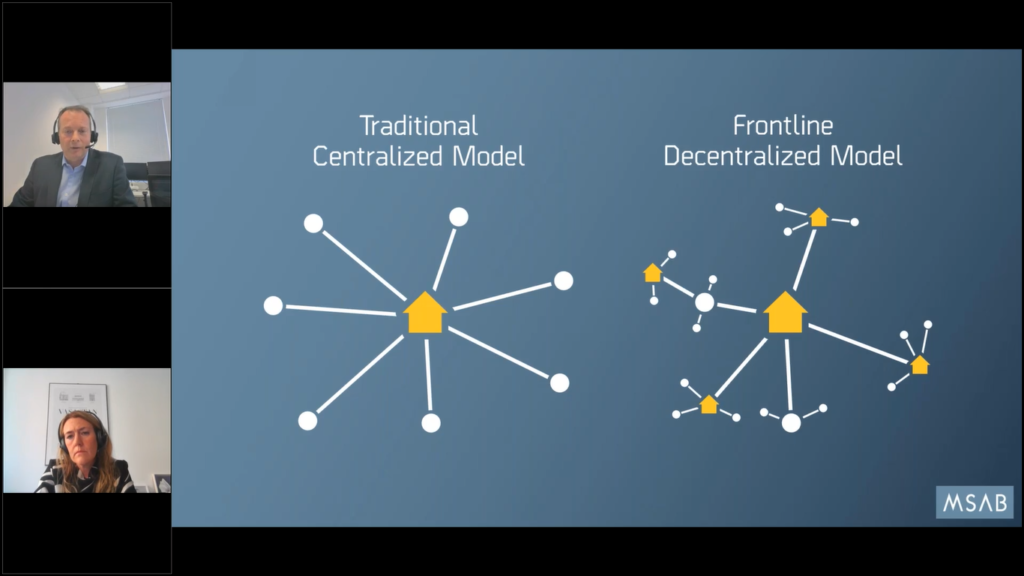
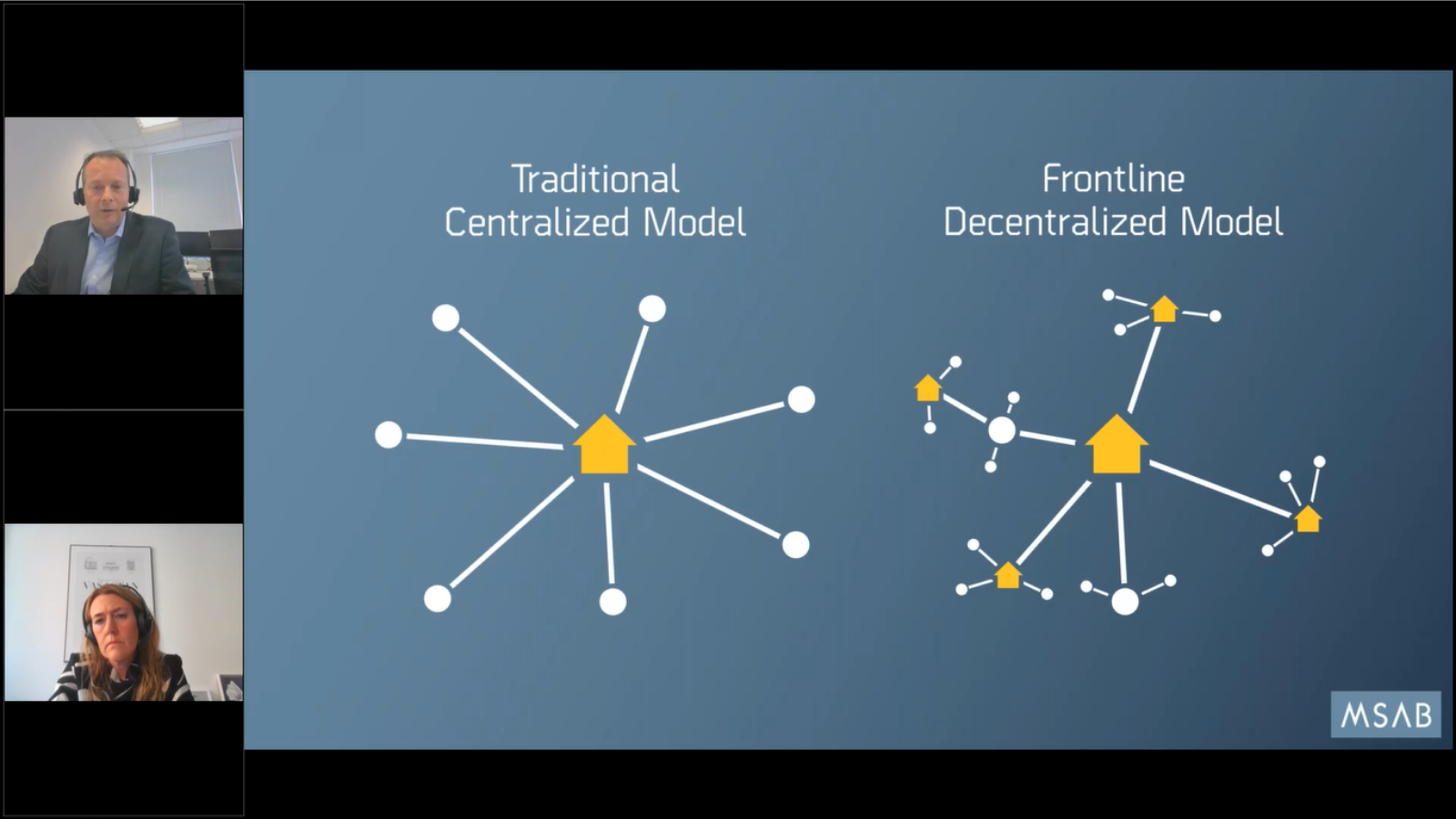
So let’s get underway and talk a little bit about what we are doing with Frontline. Because if we’ve learned anything about frontline over the last few years, especially with COVID, relying on one central point for all of your digital forensics needs can bring inherent risks, especially if there’s a pandemic going on globally and staff aren’t allowed into the office.
So we’ve witnessed quite a significant change over the last couple of years, that’s accelerated a process that probably began in the UK well over five years ago towards a more decentralized model for digital forensics.
And the principle is simple: in the beginning it made perfect sense that you would hire professional experts who know about digital forensics and spent their working life in front of a computer screen examining digital forensic devices, whether it be mobile phones or computers, and these units, these central units, were very, very successful.
Of course staff and people will seize more mobile devices. And the more evidence that seed that breeds more success, so more devices get seized until eventually you get to a point where there are more devices to be examined than there are staff or room capacity, and then you start to get backlogs.
Now depending on where you are and in what environment this can happen very quickly or it can evolve slowly over the time. But our experience from the UK market is that that happened, started to happen, very quickly by around 2010, some forces were experiencing overwhelm and starting to get significant backlogs, especially with mobile phone devices.
So they were looking for ways to try and cope with this. And the answer can’t always be just to hire more specialists. So they came up with the concept of a frontline decentralized model that you can see illustrated here, which is simply to tier the access levels to devices and try and roll out some of the technology to lower users who could do things in a simpler and easier way.
How that looks in reality is the idea that we have simple, easier to use tools. But they allow the system or the organization to move much faster to get quicker results on extractions. And also it can be much better because we can guide the process and reports.
So what we’ve tried to do is make Frontline an option that’s available for organizations who are dealing with mobile devices in particular, but all digital forensics devices on a day to day basis and have a large volume to deal with.
So what is Frontline? And Maria and I have debated this several times over about the different ways you can define it, but this is our best attempt, and you can tell us if you’ve got a better answer.
So we call it extracting and using mobile data in the field, or forward locations, using more staff versus this traditional central idea of a digital forensic lab with experts. The idea that you can only use experts and they can only be in the center has value, especially for the most serious cases, of course, but it’s not sustainable for the long term, as we see the adoption of digital forensics everywhere. And our belief is that it makes sense to try and break it out of the central lab where appropriate.
So we’re talking about doing extractions and analysis much faster locally, where it’s needed, and making it as easy as possible, so there’s minimal training impact. So the idea that you would go to a scene, you would find a mobile device and you would put it in an evidence bag, seal it up, then have it couriered securely to a central lab and then wait two months, three months, maybe six months for the lab to look at it and prioritize it and come back with a report.
We want to try and break that model and hope to show you how you can do it a better way. We’re essentially gonna present a proposal to change your business processes (not so much on the technology, although that’s very relevant). So it’s thinking a different way about how to do business day to day.
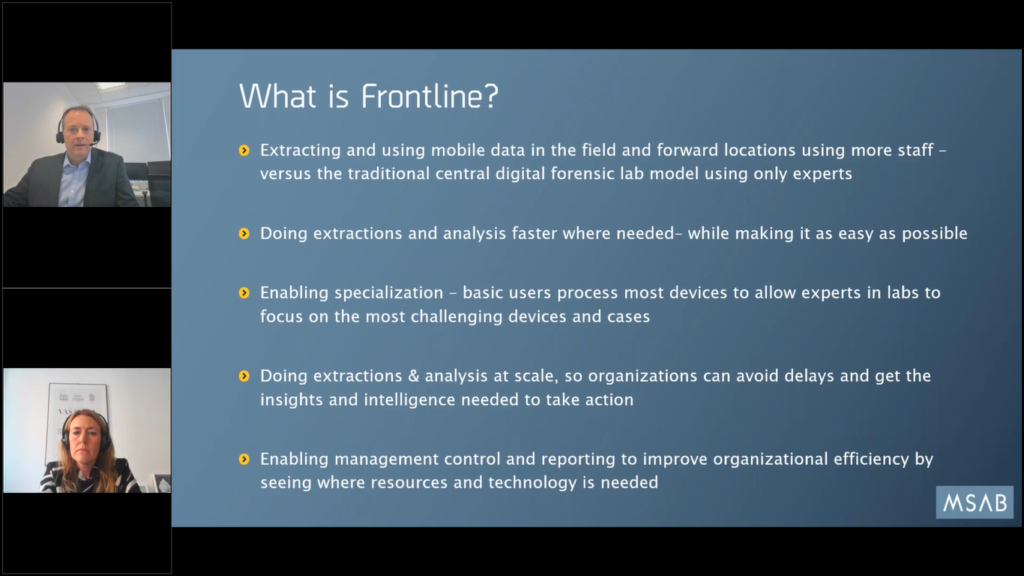
It is also facilitating and supporting the central labs. I can understand that a few people watching this might be going, “goodness me, how do you maintain standards? How do we do this if we’re gonna use people who are less well trained?” Well, it also allows us to focus on those expertise and actually enables specialization where the digital forensic labs now do just solely focus on the most important jobs with the most challenging devices and cases to stretch themselves.
Whereas basic users just process, it’s easy to use devices and easy to use tools. So we’re talking about empowering them in some ways. It’s about doing extractions and analysis on an industrial scale. That’s essentially what we’re looking at. Gone on the days of specialists in labs who had a phone every couple of weeks. Now we’re talking about it happening every day.
And we’ll talk about examples later, but for example, in London, in the United Kingdom, the Metropolitan Police, they’re experiencing 10, 11,000 devices a year or more, and they have to be processed somehow by somebody. So we’re looking at doing analysis and extractions at scale so organizations can avoid delays and get the insights and intelligence they need to take the action as soon as possible.
And finally, it’s about enabling management control. So we’re talking about reporting and improving operational efficiency by actually seeing where the resources are and the technology is needed. So it’s all very well saying, “well, we need to decentralize it, we need to put these tools out.”
But if we put them in the wrong place or with the wrong staff, that might not be very efficient. So when we move towards these processes, we are recommending mechanisms to monitor performance, KPIs, and produce reports that show you whether the technology’s being deployed and whether you get a return on your investment or not.
So frontline forensics to us, in MSAB, it looks something like this: everybody will have their own terminology for this, but we think it’s the most appropriate title we can think of. And I think this graph, this picture, sort of captures it very well.
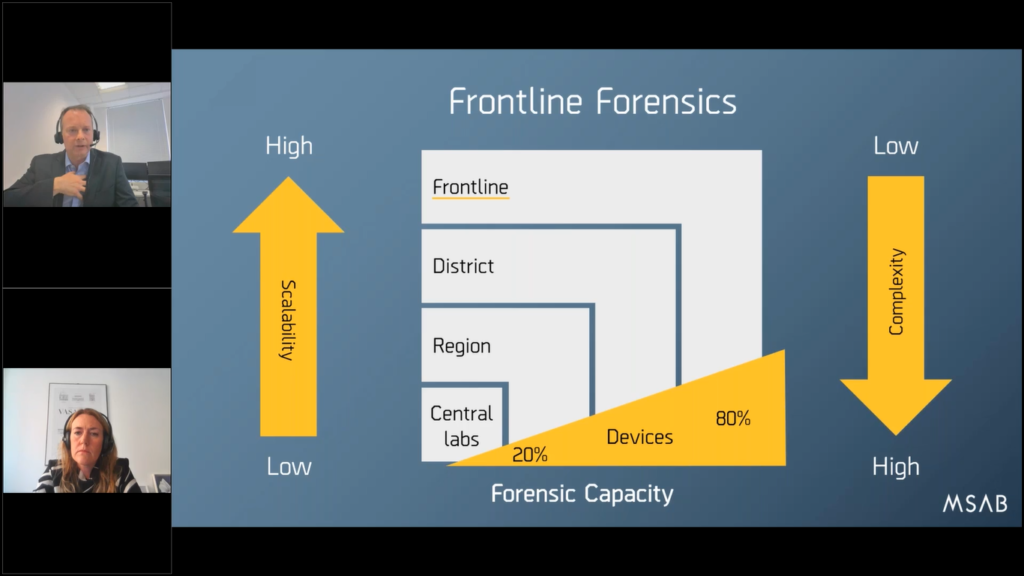
Essentially, we’re talking about making the concept of digital forensics highly scalable so that you can deal with a fast increase in the volume of devices being examined, being seized. By pushing the technology in a much less complex way, in a simpler way, towards the frontline.
And the wedge in yellow at the bottom screen, sort of illustrates this the best way. What we’re trying to say is that if you do this correctly, 80% of the devices you encounter (the simple to use phones, the burner phones, the minor crimes), they can be dealt with at the frontline or at a district level.
And there’s a filtering process that happens to the top 20%, the most complex crimes, or the most complex devices, the difficult to get to, they’re the only ones that get to the central lab. They’re the ones that focused in. So you are using the right staff, in the right place, at the right time.
This is an example, just to talk you through it in a more practical way of some of the deployment models that we’ve seen in the United Kingdom. This is being adopted in other countries as well, so forgive me, because I’m based here right now, then that’s my focus, but we see this technology being adopted in France and Germany, the US and elsewhere, where there’s a large volume of digital forensics examinations going on.
So this is the traditional model, this is…they call it one tier, but we have a high tech crime unit or a digital forensics unit (HTCU) and everything that’s there is dealt with and eventually you reach the point of overload and then you need to outsource.
