Winner of the Best Paper Award at DFRWS-EU 2022, Nauman Zubair proposes a new memory acquisition framework to remotely acquire a programmable logic controller (PLC)’s volatile memory while the PLC is controlling a physical process.
Session Chair: Welcome Nauman, happy to have you here. And, well, the floor is yours.
Nauman: All right, how’s it going guys? My name Nauman Zubair. I’m from University of New Orleans. I’m gonna present my paper.
(I’m hoping you guys can see my screen.) Alright. My paper name is P-E-M. (You guys can see my screen, right?) All right. Its name is PLC Memory Extractor. We are multiple authors: me, Adeen Ayub, Hyunguk Yoo, Irfan Ahmed from University of New Orleans and Virginia Commonwealth University. We work in the cybersecurity lab and let’s get to it. All right.
So, industrial control system is an integrated system, which is all connected over the internet. So these gas pipelines, power grids are the physical layer of the system. And these are connected through the field devices, the PLC modem, and these act as an interface between the physical layer and the internet and…the interface layer is connected…or with the..it acts as the interface between the control layer.
And the control layer consists of HMI, engineering workstation, and the control server. Basically engineers work over there and they provide the control logic code, PLC acts as an interface, and able to integrate the letter logic and make the physical layer do the work. So these all devices are connected over the internet and as you know, is prone to attack and prone to hacks and all that.
So what is a PLC? This is what a PLC looks like. And PLC is basically have inputs. Inputs can be sensors, temperature sensors, pressure sensors, push buttons, anything. So it have a CPU, memory, and as I said before, a communication interface, which connects the control engineers to the physical layer and whatever the inputs, whatever the code the control engineers write, it interpretes it, and reveals the output.
It works in a kind of like a loop, just like any programming language. It reads the inputs and then reads the code and whatever the code is, it makes the calculation and it reveals the output and it keeps going in a loop, just like any other language, any controller, any chip.
So when it comes to PLC memory forensics, there are two types: first one is acquisition; and the second one is analysis.
So as far as acquisition goes, there are two approaches. There’s physical approach. Physical approach, you basically connect pins on the microchip of the PLC, and if you get the right pins, you will see the memory, which is a good approach, but you have to be physically there for the PLC.
And there’s a network approach. The real complication with the network is since for security PLC, they have it not…inaccessible most of the parts of the memory. So, for the security of the PLC they have designed it so you cannot access it over a network.
And this…the network approach is what we are gonna discuss in this paper. And once we have an acquisition of the memory, what can we do with it, you know? What are some examples of some attacks? Will be discussed later in the slides.
So, this is a PLC we worked on, which is Modicum M221. This is just a memory map of the PLC. This is what the storage looks like inside the chip.
So as you guys can see, the only part that accessible is this one, the external RAM, which is where the control logic code, which is the programming code, the control engineer writes. And its data objects are stored right there. This is the only part that’s accessible. Everything else is non protocol map and not accessible. So if you try to access it, it’s not gonna give you anything.
So, only part is accessible, it’s this. And with a lot of reverse engineering we got a predetermined address where, as you guys can see on the left side of that screen, which is always three from here, 70300 to…this. So we are gonna use it…we gonna use this to our advantage and to acquire the memory.
So, as I said, you know, it’s inaccessible, that these parts are inaccessible, but we are gonna use this free space, we are gonna tag it from the inside, and we are gonna use this free space to our advantage.
So, this is a design of PEM. So first is the memory map creation, which is, as we discussed before in the previous slide, which can be obtained from any vendor.
And once we have that, we have to do protocol mapping, which sounds complicated. It’s just reverse engineering and finding which part of the memory is…have the free space where the control logic goes, have to do reverse engineering for that.
And once we have that, we can make our duplicator. Duplicator basically finds the code we wanna copy from different portions of the memory, for example, on-chip RAM, if you wanna copy on-chip RAM to the external RAM, we just put the for start address to the end address to the free space.
But since free space is limited, we have to do it in blocks, and each block could be different sizes. And the bigger the size it is…if it’s a maximum size of the free space, it’s gonna take a little bit longer, if it’s smaller sizes, it’s gonna take little faster.
But then we have to make multiple duplicators. And doing that, we were able to copy all the restricted space inside the free space. Once we have that, we combine all those files and it was just bunch of machine code.
So here, as you guys can see, this is the control logic code, this is where we write our duplicator and duplicator copies any part of memory we tell it inside the free space.
