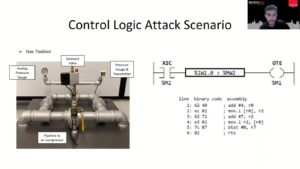
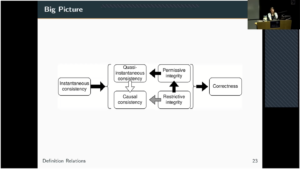
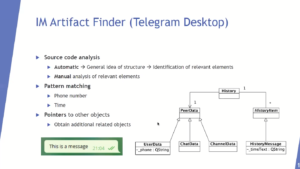
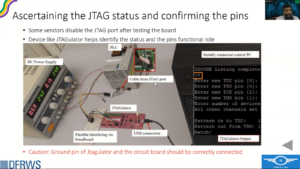
Robert Jan Mora, Principal Threat Investigator, Volexity
FF: Tell us about your background and how you ended up as a Principal Threat Investigator at Volexity?
That is an exciting story to tell, I guess. My background is that I started my career in law enforcement in the… Read more