And historically that was done by sending the phones they couldn’t cope with or the easy phones to a commercial supplier or another local police force who could handle the volume and help out, and then they would be paid for as extras. And it came to sort of hidden cost in terms of what’s the true cost your digital forensics, because it wasn’t…it didn’t look like personnel costs anymore, it started to look like billing or invoicing for contractors.
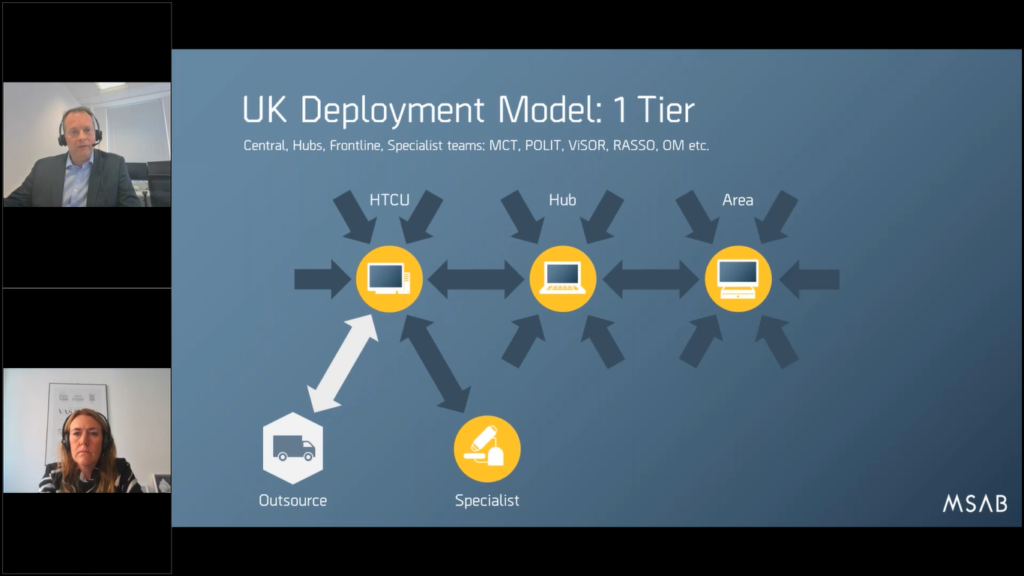
So one of the first moves was to try and look at another tier and see if the work could be pushed to what we call an area. So it’s high level central, but there were some regional areas that would take in those phones and try and deal with them and filter them, and they’d use different technology and we would deploy some of the very first kiosks, which Maria will explain a little bit later.
But eventually you get the idea of more deployment levels and we’ve got central hubs, we have standard high level work there, we’ve also got these DFU focusing on the research development and advanced work, so that we free up those specialists. So the areas got a kiosk. If they can’t handle it, it goes to a regional hub. They can usually deal with most things, but the last 20% of the most difficult go to the high tech crime units.
And if everything’s running smoothly, then you start to get this type of behavior as well. Not only are they being used on area or hub or in the central crime units, high tech crime units, it’s also being used by specialist departments.
There are also other departments being involved in there. We’ve got major crime teams. We’ve got things like RASSO (rape and serious sexual offense teams), offender management. So specialist units that historically would always send digital devices to the labs start to look at the possibility that they themselves could handle this type of technology.
And that’s become very pertinent, especially in the last year to 18 months in the UK. There’s been a lot of news and media attention about poor statistics in the prosecution of rape and serious sexual offenses. And a lot of the time the victims are pulling out because it takes so long for crimes to get to court and be prosecuted, and part of the problem (by no means all of the problem) a big part of it was seen that the removal of digital device and mobile phones from victims.
Taking that phone away for three months, wasn’t exactly helpful to engaging the victims and getting their consent. Suddenly just after they’re very vulnerable, you take away their mobile device and they don’t see it for three months and they lost their ability to speak to family or do their banking or whatever else. So the idea that you can turn around these devices much faster, say within 24 hours is very, very positive in terms of helping with the prosecution case.
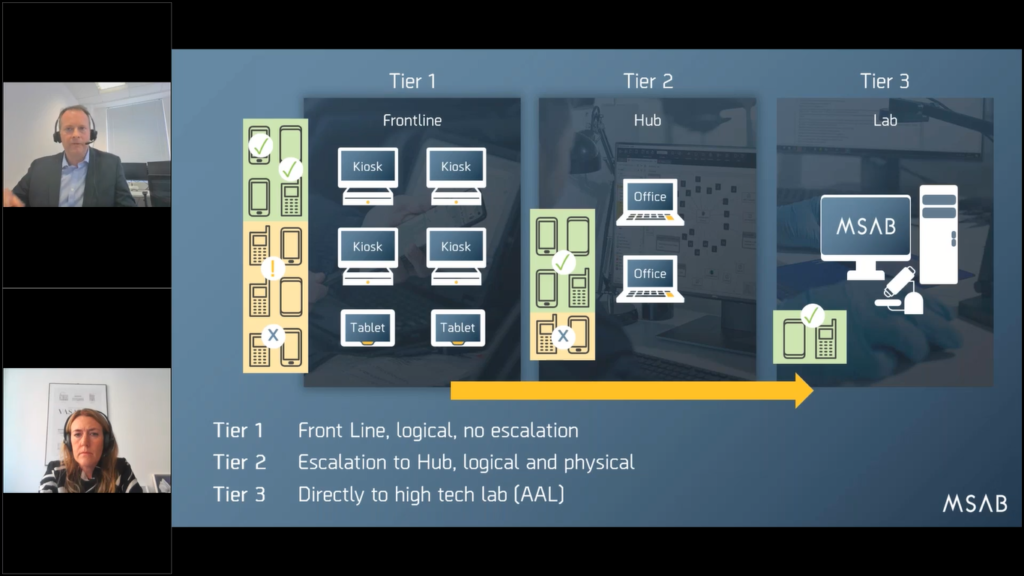
So summarizing it all up: if you get these three tiered models, you’ve got a frontline (and this is why we call it frontline forensics) where users with less than one’s training can use our technology, a really simplified interface with a kiosk that has a guided workflow or a tablet, and they can deal with a huge chunk of phones that you can see in the green ticks there.
If they’re not able to deal with some of the other phones (in amber), then they’re passed through to the second tier to the hub where offices equipped with slightly more powerful technology, perhaps X or Y office or more can handle most of those phones.
And then the final 20% gets pushed through to the lab where perhaps they’re using advanced acquisition laboratory tools and extra R&D exploits to get through some of the most secure devices, locked devices.
So just to give you some live project examples, we are…MSAB is very fortunate in the UK that we do business with every police force: there are 52+ in the United Kingdom, but we typically deal with county constabularies, these are smaller population areas.
So this is an example of one customer that we deal with. It’s 1.1 million members of the population and they have 1,730 police officers in this region. And they have 200 trained area users for their kiosks.
And another larger scale (that’s just a two tier unit, so for a large metropolitan police force), we have four tier system. So they have the high tech crime unit, the hub, the area, but they also use outsourcing as well. And that’s a population with nearly 9 million people. And they’ve got over 2000 trained users of their 38,000 officers. So it’s a whole different scale, as you can see.
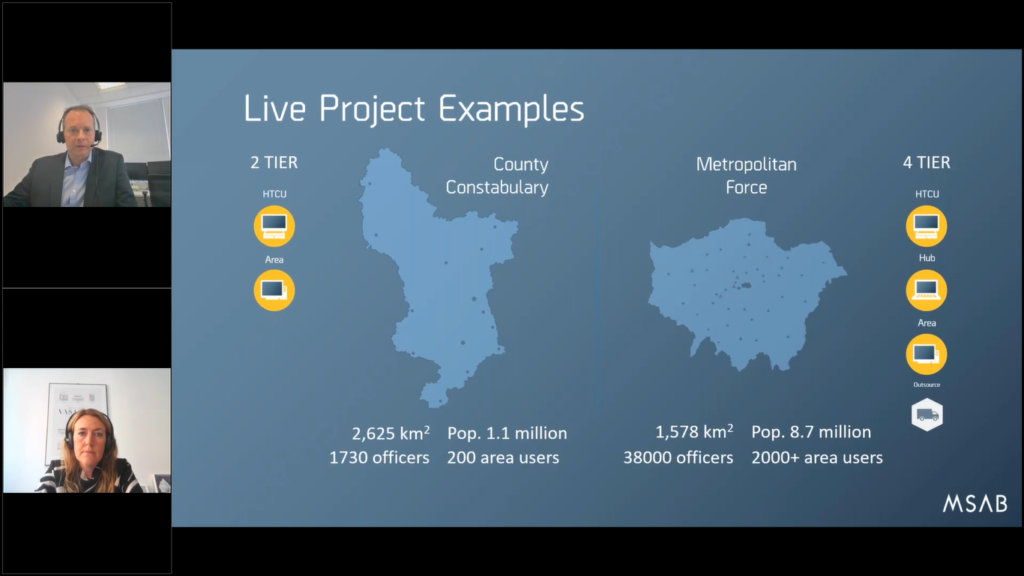
These are obviously…these differences are often dictated by funds, by staffing, and the technical resources, and also the geographical features. So there’s a lot of, “it depends”, as to what solution works best. But these are actual live examples we have in the UK as an example of how you can do things more efficiently and more effectively and turn around devices much quicker and get rid of the backlog that’s sat at the center.
So, Maria, if at this point it might be helpful if I hand over to you and you can talk in a little bit more detail about the hardware.
Maria: Absolutely. So I’ll start with just introducing myself in case there is anyone who has joined since we did the introductions in the beginning. My name is Maria Spånberg, responsible for the professional services team within MSAB based in the Stockholm office.
So if we look at frontline forensics, I mean, having the right tool is key to be able to speed up investigations and also reducing, or even eliminating, the device backlogs. MSAB Frontline solutions, they are offered on different platforms, such as the MSAB Kiosk and also the MSAB Tablet that allows users to work more efficiently. And we can go to the next slide, Mike. Thanks.
So if we start looking at the kiosk…I mean, the kiosk has truly played a significant part for organizations when scaling up and also decentralizing their mobile forensics operations. The kiosk has the power of the XRY software, but comes on a locked down terminal using a touch screen interface that guides the users, sort of step by step through the examination process, all according to a predefined workflow that we help customers setting up.
And this workflow can be tailored exactly to each unique or each organization’s unique processes and procedures. And I think Mike, I think I’m right, if I’m saying that we don’t have two organizations that are using the exact same workflow, there’s always small differences to rather big differences if you look at workflows on a worldwide scale.
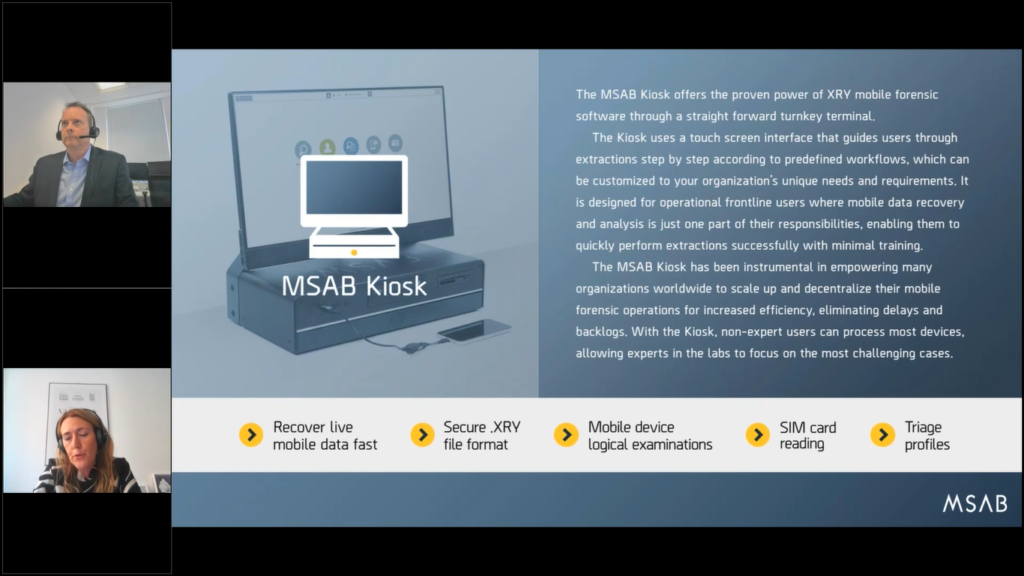
Also what’s good with the kiosk workforce and a little bit on what Mike touched on before is that you can have the non expert users examining devices the majority of the devices. So it frees up the digital forensic experts in the lab, so they can focus on the most difficult cases and challenging phones instead of doing the bulk work.
(We can go to the next slide.) So the kiosk also comes with enhanced security. Of course the kiosk is locked down to a single function with a limited number of…(phone rings) sorry about that…with a limited number of authorized users who will be able to log in and examine devices.
It runs on a Windows operating system but the access is extremely limited with a number of features disabled, and some examples you can see here, like “boot option from USB”, “Internet Explorer”, there’s “external direct memory access”, “SMB version 1 protocol”. So all those that can be sort of common attack surfaces, so to say.
Also the authentication to the kiosk is or can be linked or integrated with active directory for enhanced security. So you know, you can enforce the password complexity rules that is dictated by your IT organization also onto the kiosk. And the kiosk comes pre-installed also with Windows defender antivirus.
And of course we also have the XRY file container format that is secured by design to also meet law enforcement’s needs when it comes to integrity and preserving evidence. So as long as, or while the contents is in — is stored in the XRY file format, then the data is always benign and there it doesn’t allow for any alterations of the contents. And the file format also encrypts the content, so it’s safe to also transfer over a network. (We can go to the next slide.)
Mike: Just one comment, Maria, on that. I think it’s also one pointing out that the kiosk has been very securely hardened, and it’s also been penetration tested. So it’s fits with the IT support networks. We know a lot of the IT departments get nervous about putting technology on a network, but this works best if it is networked. Can work standalone, but yeah, just a point to make that it has been…so we try to be as IT department friendly as we can for security purposes.