All right, this is what the duplicator looks like. It’s the RX logic assembly code, which is what the PLC integrates assembly language. So it looks…so the first few lines are just to say the stack, and this is a starting address of the free space and the number of bites we wanna copy to the to the free space.
And so using that after we avoid the memory, how the attacker can use it? And so here we are gonna discuss a timer attack. So this is for the letter logic, so every control logic can…is basically, this is what a program programmer designs it. This is what their programming language. And the programming language can be broken down to assembly, that’s how PLC integrates it.
So this is the letter logic: this is basically XIC, which is input this “[EN], [DN]” is the output, in a simple sense. And it’s just a timer after 10 seconds, the DM bit (the done bit) is gonna turn on. Simple, right? Every second is gonna go and after 10 seconds, the done bit is gonna turn on.
So, this is what in the back hand, what it looks like inside the PLC. So, it runs, and if it sees a timer, it jumps to the r10 register. And when it jumps to r10 register, r10 is basically where this function calls. So every…for example, if they wanna use a timer, it just stores of address of the timer function. If it’s a counter it’s gonna have the counter function right there.
So, as soon as it sees a timer, which is a location 11, it jumps to that location and that address, and it just does the timer, and that’s where the thing happened. But since we know we have all the memory and…we did a reverse engineering and we figured out how it’s working and everything, and we use that…so we use that to change a jump address from the register 10.
And we, instead of pointing to the actual timer code, we change it to the malicious timer code that we designed. So what that timer code does: so it just jumps instruction instead of testing every single second, it jump to instruction and always returns false.
So, timer is supposed to return true after 10 seconds, but it never does. It is just, you know, it’s always false. So, this is how…this is a jump instruction. We…this is a malicious instruction report, so instead of jumping to a actual timer instruction, it jumps to the malicious timer. So the attacker has the complete control, if it’s either wants it on or wants it off, it has complete control. And it’s just how effective this attack is.
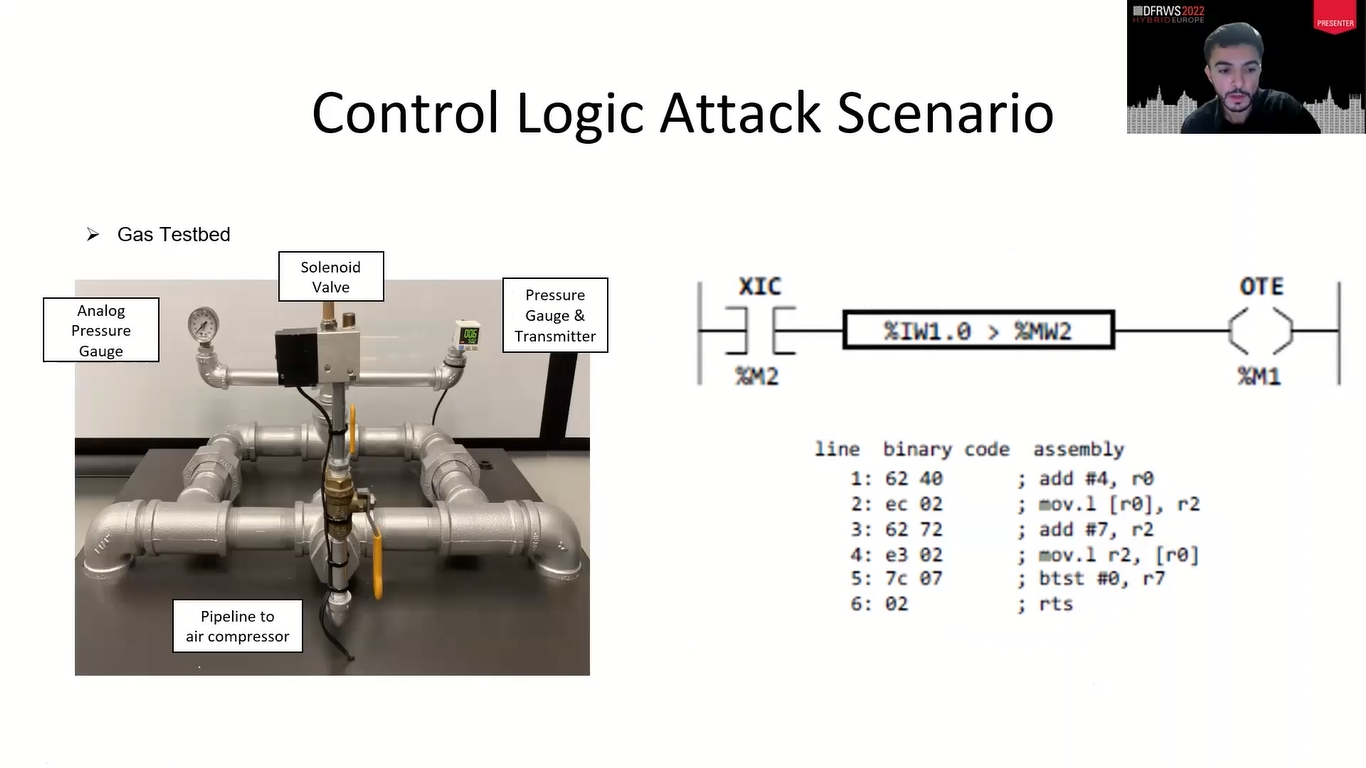
So, we did a case study. We did a test scenario in the lab where we have a gas line. It had those sensors, pressure sensors and everything in this case scenario. So what it does is if it’s over 400 kilopascals, it turns on the wall. And as soon as it reaches 600 kilopascals, it just turns off the walls to maintain the pressure inside there…gas pressure inside the pipelines.