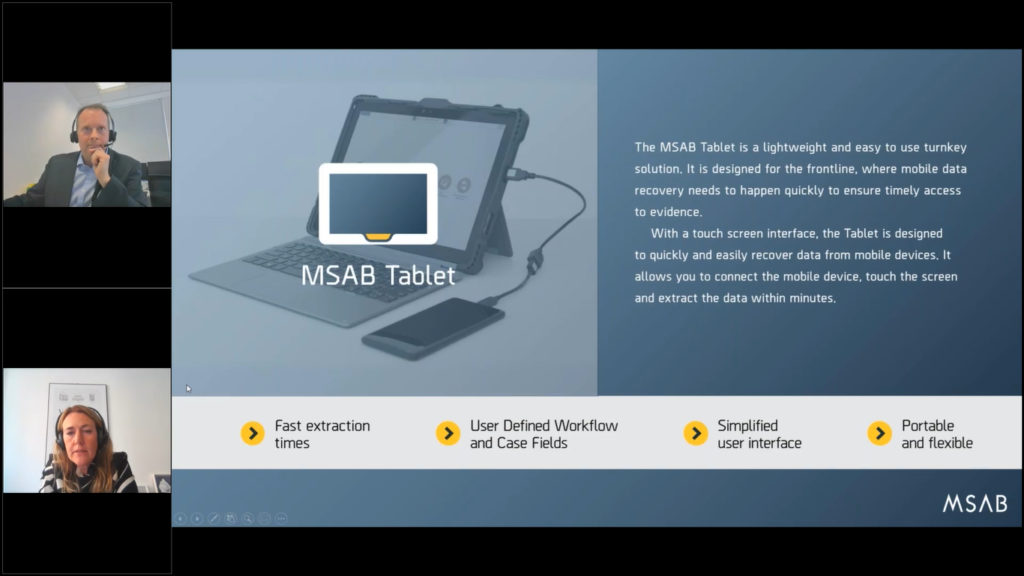
Maria: Yes. That certainly helps. Great. So if we go to the next slide. Great, then we have the tablet and the tablet, just like with the kiosk, it comes on on a touchscreen interface. It has the workflow GUI, and it’s also in a lockdown environment, but it’s designed to be sort of a lightweight, easy to use, portable solution that allows for faster examination out on the field.
And we can go to the next one and I’ll continue a little bit more on the kiosk and tablets. Thank you. So we’ll show some just examples of workflow for dialogue logs. Both the kiosk and the tablets, they are workflow driven.
We also have the XRY Express product, which is using also the workflow GUI, with the difference that the XRY express product can be installed on any Windows installed computer of your choice, really.
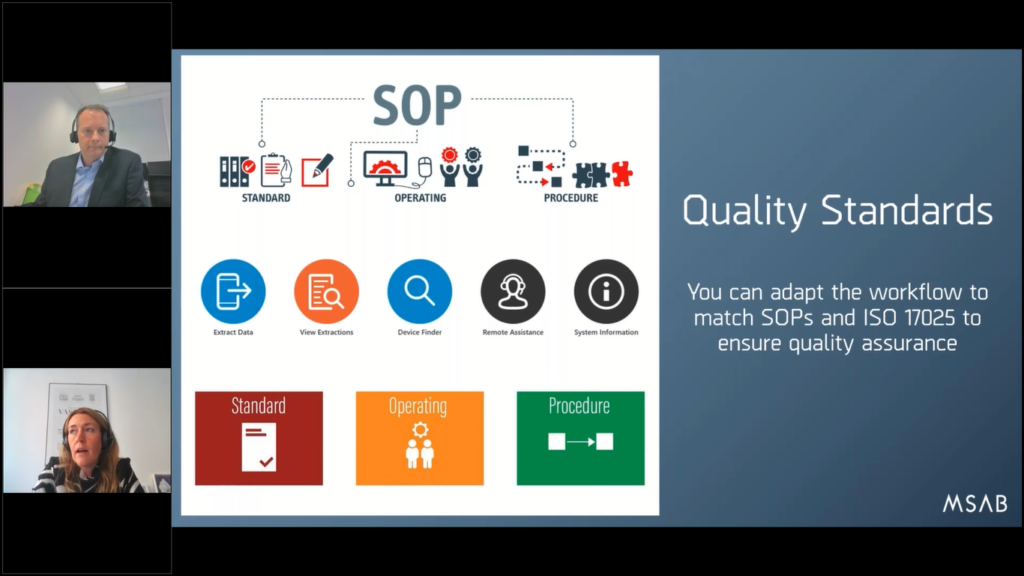
The workflow is a step by step guide that gives you just in time instructions, during the examination process. It can be fully customized, just like we mentioned, to comply with the local regulations or standard operating procedures that you need to follow.
And also the workflow ensures that your users follow the standard operating procedures. So for example, staff cannot proceed with the device examinations before, or rather without completing certain mandatory data fields, for example, or before meeting certain criteria that we set up as part of the workflow.
So the quality and also the integrity of the data is ensured. And I would say that, you know, having the right workflow that supports and also enforces your organization’s standard operating procedures, that is everything. I mean, you know, that’s really the true value of the solution.
And I think, Mike, you can stop me there because I’m probably biased also just because my department, we’re the ones that work with these workflows. But I think that…I truly believe that that’s the single most important part of the puzzle.
Mike: Yeah, no, I’d agree with you. And ironically, it’s usually the thing given the least thought to when we first encounter customers. So we, we try and help with understanding.
But as simplistic as this sounds, and as Maria’s brilliantly explained it, this is so vitally important because it, you can make this work to precisely your standard operating procedures or your quantity standards, but it does require a tremendous amount of thought how to set it up correctly. Like most things we do on frontline, they are really easy to use, but they are complex to set up because you have to put the hard work in at the beginning.
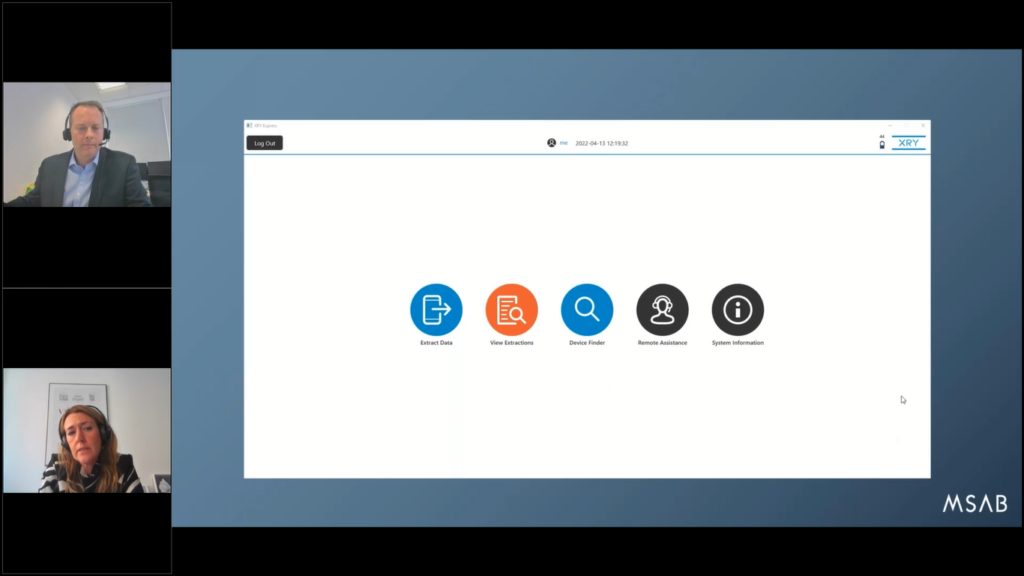
Maria: That’s right. And if we continue looking at this slide: once you’ve logged in to your kiosk or to your tablet, you will then be presented with the sequence that has been assigned to you by an administrator.
So, basically what you’re allowed to see, and in this example, I’m allowed to see the extract data option, so I can extract data from devices. I can also view extractions. I can use the device finder and look up support for different devices or apps.
I can also request remote assistance from an administrator if I need help. And I can also look at the system information, which basically gives you information such as what system version that is installed, and workflow version, if my client is networked or not.
So those things that might be good to have for troubleshooting purposes, if you’re talking to, you know, support or your IT department. And of course that is a very important thing, also if you have decentralized capabilities, that you can also, in a good way, centrally support all the clients and users rather than having to go out to all the different clients.
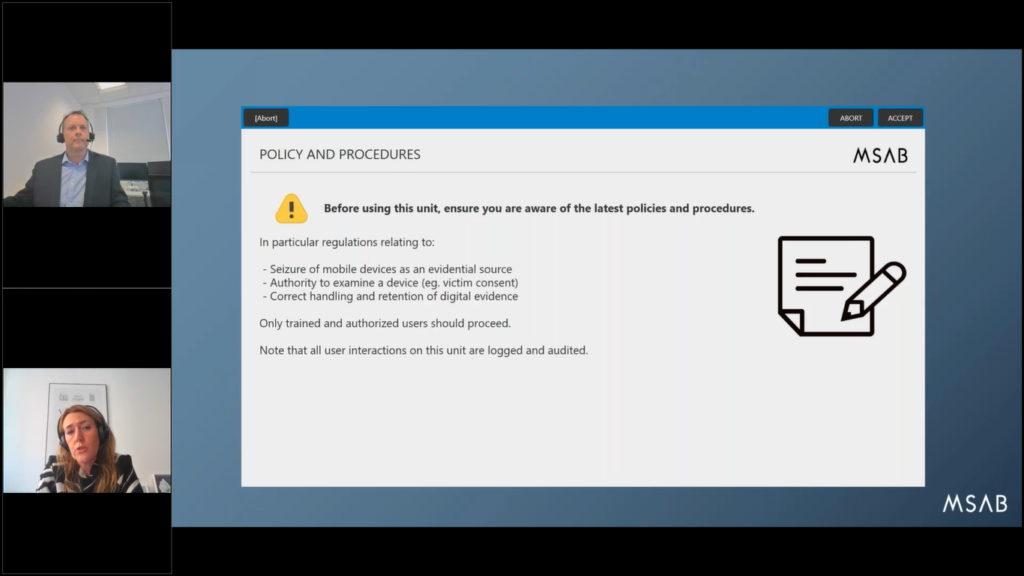
(We can go to the next one.) So, policies and procedures. I would say that the majority of the workflow implementations that we have done, they have some form of policy and procedure dialogue in the beginning with…can be references to regulations or guidelines or standards, ISO 17025 or ACPO, or you know, what have you here, that the user needs to approve or accept before continuing. (We can move to the next slide also.)
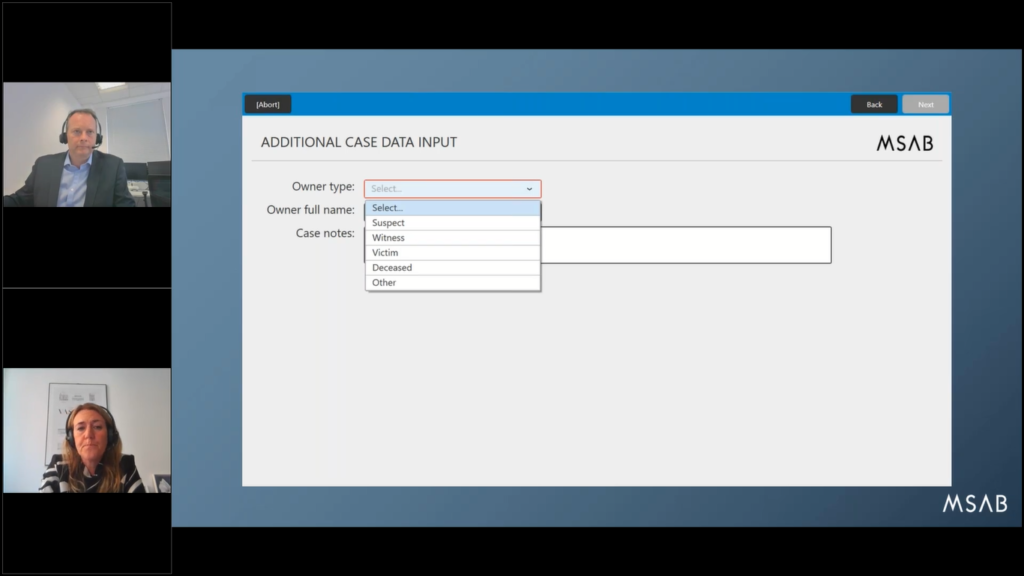
There we go. So this is an example, a pretty basic example, but of case data input. So, you can set up different customized fields here with data that you would like to be captured as part of the examination process. The boxes that you see in red, those are mandatory and need to be filled in before you can continue. Also drop down lists, that’s something that we tend to use a lot, we like using that because that, of course, you know, ensures that we have consistent data, especially if you want to draw statistics from the input later on.
If we jump to the next slide, another common example is also to capture of course, the owner type of the device. So for example, suspect or victim, witnesses. And depending on the owner type that you set up, you can set also the workflow to take different routes or paths in the examination. And for example, use specific triage profiles for witnesses and victims to only capture the relevant data. For example.
Mike: Maria, if I could interject, I think this…
Maria: Yeah, please do.
Mike: This is a good example of how you can really help out…we’re seeing (talk about it later), but more and more attention being paid to whether you should be taking all the data or not just because the volume of data that’s being extracted these days on 512 gig or one terabyte phones is so huge.
It’s unrealistic to expect officers to be able to go through it. And the ability to change your behavior, depending on whether you’re a suspect, where you may say, “look, this is a suspect, so we must justify taking all the data”, whereas maybe this is a victim, we should believe that or a witness, so we can be more selective about it.
It’s very important because this is the ability to change how the kiosk or the tablet will extract data from this point. So the workflow determines the behavior because it’s all been agreed in advanced as part of your standard operating procedures.
Maria: Absolutely. (We can move to the next one, right.) So, in the workflow design, you can either set up a linear workflow, we tend to call it internally at least, which basically enforces the order of the extraction, such as depending on what order you choose to set it up. But for example, SIM card, then memory card, and then device.
And then alternative to that, then you can use this style that we refer to as a hub menu, where the users basically come back to menu from where they can choose what to do next. So for example, if you extract SIM (we can move to the next slide), you will then be presented with instructions for the SIM card, and of course, depending on how you choose to set it up.
And I think what’s really good also with the workflow is that you can tie the workflow, the instructions sort of to the experience level of the user. So a beginner user can have very detailed guidelines or instructions in the workflow.
And once they get more familiar, and get more experienced, you might want to limit and remove some of the instructions and more cut through the chase and do fast instructions. So that can all be adjusted for your individual users as well.
(We can move to the next slide.) So as part of the workflow design my team, we lead consultancy session where the sequence design is drawn out based on the existing standard operating procedures of the organization.
We also look at best practices sort of on a global level that we see when, when talking to customers from different countries. We go through a number of questions and topics really to do a deep dive into the current and potentially also future business processes.
And then as a result of those discussions, we then map out sort of the desired process in a flow chart, similar to this (apologies for the dark background here).
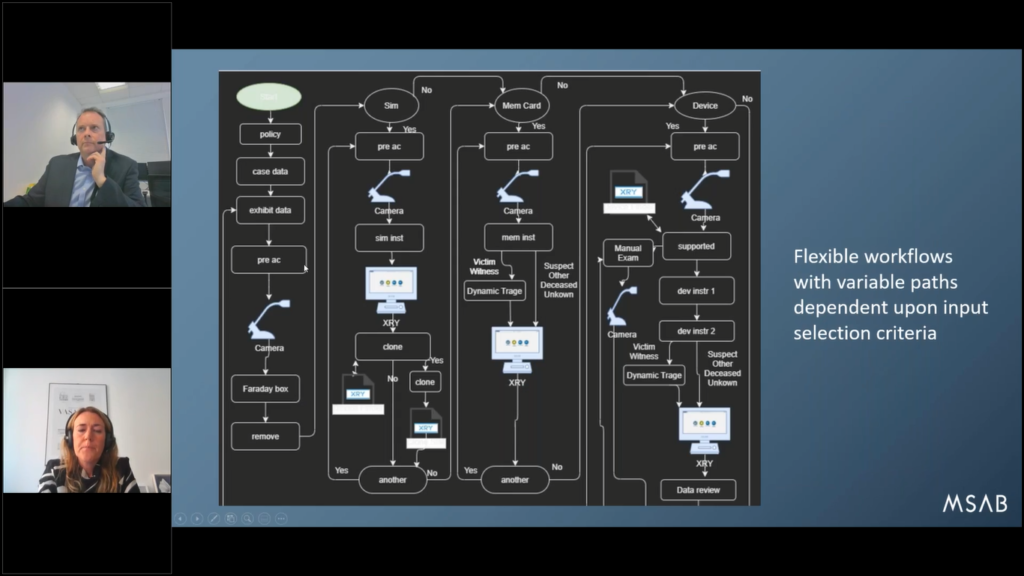
But this is mainly to then go through with our customers and ensure that we’ve captured the process in the right way before we then go ahead and start working on the actual workflow.
And one thing you can see in sort of the middle of the screen here, from the memory card what we mentioned before is that you can set up depending on suspect type…or owner type, sorry. If it’s a suspect, it might do a full extraction, if it’s victim or witnesses, it might use triage profile instead.
Mike: I’d like to just comment on this Maria, just to say, this is a great example of the complexity that initially on surface, you think, “well, why on Earth do we need to worry about the workflow?” Well, there’s a lot of choices to be made here and the temptation and our experiences that most people focus on, “well, can you do this particular phone?”, or “can you get this particular app?” or, “can you do the data securely extracting it?”
And that’s…of course the answer for that hopefully is yes, can’t do every phone, but we tried to do most. But in the frontline arena, you’re dealing with the 80%: the ones we know we can do. The really complex ones they’re gonna go to the lab, and every tool you’ll have at your disposal will be available for that.
But for the majority of devices, you don’t want to be having multiple tools. You just want one to make it as clean, as quick as possible, and you want the users to make sure that they follow the right steps.
So planning it ahead, how they do the extraction and, and in what order, whether it’s the SIM, the memory card and the phone and how much they can take off the device. That’s the real questions that are often unanswered until we get into the consultation period.
And that’s the point to think about when this becomes industrialization, then everything needs to be automated. So everything has to be considered that previously professionals wouldn’t even think about consciously because they’re well aware of how to do it.
Maria: Great. So automated report integration. I think, you know, since digitalization is increasing rapidly and as part of that, we see that a lot of the organizations that we talk to and as part of the workflow design process, many of our customers want to try to move away from all the sort of manual forms to fill in as part of the examination and instead integrate those parts into the workflow and capture that as part of the case data fields in the workflow.
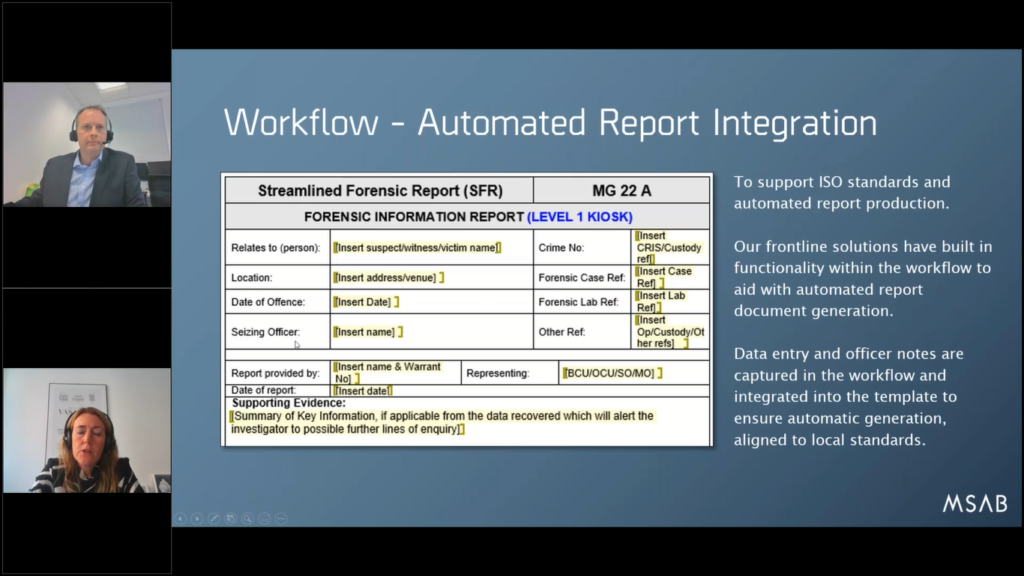
And we have this feature where you can capture these sort of fields that are filled in by an officer in notes and, well, case data fields that are filled in that can automatically generate the report.
In the UK they are called Streamlined Forensic Report (SFRs) but it can be really any templates of your choice that we then tie into the fields and do an automatic report based on that template and fill it in. So can generate a PDF in the end or a Word document to also support ISO standards with this report.
And continuing with standards: I mean, running the workflow, of course the process is totally predictable, it’s auditable, it also reduces the risk of error. And with a quick pace that digital forensic is changing in. As you all know, there are constantly new devices and technologies emerging.
It is also extremely important to be able to adopt, or rather adapt to the workflow quickly to ensure continued compliance to standards. And, you know, being able to then update the workflow and push it out from a central location to all the clients ensures that quick compliance to new standards.
So that’s one really important thing that we see. And I guess Mike, on your home market (and UK is really the forefront there when it comes to ISO 17025), this is something that’s constantly being discussed, and debated, and feared, I guess!
Mike: All of those are more, yes! I need to be very careful what I say, because I have my own personal opinions about the suitability of ISO 17025, but nonetheless it is the standard by which digital forensic labs, and certainly the police use in the UK have to adhere to. And it’s very demanding on how they must do that.
And every new release of XRY software for example, has to be tested and independently validated, and each force needs to do that. So there’s a lot of work that goes on there. One of the other requirements that brings about is that people who are doing or involved in digital forensics are trained to sufficient standard and keep that, maintain that experience.
So one of the things we can do with helping here (we’ll see this more as Maria talks about it), is we can with a networked frontline solution from MSAB, you can actually monitor the usage and behavior and activities.
So you can see if you’ve trained (like one police force does) 2000 users. You can actually see who of those is actually doing this. Who’s had continued support and who’s still examining phones and which ones have mysteriously disappeared and no longer being trained. Did you get a return on your investment for that?
And you can see which devices are doing…which devices are the most popular ones that are being examined in your region, in your local police area. And that’s really useful because then, you know, you can justify why you’ve picked 10 validation phones because they’re the top 10 phones you experience in your regions, as an example.
So there’s lots of really useful metadata that we can pick up from usage behavior, the type of phones be examined, how long the average phone takes, that can help improve your quality standards.
And it means we can continue to tweak the workflow and update the workflow to continue to capture even more data for you over time to help with this standard operating procedure.
Maria: Yes. So if we go to the next one, then: “how to manage efficiently?” we’re asking there.
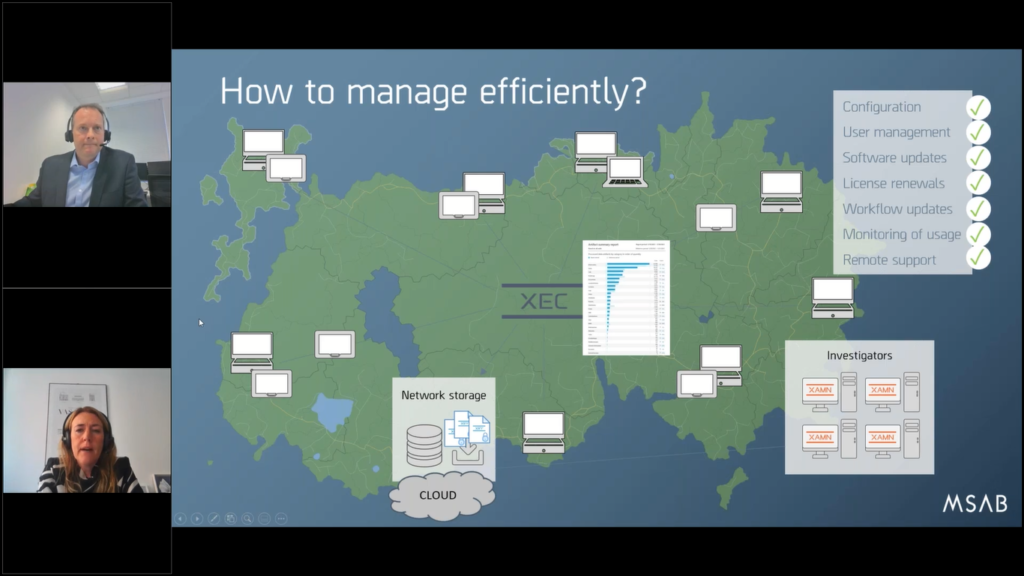
So, of course as mobile forensic solutions grow in scale, you might also need to manage different mobile forensic tools in multiple geographical locations. So there is a need to be able to efficiently manage and administrate all those endpoint clients from a central location.
And the majority of our customers, they are using XEC Director to be able to do just that, manage efficiently their systems, and do things like updating configurations and handle the user management, adding, removing users, push out software updates.
Also license updates, workflow updates, provide remote assistance, and also to be able to monitor usage insights, so to say with the reports that also Mike mentioned. And I have a couple of examples of that further into my presentation, so I’ll come to that.
But of course also centrally storing your data on a network storage that makes the management a lot easier or even, you know, look at a scalable cloud storage that makes it a lot more cost effective and also efficient in the long run.
And no doubt, you know, you will save a lot of manual work by being able to update all your clients remotely instead of having to physically go around to each location to do updates, which can be on a monthly basis, pretty much, or at least on a quarterly basis.
And also not having to transport data from one geographical location to another, which also is very time consuming. If you’re doing that, like we know some of our customers are doing on removable media, that of course is a big security risk as well.
Mike: Those are really good points, Maria. Of course, one of the huge advantages of a central digital forensic lab is that everything is in one place and you have to go there and update the machines locally in order to achieve it.
So of course, immediately one of the first questions comes up, “well, if you are advocating putting this technology out where it’s needed (at local police stations at areas and hubs), how are we gonna manage this?” Of course we have to have a solution for that, then, the solution is a network solution.
And XEC Director is that solution. Maria will give you a bit of information about it, but it brings back that ability to centrally control everything from one location to be able to log in and update all the hardware with the latest version of the software and check in and add new users, all from the center.
So all of that advantage of centralization is still there with XEC Director, but the hardware can be where it’s needed and the examiners can be where they’re needed.
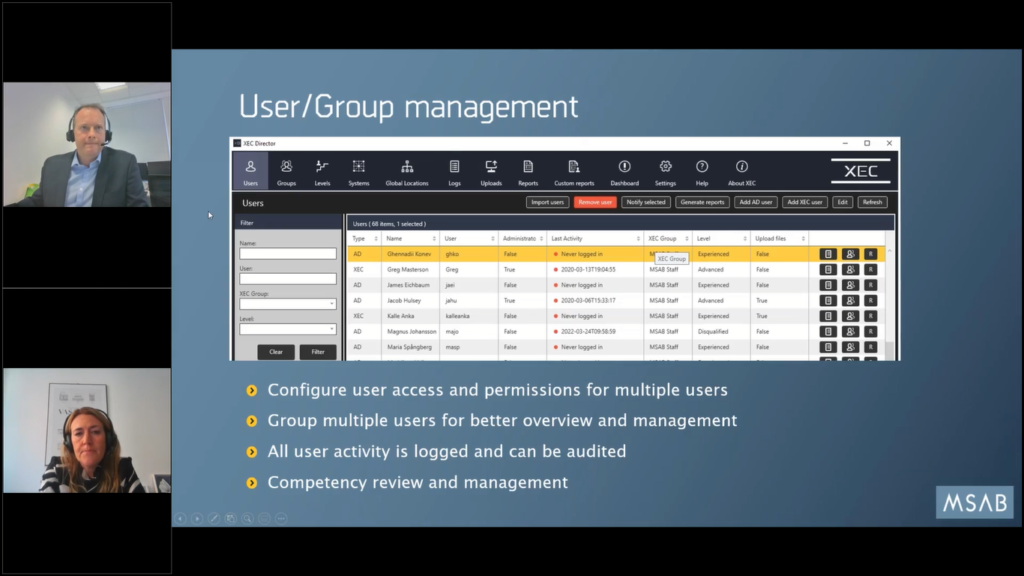
Maria: We can move to the next one, great. So I’ll just show a couple of screenshots here from XEC Director, because that that’s really a topic in its own.
But some of the features, like we mentioned, is that you can configure user access and permissions also for multiple users. You can group different users together, so that it’s easier to manage. Also you can view the user activity because all that is logged and can be viewed in really nice looking graphical reports, like Mike mentioned before.
And also you can do the competency review and management and con…you know, set up different criteria that the user needs to fulfill and, and control what different levels of users should be able to do and tie that into workflow functions as well.
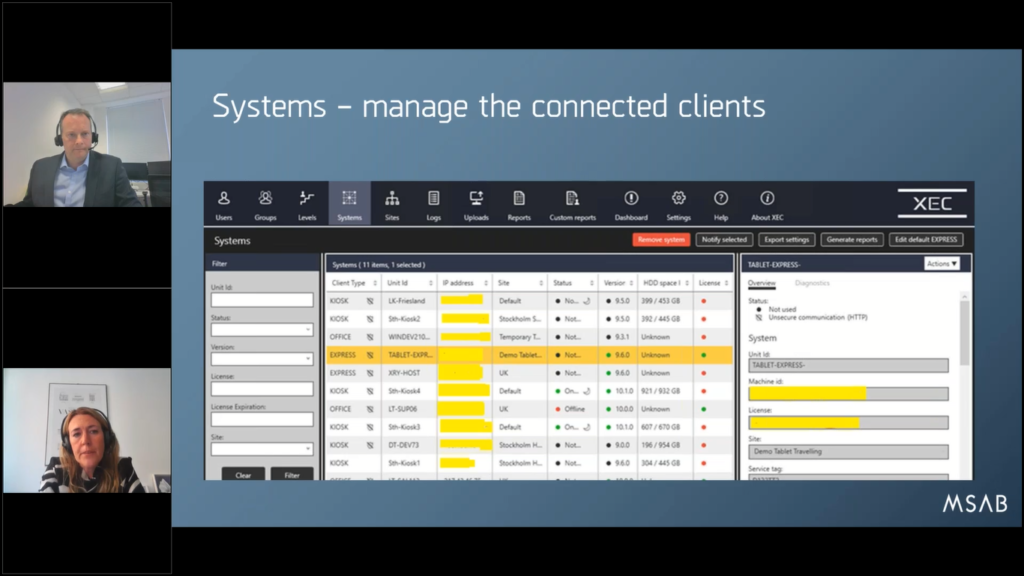
(We can move to the next one.) Then of course you can manage all the MSAB endpoint point clients through XEC Director. Apologies for this a ugly looking picture where I’ve masked out some of the sensitive information in yellow. So in real life it looks very nice! But of course you will there see then information such as a client type.