The pipeline can only withstand so much pressure before it bursts. So it’s just handles pressure…any, you know, gas pipelines, that’s what happens in the industries. So, this is the letter logic, how the control engineer made for this gas pipeline.
So, what it does is…this is just a logic, so whenever this is greater than this, the M1 turns on. So this is a malicious code we wrote for this comparison instruction. So before we wrote a malicious code for the timer instruction, now we wrote it for the comparison instruction.
So what it does is it always sets it to true because it never does the comparison because of the malicious code, and it’s always on. And we did this experiment and we noticed it never turns off and it keeps going and we have to unplug the actual wire to turn off the process. So, the severity of this attack it’s very accurate.
So how will it actually works in the real life? So, if you do a performance evaluation, we were able to get 2.69 MB of the memory. And so when our regular gas pipeline operation, what we did before, it takes, you know, how it goes in loop, it takes, every loop goes in 331 microseconds, it takes every loop.
But if you wanna acquire the memory while it’s running, it takes 30 milliseconds every loop, which is not noticeable when it’s running it, because it’s just happening so fast, it doesn’t even realize it because it’s just checking every 30 millisecond which is still super accurate.
But if it’s a super, you know, tight scenario, we can acquire the memory blocks in smaller amounts, which will make it to 674 microseconds, which is pretty quick. And there will be no noticeable difference, even if you do it with 64 kilobytes, as I said before.
So, in conclusion we were able to obtain the entire memory of the PLC and over the network which is very great and not great. And so, we were…we introduced also two new attacks by doing reverse engineering. We were able to do former modifications inside the PLC.
So, even when the control engineer is like, “oh, what’s wrong with it?” You know, he won’t be able to tell because he’s writing the write code, but the result of the PLC is always off and he’s like…can be confusing. And that’s all guys, thank you so much for your time. I hope you guys like it. Any questions, anything.
Session Chair: Thank you, Nauman for the very interesting presentation. Are there any questions here in the room? I do have a question for you, Nauman. It is inspiring. I basically have two questions. So first question is how well does this you think generalized to other types of PLCs, I think you mentioned the type that you were doing.
Nauman: So…I’m sorry. Did I cut you off? So, how it works is, as I said, we follow the flow chart. So we have to acquire the memory map of different PLCs, which can be accessible at any vendor’s website. And once we have that, we have to do reverse engineering, which is…once you have done it with one PLC, every PLC pretty much works the same.
And once we have that, we can just follow everything. And so the only complication is we have to do it for every different kind of…every different version of PLC, different brand of PLC. So once we have that, you know, it’s…I’m not sure how secure the other PLCs are, but especially for this PLC, it’s pretty doable.
Session Chair: Okay. And now you’ve had this in a lab setting you could connect with. So what…how would you see this in…if this were a real threat how could you apply your methods? Because this is for acquiring data. I can imagine that your method can also be used for changing the software so that it malfunctions. Would that be easy, or is it only possible to apply your method in a lab setting, or would it be possible to actually do it in an industrial environment?
Nauman: So, PLCs are password protected. So if you combine two different research where you can go through that password protected loop, since PLCs are very…not very protect…like they’re designed you know, along time…10, 15, so many years ago.
So it’s not very protected in this type, in this era. So, if you can go through the password protection, I’m sure you can do this since this is only focused on the acquiring part, but if you combine two different research where you can go over the password, this can easily be done.
Session Chair: Okay. Any questions in the chat, perhaps? Okay. No questions in the chat. I want to thank you again for your presentation.
Nauman: Thank you.