So for example, if it’s a kiosk, office, express, tablet, examine client. You can also see the unit ID, IP addresses, site (which is basically systems that you can group together, you know, for example based on location or whatever makes sense to you).
You can also see status, such as if it’s on online or offline what version that is installed, hard drive space available and from here you can essentially update the systems, licenses, provide remote assistance to the users, manage the configurations and update that all the systems remotely, see the event logs and also system diagnostics for your clients.
(We can move to the next one. Great.) So, using XEC Director, you can generate these management information reports either on demand or you can set up scheduled reports to be generated periodically to give you all these valuable insights of the usage and also to, you know, help you measure KPIs and follow up on that and return on investment as well.
And these reports can be generated both for overall system activity, but also individual units systems or individual user activity. And you can also create artifact summary reports. So, see different categories such as calls or pictures and also custom variable reports based on data that you have entered into the workflow.
So if we move to the next slide we can see an example there, and here we can see custom variable report for case type, and also an artifact summary report.
And one really nice feature there is that you can also decide a reference period, so you can compare the results and see sort of trends over time with, you know, last quarter, or last year, or, you know, whatever you want to…whatever dates you want to compare it with. But it gives you more insight, I would say when you can compare with a reference period.
(And we can move to the next one.) And there, we have also examples of custom variable reports for crime type, where you can see top 10 crimes types and also see that compared with a reference period. Has it, you know, increased or has it decreased? So that’s a lot of useful insights in those reports.
Mike: That’s great. Thank you, Maria. So you’ve seen some of the hardware that we use, the kiosk and the tablet, and we’ve talked about connecting that on a network to manage and facilitate frontline and some of the really useful management information reports that we can generate with that.
Thought now would be a good time just to talk about some extras, some special that sometimes don’t get the headlines from us. So just because we’re so busy explaining what Frontline is! But given that we have the luxury of over an hour on this webinar, we’re gonna spoil you with some extra information.
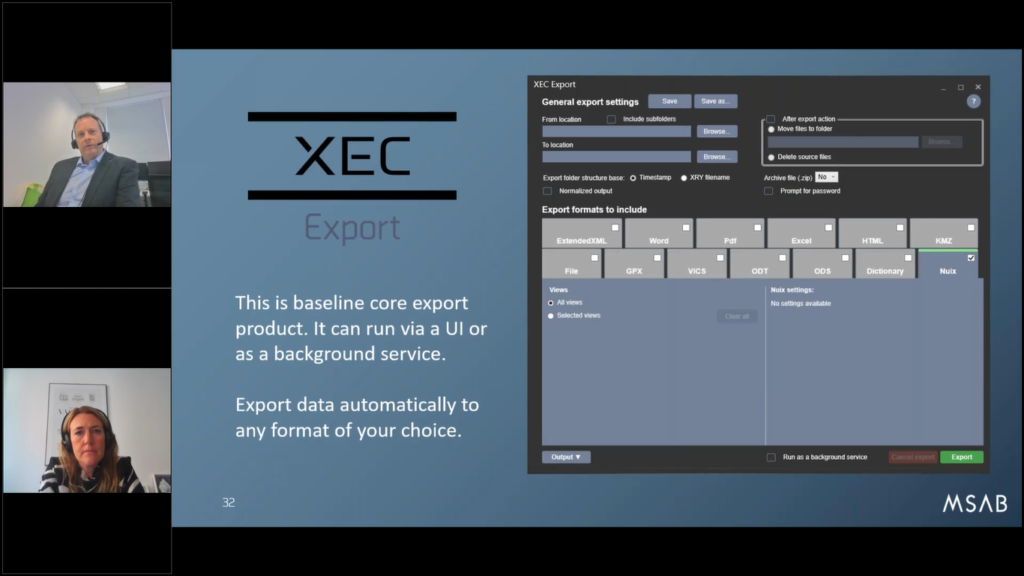
So the slide I’m showing you now is for a product called XEC Export. It’s well loved by some customers, but not known by that many. It’s a core export product that can run by the user interface you can see displayed on the slide here, but it also can run entirely the background service as a command line.
But what it has is the ability to take all your extractions using our technology (the Kiosk, Tablet, XRY) and convert them automatically as a report in any format you like.
So you can see here, we’ve selected for example, integration into a new analytical tool for a larger scale in crime investigations, but equally it could be an extended XML scheme or export, it could be to Word, to PDF for a report, it could be file types, we could send it to Project Vehicle, or as it’s known in the UK, the CAID for child sexual abuse material.
Whatever it is, we’ve got an export format for all the major standards. There’s tools available to anybody who’s got these systems, but if we’re taking all the XRY reports from a hundred plus kiosks and they’re being centered to a central server area, or even the cloud, then this is a great opportunity to buy XEC Export and use that facility in the background to ultimately generate reports. Again, it’s about automation and industrialization of processes, so it’s gonna be very helpful.
We’re gonna give you a sneak preview into something that we’re working on for the future. It’s not available today, but it’s coming. This has a code name of project Cascade, but I just wanted to talk about that because we’ve already got some customers in the UK moving this direction, and they’re actively talking about doing frontline extractions.
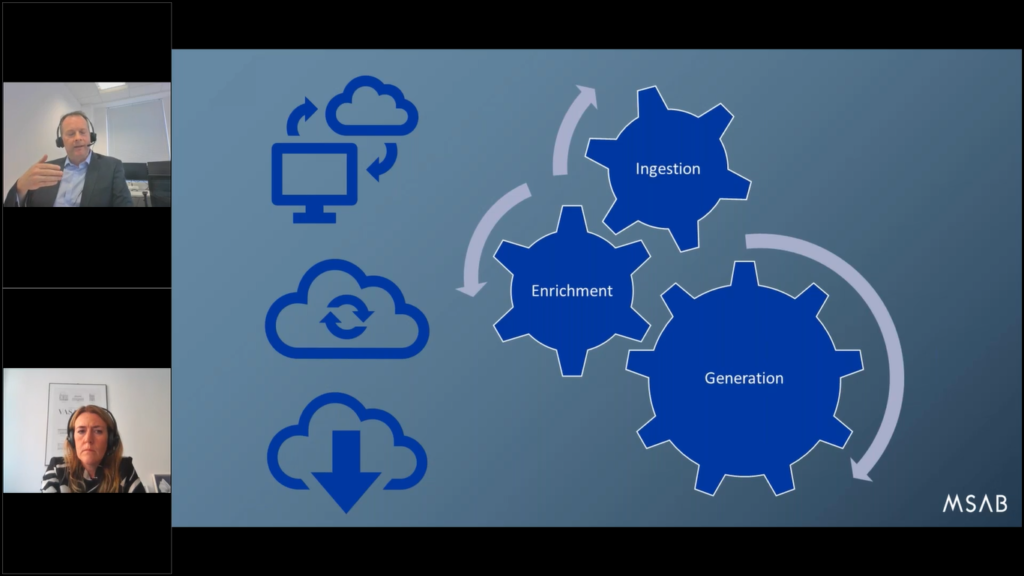
They already have Frontline deployed. They have kiosks or tablet units available at the frontline and technology coming in. But what they want to do is ensure the speed of extraction at the frontline, so that users get the data and can see the results very quickly, but there’s always a price to pay for that. And the faster we can get the extraction and present it, the less enrichment of data, the less decoding work we can do on it because there’s always a compromise.
So if you want image recognition done, that’s significantly extra processing power required, and usually time as a penalty, because if you’ve got a phone with 10,000 images and everyone needs to be looked at (you can do three images a second with a standard computer), it’s gonna take considerably longer to do the image recognition and not only decode the picture, but then tell you what’s likely to be in the contents of that picture.
So quite often we’ve seen a compromise situation where the decision is to do the extraction, do it as fast as possible so that you get a triage type review of, well, “how many messages have we got and how many pictures?” Just so that officers on the ground don’t spend too long in front of the kiosk and tie up that operational unit, because there’s always somebody in the queue behind them that needs to use it for the next phone.
They get the extraction done (20 minutes, half an hour at the most), but they keep the original data and then it gets sent off to a central server on the network or even the cloud, now we’ve got some active customers using GovCloud (secure cloud computing) and then it’s thrown up for ingestion and enrichment.
And that could be a number of different things, and we are working on some pilot projects right now, with a project it’s codename Cascade, and essentially it could be any one of the solutions you see on the screen here.
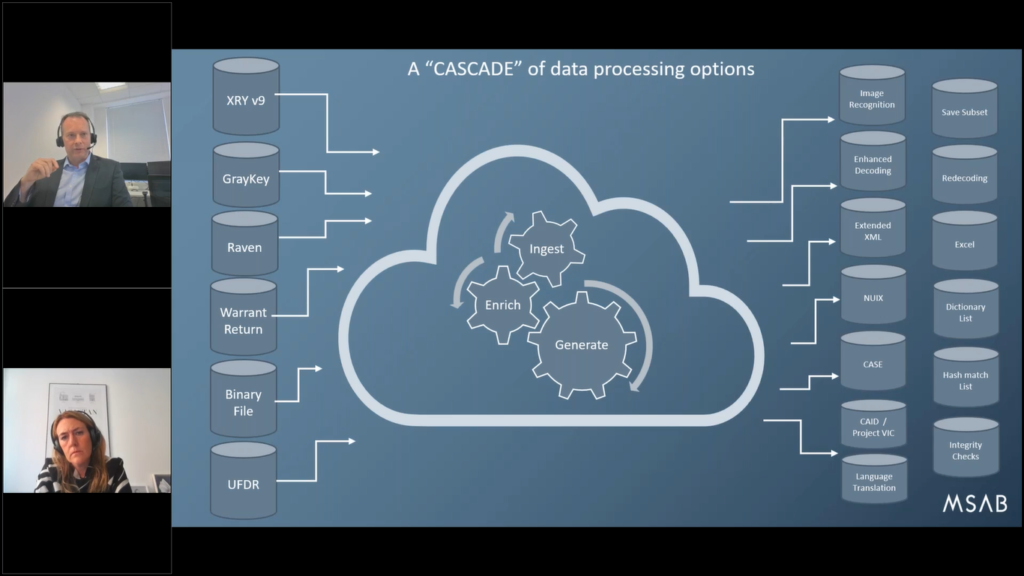
So perhaps you’ve got old versions of XRY that you want to reexamine in light of new evidence that’s come in version 9 (that’s currently version 10). So you could take XRY version 9 files, all the ones you’ve got on local server and bring them in and re-decode them for XRY 10, and benefit from all the new decoding technology we’ve learned over the last few years since you did that first extraction, and hopefully recover more evidence, but also ensure compatibility and longevity, because they’re all the same standard.
Equally, we can now take GrayKey dumps from iPhones or Android (their support) and we can ingest them and turn them into an XRY file and do the decoding because GrayKey doesn’t do that.
We also have a product called Raven, which is an Android based smartphone app that does similar to XRY at a lighter level, so it can be a phone to phone extraction.
Or we can take Warrant Returns from the likes of Apple or Facebook. We can take a raw binary dump file or even Cellebrite UFDR files, we can take those, ingest them and convert them into another format of your choice.
And on the way we can process it with enhanced decoding. So we could do something like image recognition, or scan it against the CAID database for child abuse images. Or we could look at language translations, or we could work on this extraction, which has a foreign language and convert it to your local native language.
We could even set it up to save a subset, so we avoid certain data. We can set it up to create a spreadsheet of your choice. Or something that’s often overlooked: dictionary list. That’s a nice one where we just simply take all the keywords in the Latin Roman alphabet, and we just simply create a list of all the possible keywords from that device that could be used to attempt to brute force on another locked device from the same address. That’s a dictionary list.
We could run it against the hash match. So you might have a hot list of telephone numbers, or images, or known contact names and you want to know if Mr Big, the master criminal of your local area, if his name or his telephone number appears on any of the extractions and how many people has he connected with in the underworld. You could run that hash match against all the data you’ve extracted from all the phones and see how many you get as a match.
And we can do things like integrity checks. So all of these options are a central online service that can be run centrally in a server, or in the cloud, and make you much more effective and operational with the data you’ve got and also historical data you’ve got.
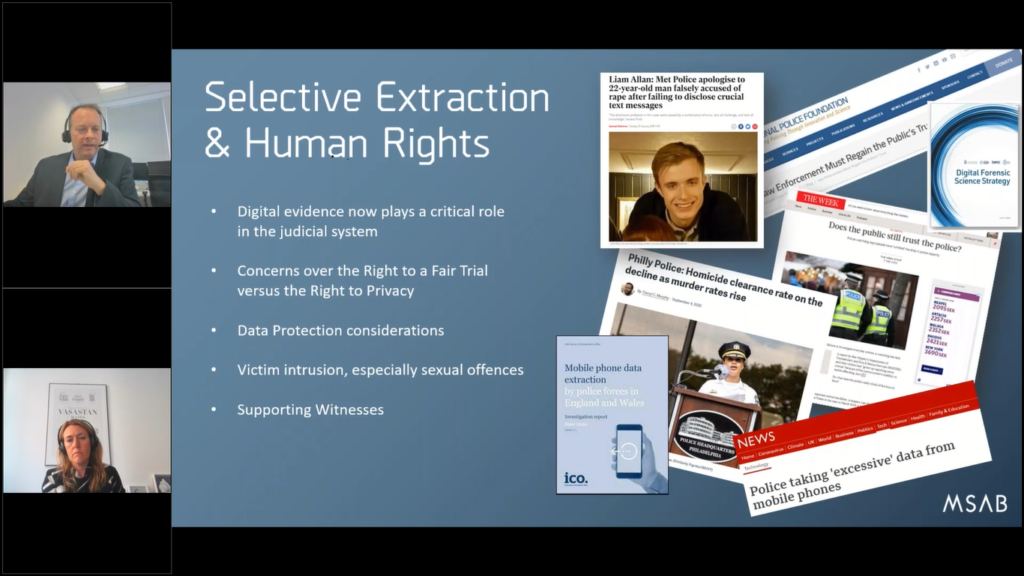
So let’s move on. I’ve told you about those things. I’m gonna talk to you about something that’s happening locally with the UK, and we’ve seen a lot of this behavior. This is about human rights. We see a lot of sensitivity around data privacy, essentially. And more and more so.
And this is example in this slide of some reports that have come out of the UK and elsewhere raising concerns about how much data is taken by the police, and whether that’s the appropriate choice to do.
And there’s been some recent publications that have come out from the UK College of Policing, there’s also a report from the UK information commission’s office saying the time of taking all the data from all the phones is probably over. You can’t process it or handle it or review it manually anyway, and we need to consider people’s human rights because everybody’s living their life on the phone now. And is it relevant that you’ve got their banking data details when you’re actually investigating an assault? Is there anything to do with… are these connected?
Of course that’s a decision locally for officers, but the idea that we do selective extraction is now very important. And the great news is with our Frontline technology is that we spent the last couple of years since this report has come out, developing this as a unique feature that’s available.
So digital evidence is obviously, we know, plays a critical role in the judicial system, but there’s a concern over what we would say is the right to a fair trial, i.e. surely you want to get all the evidence so that the courts understand all the potential, versus this right to privacy where you’d say, well, “yeah, but do you really need to know about the victim’s history from the last five years on the mobile phone? Is that relevant to the case?”
Probably not. “Do you want to give all this data we can’t even handle?” And the balance seems to be tipping towards, “no, it’s not relevant that it’s not proportional anymore to invade everybody’s privacy and you should be more selective about the data you take.”
We don’t make a judgment whether that’s right or wrong, and I can imagine there’s various people have a hundred views as they have in the UK. But the technology now exists, and you can take all the data, but you can do selective.
So this data protection consideration, the idea that you shouldn’t intrude the victim’s privacy, especially on sexual offenses. You know, if somebody has gone, a classic rape scenario that we experience in the UK, as somebody meets somebody on Tinder, they go on a date, and then something goes horribly wrong and they wake up the next day and they don’t know what’s happened because date rape drugs have been applied.
Well, you know, the fact that the two have interacted is clearly relevant to the case and you should probably want the Tinder interactions and the WhatsApp interactions if they’ve been chatting offline for the last 30 days. So it’s all happened in the last month. But it isn’t fair to then go onto the victim’s phone and take the history from three years ago of interactions between the victim and a boyfriend if that is not relevant, it’s personal and it shouldn’t interact with the case.
So having the ability to selectively extract that, which is now in all our XRY products is a real benefit because you can now choose what you take. So hopefully that’s seen to support witnesses and victims, and we think selective extraction is definitely the way ahead. And I’ll show you some examples of how we’ve tried to implement that.
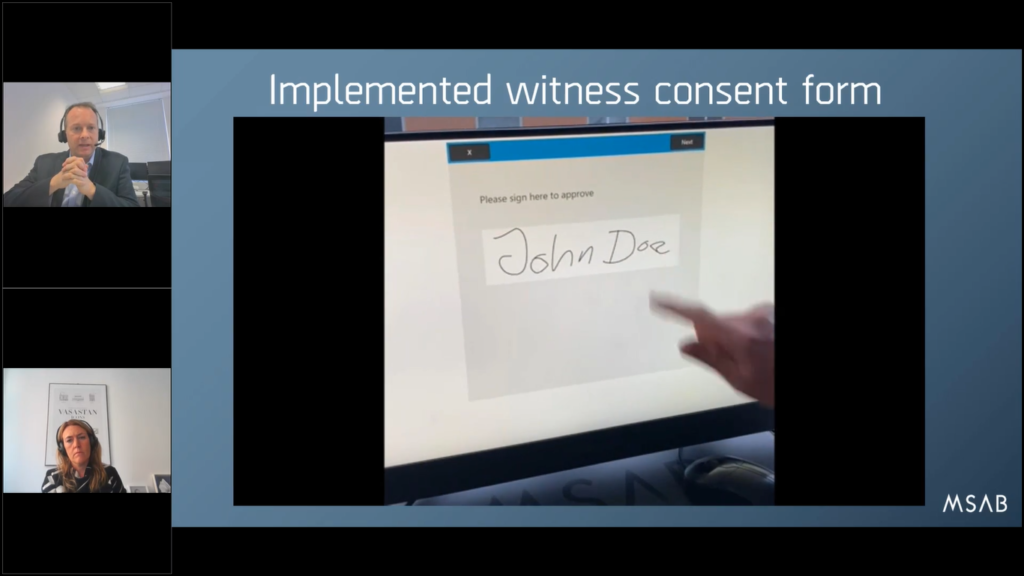
So, for example you can now implement this where a witness (I’ll just show you the video) can sign in the workflow that Maria described earlier to say that they consent to their data being taken for the witness and they can click next on that, and it becomes part of the XRY solution.
And when that’s all done to the end, here’s your streamlined forensic report, your SFR (it can be any report) with the witness signature, the date and timestamp all captured, and it’s all automated. So, you know, there’s not hundreds of bits of paper on the side where an officer has been taking notes alongside the tool.
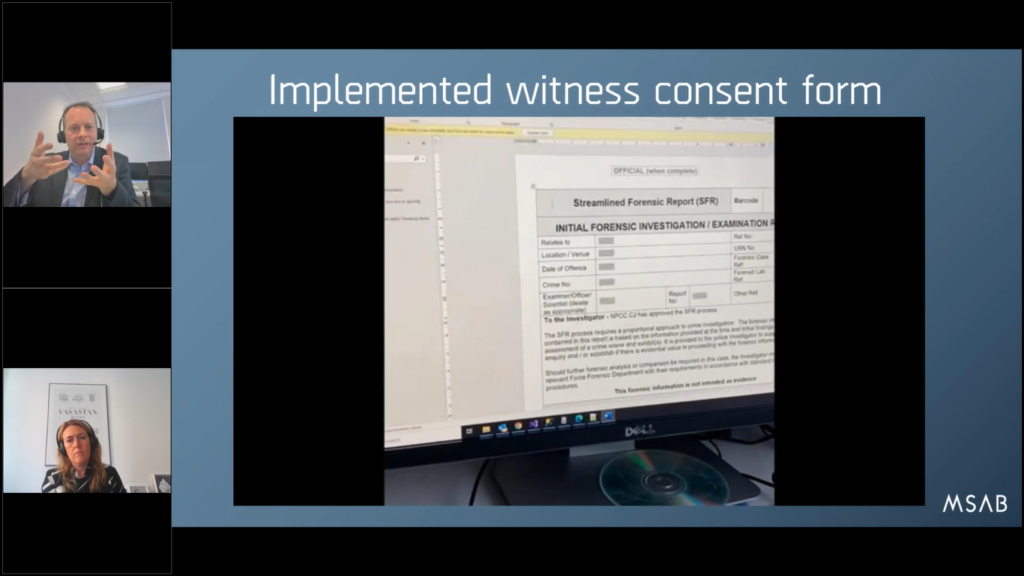
Now the workflow is capturing all the user notes, contemporaneous notes at the same time, and it’s all automated to the press of a button and you’ve got your nice document ready to go to court. So this is an example of how you can use technology to your advantage. And this new digitalized signature can be introduced to workflows, and is available now with the latest release XRY 10.1.
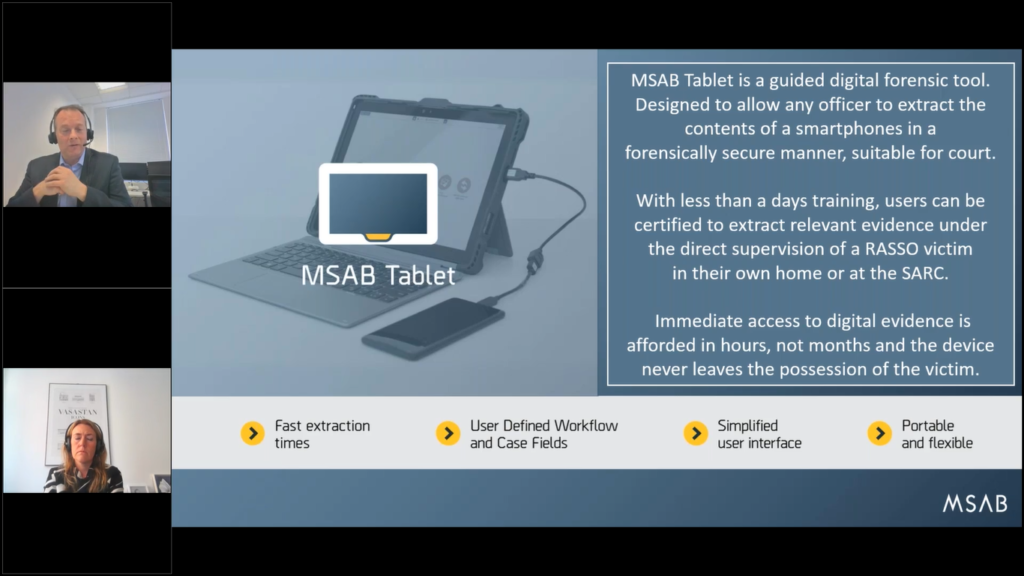
So yeah, they’re very popular right now. Maria touched on it. I’m gonna go into a little bit more detail now is the tablet device. We’ve got to the point where it’s become standard operation for most UK police forces to have kiosks deployed locally at police stations. So the tools are where they’re needed as the phones are seized.
The next thing that seems to be happening, and this extremely popular, is this the tablet solution, the portable solution. So what we’re seeing a huge amount of interest in specialist officers in investigative departments asking for portability, so they can take equipment in the car with them to go and victim…go to, for example, with rape and serious sexual offenses, go to their home address, or the sexual assault referral centers, meet with them and try and do the extractions on their phone, in their presence.
So we don’t even seize the device from the victim to do the examination. We actually sit down with the victim and do the extraction in front of them. Maybe it’s one or two hours. At the same time as taking their witness statement, we can be extracting the data on their phone, and they can see what data’s being extracted on the screen, they can sign a consent as you’ve seen there.
And that builds victim engagement and trust in the police, and their phone is handed back to them at the end of the investigation. They never lost control over it. So hopefully that really speeds up justice access.
And it means that the investigating officers have got the data, you know, within two hours, they haven’t had to send the device off to a lab and wait three months for it to come back, because it was in a queue prioritized with every other crime and offense that was going on.
So we think this is the future and has great potential. We’ve got great interest going on for these particular projects. Also for another example would be offender management.
So I’m sure it’s similar to many regions around the world where we have prisoners who are sent to prison for custody, and then they’re released, perhaps on a license with conditions. And some of those conditions may restrict their behavior and their activities, places where they may go, or even websites they may visit, especially if it’s sexual related offenses.
And quite often the local police are tasked with the job of going around on a regular basis to visit these offenders who are released on license from prison and check that they’re meeting their conditions. And they can do that by checking their devices and they have the power to do that, so they can go to their house, extract the contents of their phone or their computer and just to see what websites they’ve been visiting or get the geographical locations to make sure they haven’t been near any schools.
And again, the portability of the tool and the ability to do that and check it and instantly see the results means better justice for all.
So, selective extraction we talked about, I just wanted to show you some of the functionality that’s currently in XRY. Feels like I’ve been talking about this forever, but I’m very conscious that probably most people in this call will be the first time that you’ve seen this.
So, this is a screenshot from XRY. We’ve gone through the workflow, guided, and we’re now into the extraction stage and we’ve connected a phone. And the very first thing that happens now is we have the ability to pre scan the data, which can be really, really useful.
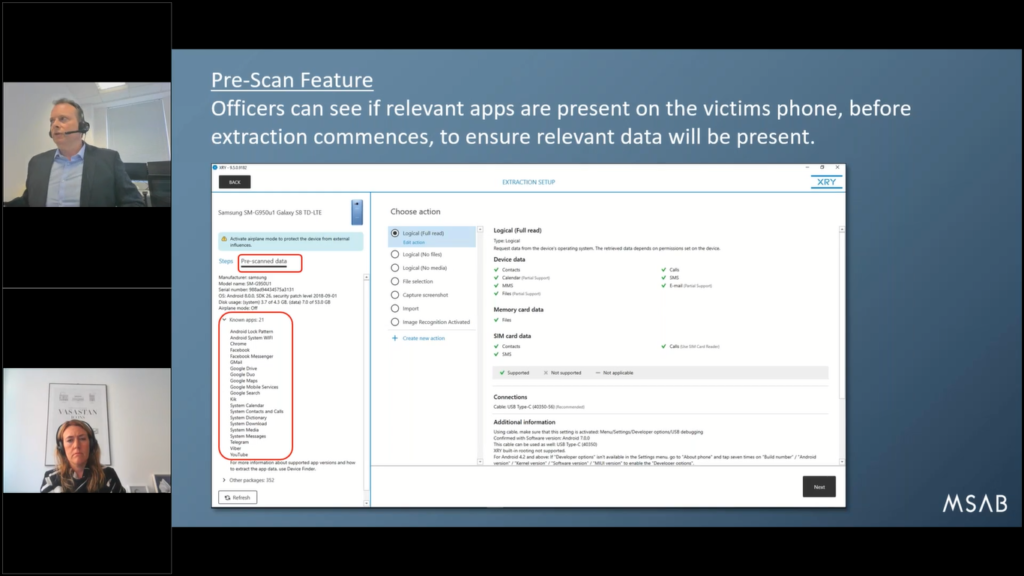
So, before you’ve even clicked “extract” there’s an interaction between the phone and XRY where it just does a check to say, “well, what type of device you are”. Nowadays, the devices also give a lot of information extra, which we can show.
And you see it highlighted here in this area called pre-scan data if you click on that, it says, “hey this phone’s connected. I can see it’s a Samsung Galaxy S8. But on top of that, I can tell you there’s 21 known apps and here they are.” And you can see there’s YouTube, there’s Viber, there’s Telegram.
Now, if you know already that this case were is relevant and there’s some messages on Telegram, this is instant recognition. Yeah, the app’s installed on this phone, so this is relevant.
Whereas perhaps if the…it’s a victim’s phone and they says, “no, you know, there’s WhatsApp”. And you say, “well, I’m looking here and I can’t see WhatsApp’s on your phone. Are you sure this is right?” It’s a good indication whether you’re in the right place or not. So that’s pre-scan data, and that just happens automatically.
Then we’ve got sort of time spent selection. So now we have a unique feature where we can say, “okay we’re dealing with a victim here of crime. The crime happened in the last year. I don’t need, you know, all the data. I just want to take timestamp data between March 2021 and June 2021 when the crime commenced.”
So you can selectively extract the last year, the last month, the last seven days, the last 24 hours, whatever you choose.
Now, it’s never quite as easy as it looks on the screen here. I’d love to say, well, that’s it. Of course there are question marks about what you do with data that has no timestamp. And there are options that you can configure in the system to say whether you want to include them or exclude them.
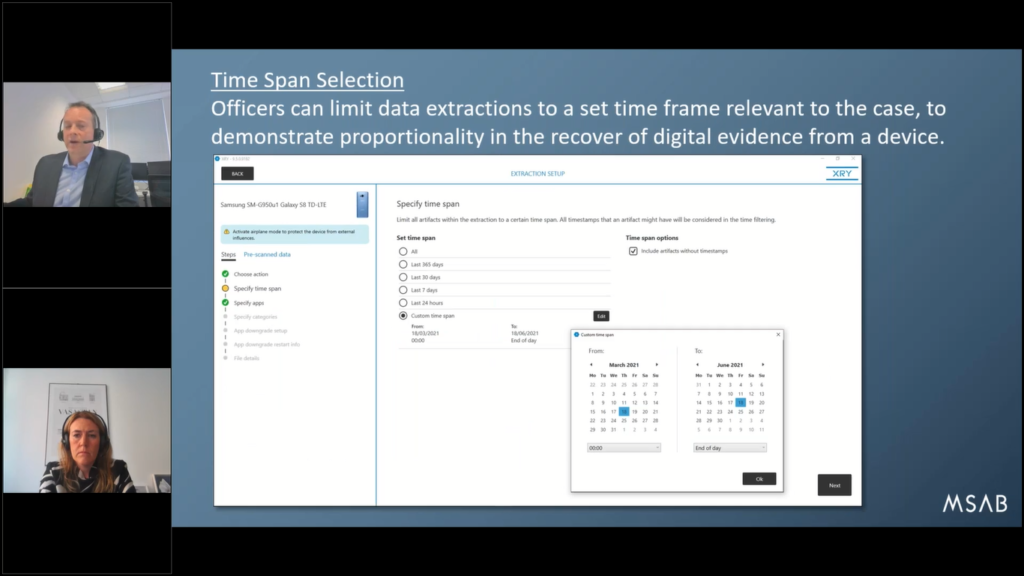
But suffice to say any data that is timestamped, we can pre-filter and if it meets the criteria, it goes into the extraction. And if it’s outside of the time set, and we can confirm that it’s never recorded, it’s never saved, so you won’t see it in the XRY extraction. So that starts to offer a degree of protection and data privacy.
Next up, we have the ability to select data by category. So you may be investigating a phone and with a victim and you saying, “well, you know, do I need all the data here? Do I need to know what’s going on with security or locations, or…I don’t need this health data. That’s not relevant.”
Health data, particularly nowadays with smart watches, means we’re picking up people’s heartbeat, we’re picking up their pulse, and even the latest device I’m wearing (Samsung Galaxy S4 or 3 or something) it can actually pick up my blood pressure, which is quite remarkable.
So the level of personal sensitive detail that’s being collected and stored ultimately on the phone, is getting quite concerning. And that’s why you’re seeing people like the Information Commissioner’s Office saying, “look, there needs to be some rules around this”.
You know, normally this stuff is very, very private and you would need to get very special permission from a doctor to see this level of medical device…data. So do you really need it for your investigation?
Now, of course, it might be the circumstance of the case are particularly relevant. It’s all about health. You know, could this person run up the stairs in the time they say they did? Well, then you might need it.
But at least the option is there now. Specify the category and only take the data that’s relevant. And you can show victims and witnesses this is what you’re doing to build the trust.
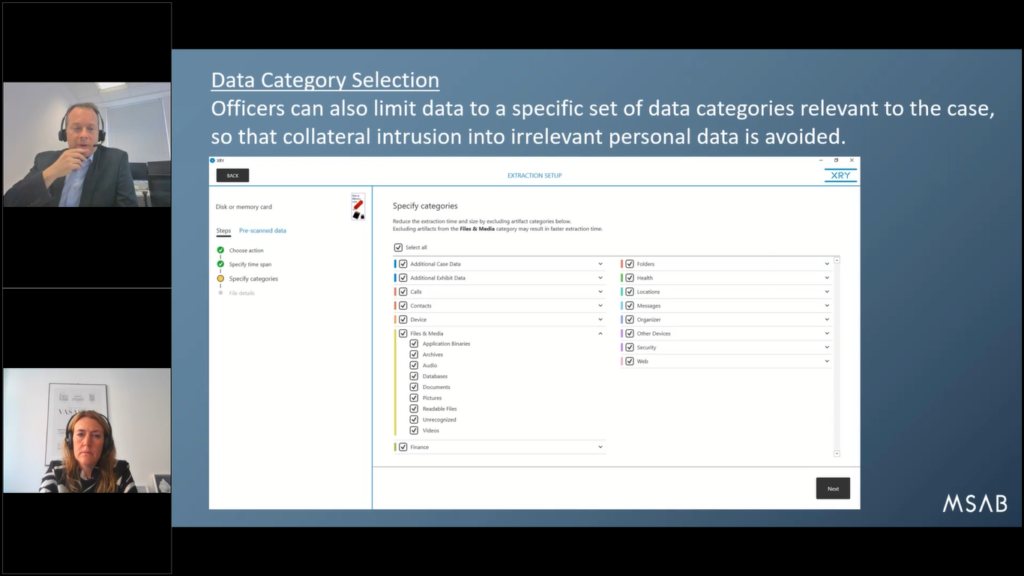
Another alternative is simply to do with apps. Everybody’s talking on apps, as we gave an example earlier about, say, a rape investigation. Maybe the only way that these two people (the offender and the suspect…and the victim, sorry) are connected with each other was via Snapchat and WhatsApp.
Well, in which case, let’s just take Snapchat and WhatsApp because there’s no reason to disbelieve the victim at this stage. Let’s take that data. And if there’s relevant information, you’ll have it. You won’t intrude the privacy, and we can just take the relevant app.
So, we’ve got this ability to select by time, by data category, and by app, and you can combine all three as part of the extraction chain. If you see on the left hand side there, there’s a chain of steps where you can see specify, “choose an action”.
You do wanna do a logical, do you wanna do a physical? You can specify the time span, you can also specify the category and the app downgrades and the app selection. So, I could say, “look, I only want WhatsApp from the last 30 days and I don’t want anything else.” And that is the extraction you’ll get via XRY if you use the technology.
One other step is hash matching. And again, this could be particularly useful, especially with offender management example I gave.
You want to do the extraction. Whilst the extraction is taking place and the decoding is happening, live, you can get alerts on the screen to the operator, telling them if there’s something of importance and intention on the device.
So here’s an example where the hash list match as we’re decoding has made five hits. It’s found something called “mastermind output”, “ajabaja” and “drugs”.
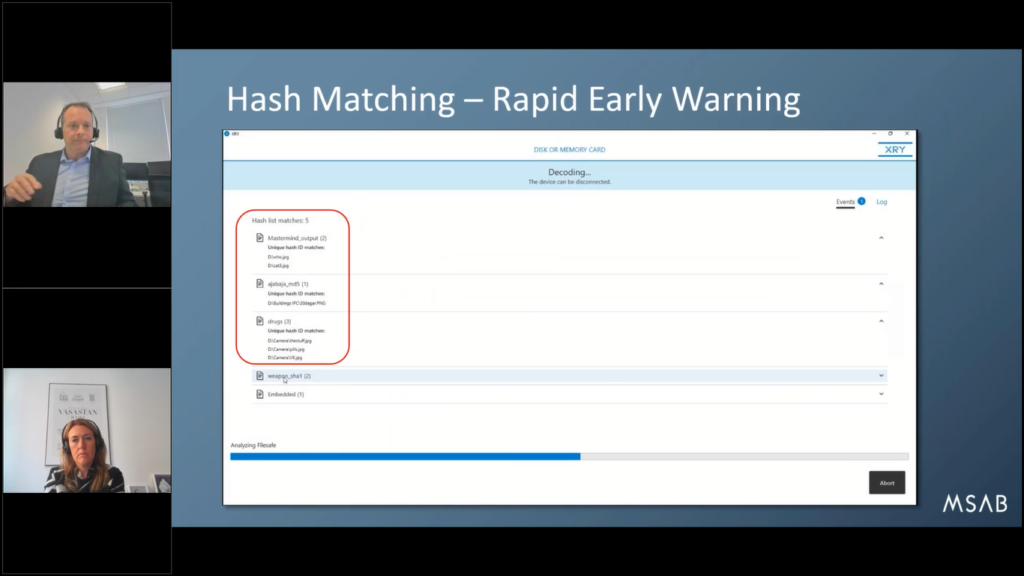
So obviously if you’re dealing with an offender release from prison on license for drug dealing, and you get a hit immediately on a hash match for drugs, well, that’s probably something you’re gonna wanna pay attention to. And it gives you a really early hint within the first few minutes of the decoding, there’s been an event and this phone is of interest and you’re probably going to once look at the extraction.
Maria, any comments that you’ve had from customers around these topics and the use of this technology?
Maria: No, I think we hear a lot of comments and questions around this. So it’s really something that it seems like all forces, I would say, especially in the UK are looking into.
Mike: Yeah, thanks. Yeah, hugely interesting. We think it’s likely to be the way of the future. Different regions of course, have different legislation, and different views on the powers of police, and what they can and can’t do. But the UK is quite interesting. They try to lead on a lot of this stuff. And we think it may be where things are going.
Right, let’s move on. (We’re going down towards the last 10 minutes of the presentation for those of you hanging on there, so thank you for your attention!) It’s a classic, but please don’t forget the staff training. Maria and her team could literally spend six months with you planning the workflow, the hardware, the layout, the network, and everything that goes with it. And then nobody’s got a budget for training the staff.
And it really…I think the best way to say is if you’re going to invest hundreds, thousands, even millions of your local currency in this type of technology, it’s kind of crazy not to think about the users as well, because they’re just as important and they have to have the skills and knowledge.
So we offer training in a variety of different ways to use Frontline technologies, some examples here. But Kiosk training can be done in less than a day. We can offer it via an online solution. We can train organizations with our “train the trainer package”, such that you can deliver your own, your house training at will to whom server you want within your organization. Or we can do onsite classes.
There’s always a balance and a trade off. We do recommend for people who are going to extract mobile devices to try and do an in-person class, whether it’s train the trainer or MSBA delivering it, just because getting used to plugging the phones and trying to run extraction and realizing that sometimes you have to plug in three times for no apparent reason, because that’s the phone is a useful skill to get, rather than try and simulate everything online, and then have your real first experience with an actual kiosk with an actual extraction.
But, we realize equally in COVID times, it’s pretty difficult to get people together in a lot of group areas. So online training’s available for all the technology you’ve seen played here.
So just to try and summarize some of the things that we’ve talked about here today. Frontline is a fantastic opportunity to professionalize and industrialize your digital forensics operations across your organization. And it’s as much a business process change decision as it is a technology change decision, although they’re both equally important.
But we can help customize this solution to meet your precise operational processes. Whereas in the central digital forensics units, it tends to be that we ship a box with a tool and everybody there gets locally trained on how to use it. We do it the other way around: we build a system around your business needs with Frontline.
That’s the unique difference. We’re building the technology to make you more efficient and XEC Director is the way to do that, to keep those efficiency savings of central management control. But at the same time, have the technology where it’s needed for the people who need it.

So with a single push button, we can update all the licenses every year, we can do all the software upgrades, because we’re currently pumping out 10 to 11 versions updates every year of XRY, because apps and phones don’t stop being manufactured.
We can update the workflow centrally, so when you figure out that you want to add a new process or capture some extra data, we can do that. We can talk about user permissions and authority levels.
Maria can probably explain this better than I, but one of the things you can do is, depending on the type of users, allow them more ability to do greater extractions. So some users who’ve had, perhaps a week of training, are allowed to do physical extractions instead of logical only users who’ve only had one day or less training.
And of course there’s the ability to generate management information reports. So you can show your bosses a very pretty picture and say, “definitely you’ve got a return on your investment, we’re doing more phones this year than ever before”. Maria, anything from yourself?
Maria: No, I think that covers it, Mike.
Mike: Thanks. Oh, excuse me. Jumping ahead. So professional services. Maria, this is your area so I’ll let you talk to this slide.
Maria: Absolutely, yes. So, I think with our experience from running, we’ve done a number of implementation projects and we have our own project methodology that we are using.

And of course I think for the majority of the customer that we talk to, they also understand that the project management part of it is really relevant and really important in order to get the project running in time, and according to the time plan that we set up with the customer from the beginning.
So we have the same sort of procedure that we are using for all these implementation projects that works really well. And there are so many different things to really think about. And just the things that, you know, might sound very obvious, like, you know, for us to have a project owner on the other side, a recipient of what we are delivering. That’s not always the case.
So, I think we try to really go through with our customers, what is expected, you know, from their side, what we will deliver and be very clear on that and state everything in statement of works from the beginning, even that sounds maybe boring. But it’s really important to know sort of who is doing what in these projects. So, and also to just have the right people in the team also is very important.
Mike: Thanks, Maria. Yeah, that professionalization, that need to document things and report is essential to make it work effectively. And like most things in life, the more preparation you do, the better the end result.
Just some observations from our side, I mean, we’ve already talked about this. We are the most experienced vendor in the sector for Frontline, with the greatest number of successful deployments. We’ve got deployments in virtually all the UK police forces around this.
Another point we talked about is our IT department. We’ve done a lot of work on the hardware to make sure that it’s suitable as a network tool and it passes all the security protections. And something we don’t shout about enough really, but we’ve been running Frontline technology with Kiosk and XEC Director with a number of customers for well over five years continuous uptime. There’s just been no downtime.
So this is reality, hardened police environments, law enforcement environments, where this technology’s up. So it’s extremely reliable. And we just wanted to highlight in the opportunity we had today.
So summarizing: for things for you to think about, if you are interested in this for your market, for your organization. Firstly, there’s just no one size fits all solution. We’d love to be able to ship your black box of magical Frontline, and it just open up and you unpack and it works, but that is not reality. This is a tailored solution to meet your operational requirements.
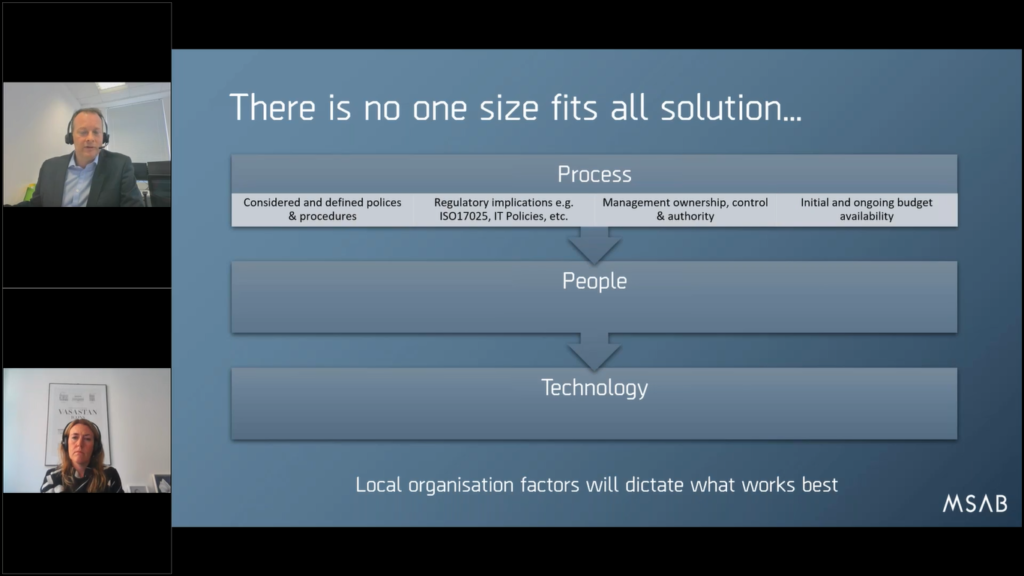
So it does need a lot of discussion and local organization factors will determine what works best, but things you need to think about: the process, of course, absolutely the people. And then the technology last actually!
Even though it tends to be exactly the other way around when we have the conversation to start with. Everyone wants to know what’s the latest kiosk made and how many processes it got. It’s like, well, yeah, that’s important, but maybe you would think about how do you want to do this first of all.
So, try and have some considered and define policies and procedures as Maria suggested. Think about those regulatory implications, whether it’s ISO17025 or your local IT security policies. Quite often, we still walk into an organization and hey say, “hey, all USB ports are disabled. You can’t have anything on the network with a live active USB port.”
It’s kind of a major problem if you want to extract a mobile phone via USB cable. So, these are the sort of discussions that need to be had internally.
Then you’ve got this whole issue that Maria mentioned about management ownership control. Sometimes we’ve encountered situations where everybody wants it, but actually nobody has control authority to decide something. So it’s worth thinking about who’s got control. What sponsors do we need?
And do you have the budget? That’s a huge thing, because inevitably there are cost considerations that may not have been planned. So, we are more than happy to talk to you about theoretical options and just give you an indication of costs well in advance, just so you can budget appropriately because when it’s public money, it needs to be considered by tender.
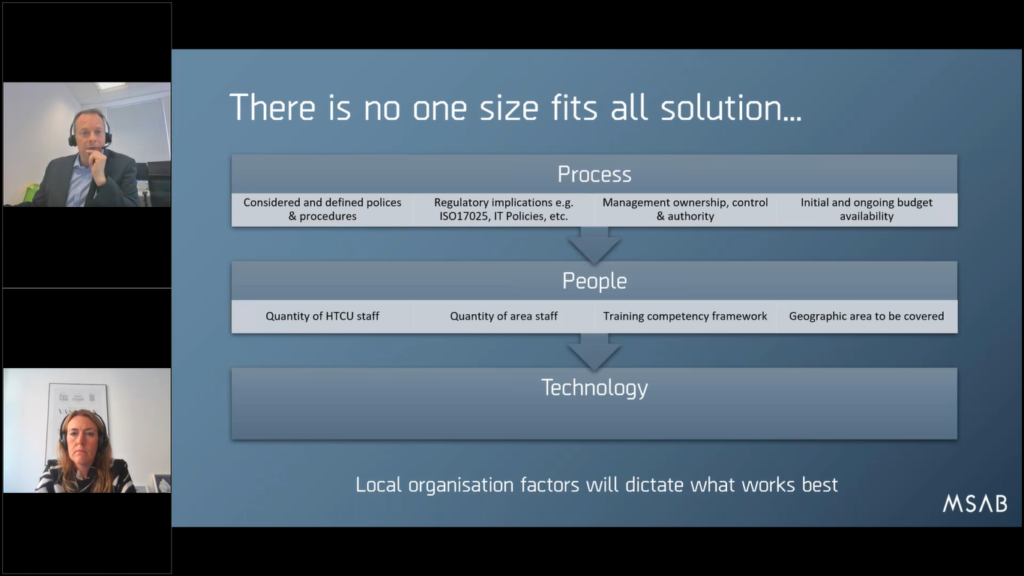
Think about the number of high tech crime staff you currently have in terms of people, because who is going to do an oversee deployment? Who’s gonna be involved in it? Who’s gonna decide what people are trained? Think about the quantity of area staff you have available, and the training competency framework. Who’s best to do what? How should you divide up the work responsibility, and of course, the geographical area?
Very often we experience churn, so that we go into a project, we deploy the technology and we train up X number of staff. And then within six months, a significant percentage of those staff who were trained have disappeared. They’ve retired, they’ve been promoted, or they’ve moved on to a new department and they no longer do anything to do with it.
So, ongoing planning for the long term and thinking about having an ongoing training budget for staff churn is important to make sure you get the best out of your investment.
And when it comes to technology, obviously think about the user environment. Where are you gonna put this hardware? Is it gonna be in the middle of a busy police station, or should you lock it in a room so it’s secure so that all the cables don’t get stolen as chargers?
Where do you put things? That’s a good question. What is appropriate technology selection for these objectives? Sometimes we get people who want to do a full physical dump of a device regardless, at a kiosk site, and we’re like, “well, you can do that, but that might tie up every kiosk for every phone up to four to six hours, if they’re big phones”.
And then sometimes there’s a point where you go, “look, if you’re gonna do something that complex and advanced, and you’re gonna attempt to try and unlock locked phones and do physical dumps, maybe it’s not appropriate that you have a kiosk. Maybe you’re actually talking about high tech crime work here, and that’s better place to do that type of activity”. This is meant to be about fast paced, easy to do phones.
Think about data handling, think about data protection. Think about data privacy and the sensitivity. Think about the fact that we are extracting data from suspect phones, and we can’t say what’s on there. Think about the need for IT department to consider the risk to malware. Might be an Android, might be an iPhone malware, but it’s still running on your network and it’s evidence that could be there, so these considerations need to think about.
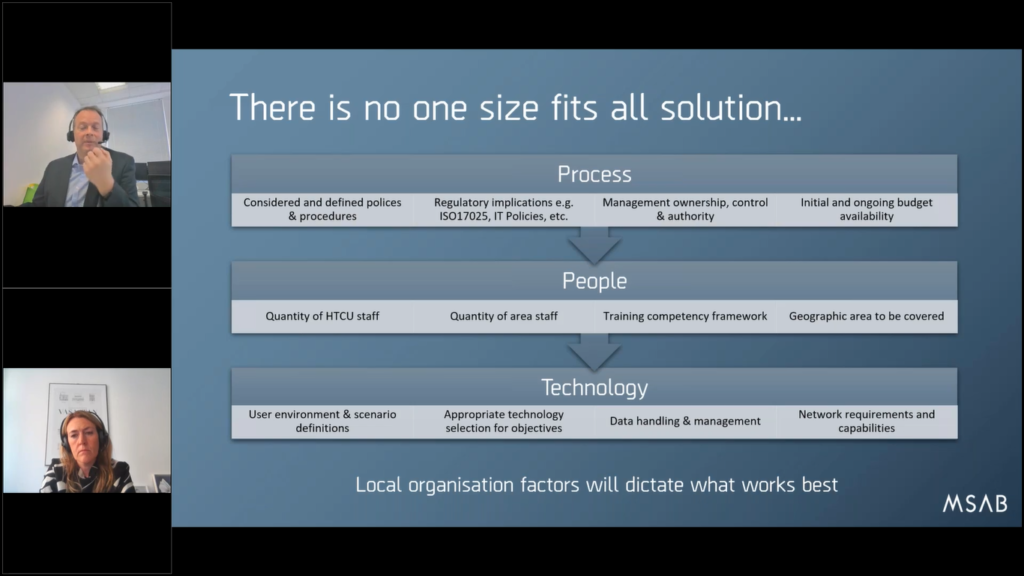
And of course, think about the load. One of the biggest…if there’s one thing that doesn’t get considered in our experience (and Maria’s gonna nod her head to this) it’s the network. Do you actually have a network that’s capable of being used in this environment?
Some police forces will try and use their existing police networks, and they were never built for this volume of data. We immediately start to choke the pipes, because we’re sending hundreds of gigabytes of data down them.
Other forces have considered it and have really gone professionally. They’ve installed their own separate digital forensic networks dedicated for this purpose, but obviously that’s significant investment cost and probably not operationally achievable for many smaller law enforcement organizations. All of these needs to be married up.
Maria, your thoughts, experience?
Maria: No, I think you’re, you’re totally right there that these really do differ from every single project that we are involved in.
And I think our task really is just to understand the customer’s needs. That that’s the main thing that we need to work a lot with with customers in the beginning and, you know, making sure that we also know what solution to recommend for the customers, because just like it says here, there is no one solution that that fits all customers.
And of course things like the roles and responsibilities I mentioned that before also that’s key also to have all that. And that’s part of all these processes, people and technology that we look into as part of the project.
Mike: Thanks, Maria. Okay. We’re moving into last few slides. So let’s summarize. Thank you all for your attendance. And the key learning points for us, from our experience of deploying frontline and in some of the busiest places in the world for law enforcement: we think early engagement with everybody, your key stakeholders is absolutely essential. Don’t just think about the DFU or the IT department. There are many other people, data protection being a big one.

Trying to decide who will own the project. When you’re crossing different departments, that can be quite the challenge. Please, early involvement with IT department, if there’s a network required because it’s not gonna happen otherwise.
And there’s a very exciting opportunity with the deployment to cloud that’s happening, and if you are…have an organization that’s forward thinking and is considering secure GovCloud type solutions, then this is a great opportunity to leap forward and never have to worry about local networking.
As Maria emphasized at the beginning, a well designed workflow that mirrors your business process is essential. We are not mind readers, so we need to understand your business process before we can build it.
So it’s a bit chicken and egg. We’d love to…we can show you what we’ve got potentially, but it’s probably worth having meetings to try and build one that works for you.
Training. Absolutely vital, just talked about that. Please, don’t overlook the training need for your own staff. And I think just to emphasize a kiosk is not an out the box solution. Don’t unpack it, plug it in and it works. There’s actually a considerable amount of work that goes into planning it.
What network is it connected to? Where is the data being stored? Locally? Central server? Cloud? What does your workflow look like? Which users are gonna be allowed to use it? What level of permission are they in authority? And what type of extractions do you want them to?
All of these questions need to be thought through. So you can’t just buy an XRY Office kit and then start to use it. It’s not the same.
Constant communication is required and it helps, especially between ourselves, but also internally with your stakeholders. But it’s also important not to just do fire and forget, run the project, get the technology deployed and then go, “oh, that was great. Thanks very much.” And everybody goes about their business.
You need to continue to monitor this once it’s deployed and look for trends, see if your offices are using it. You may discover that some kiosks are…were deployed to a police station and it’s just not used compared to other areas where there’s vast over usage, and you might be much more efficient if you were to take that underused kiosk and put it into the same police station where there’s an overworked one that’s in constant use 24 hours a day.
So the ability to see where the technology’s being used, and by how much, it allows you to move it around to where it’s needed and their requirements. And they do change over time and especially over the types of users, because you will find some staff love this and they wanna play with the kiosk all the time and do phones, and others come on the training, but then immediately find a way to disappear into the background and never actually start doing extractions.
Defining a service level agreement between all the parties does help save a lot of time. And I know that Maria and the professional service team members work on that a great deal so that we set the expectations out the beginning and it’s very much worth it.

Okay, so let’s give you an example of a customer with a real life efficiency saving. So, we had a customer who was…had a central digital forensics unit, and they were costing them well over £100,000 a year to transport that data, those devices in sealed bags, in secure environment, to the lab.
Typically it took five to six weeks from extraction and analysis to getting it back to the officer’s hands. Naturally, there’s a security risk with data being corrupted when they burn it to disk or DVD for review. And they did see that on average, they had about a 20% error rate for users when they were doing the extractions because they had a tool that basically didn’t guide them, there was no workflow.
So they started to interpret their own ways of doing things, as is the way. Confidence wise, they were relatively basic users, so some of them started to become reluctant to even attempt, and they lost confidence when they had problems and they got feedback saying, “oh, you, you didn’t do that extraction very well.”
Training was split between business processes, so we had teams in the DFU doing the extractions, but then the actual offices were doing the analysis and there was poor communication between them. And of course everybody’s impacted by cases and trying to advise those.
Then we deployed the Kiosk technology on a network with XEC Director and we monitored the results. And after Frontline, they discovered that their costs were reduced from £100,000 down to £20,000 pounds a year for a network. (That was essentially the cost, so immediate saving from transport of moving product and hardware around.) Typically they were having the results available to them within two to three hours instead of five to six weeks.
The security was enhanced because the network was running top level 256 AES encryption, so there were no worries and risk of data loss and the Information Commissioner’s Office and the data privacy offices were happy.
Error rates dropped massively from 20 down to 4% in year one, and after year two, they got so good that the error rate was literally less than 1% because we tweaked the workflow, learned from some of the mistakes being made and essentially there was no way for anybody to go wrong.
Confidence wise, well, there went from 1500 to 2000 extractions in the first year, so that’s a 25% increase in performance, because people thought they could do it. Process was taken care of. Training focused in on the devices that they were experiencing took a lot less time. Less errors, everybody successful. So we really think this industrialization of frontline can help you and help your organizations if you are experiencing a lot of mobile phones.
But you don’t have to take our word for it. Hopefully I can show you a video clip now of somebody in the Metropolitan Police who felt the same way as we did.

Maria: There is no sound, Mike.
Mike: Ah, ah, there is the technology loss! Well, hopefully you can read the graphics! Okay, this is the former commissioner of the Metropolitan Police, Cressida Dick, showing you around the digital forensics unit and the kiosk and tablet technology that’s been deployed there. And as you can see, it’s all about speeding up the process.
You can see the data, privacy considerations are being played there, and there’s a kiosk being displayed. So that’s the commissioner of the Metropolitan Police, essentially using the technology. There are around about 130 kiosks deployed at police stations throughout that region.
And they’re being used on operational basis and have been for the last five years to extract mobile data and get the evidence faster. And that’s them investing and committing to further investment this year, because it’s been so effective. So we think that’s a good working example of how this can really help your organization on a local level.
Yeah, so this is a sign off from us. This is the last slide. Thank you very much for all your attendance and those of you who’ve gratefully been listening for the last one hour and 20 minutes. Wow! Well done to those attendees! If there are any questions you wanna send anything in the chat, feel free, we’re available for the next 10 minutes and I will make sure this recording is made available to you in due course.

I saw there was one question asked early on about OTG. The only definition I know for OTG is “on the go” for USB devices. I’m not sure, because the question is literally OTG…what the question was about that. But if you want to expand or send another one, please do and I’ll try and answer that. We can handle OTG USB memory sticks, flash drives, if that’s the question…they can be examined. We can do a physical examination of them on a kiosk or a tablet, if that’s the question.
Otherwise, I thank you for listening, and if there are no further questions (just checking in the screen). Maria, is there anything you’d like to sign off with?
Maria: No. Big thank you from me as well. I was trying to see…I couldn’t see the questions. Only the OTG thing here. So it doesn’t seem like there are any more.
Mike: No. And I’m looking at the chat that looks clear. So either this is overwhelmingly brilliant and you’ve understood everything…probably another case! But if there are any questions, feel free to email. You can email…I think probably the easiest one is info@msab.com, or myself mike.dickinson. Welcome to take your questions post event, and we will hopefully be able to send you an email where you can get a copy of this recording. Thank you all for your time and attendance.
Maria: Thank you everyone. Bye.