Moving digital forensics forward in terms of methods and frameworks, as well as organizational and cross-cultural collaboration, was an overarching theme of this year’s European Union edition of the Digital Forensics Research Workshop (DFRWS).
After 40 years, mainstays like file systems, memory, and network forensics persist, joined by relative newcomers such as industrial control systems components, internet of things (IoT) devices, and even quantum computing. How to define, represent, and explain these technologies and methods were questions underlying much of the research presented.
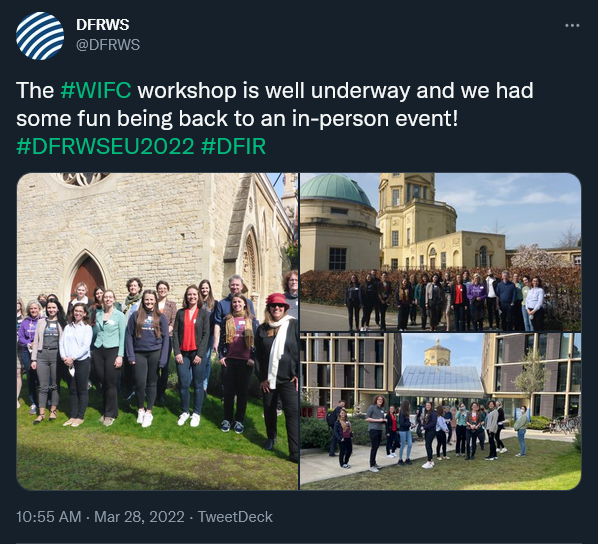
The week began on Monday with an independent event: the Women in Forensic Computing Workshop. Held at Oxford in conjunction with DFRWS, the event brought together mostly academic professionals: several dozen women and men from a wide range of countries including Germany, India, Lesotho, Namibia, the Netherlands, Slovakia, Sri Lanka, and Sweden. Together with local and international attendees from UK-based universities, they joined the workshop to hear about important research and other developments in the industry.
Presentations ranged from broad overviews of digital forensics research and requirements, to shorter and more targeted talks on specific research studies, to a full workshop on memory forensics. The full program, with links to slide decks, is available at the Women in Forensic Computing website.
On Wednesday, following Tuesday’s grouping of workshops, conference chair Chris Hargreaves was finally able to say “Welcome to DFRWS in Oxford” after two years – although he acknowledged that the virtual event format made the event more accessible to many more people than would otherwise have been possible.
In “another exciting first” for the conference, this year’s hybrid format allowed 72 physical and 72 virtual attendees from 22 countries to join the proceedings, representing students, practitioners, and vendors.
Opening comments included perspective from Helen King, principal of St. Anne’s College and former assistant commissioner at the London Metropolitan Police Service, who welcomed attendees remotely. Recalling the evolution of digital evidence over the course of her career, King spoke about the challenges that can impact the pursuit of justice, and how research helps to drive justice services forward.
Keynotes at DFRWS-EU 2022
For DFRWS’ first keynote, Serge Droz, board director for the Forum of Incident Response and Security Teams (FIRST), spoke on Wednesday about global incident response. Noting how information flowed across countries and organizations in the 2011 DigiNotar case, Droz made the point that incidents, with complex stakeholder and other human challenges, are never purely technical, and challenged attendees to think about how to cooperate on a global scale – including through in person conferences to network and brainstorm.
The following day, Emre Tinaztepe, founder and CEO of Binalyze*, spoke about traditions versus the reality of modern enterprise digital forensics and incident response. Drawing on the history of digital forensics, Tinaztepe sought to highlight current methods’ strengths and weaknesses, laying a foundation for the next era in alternative solutions.
*Editorial note: Binalyze is a Forensic Focus advertising partner.
Hands-on Workshops
A total of four workshops were offered across Tuesday, with participants able to choose between two hybrid in-person / online workshops in morning and afternoon sessions. In the morning, Tom Lancaster informed attendees about how to “Level up with YARA!” while Harm van Beek and Hans Henseler discussed “The Future of Digital Forensics as a Service.”
In the latter session, Henseler and van Beek briefly recapped data from previous research and presentations done over the last decade. They described the automation, transparency, scalability, and admissibility inherent in the Hansken platform, which they then demonstrated for workshop attendees. They also described the future and vision of Hansken as a knowledge hub not just for case data, but also research via an academic version and collaborations.
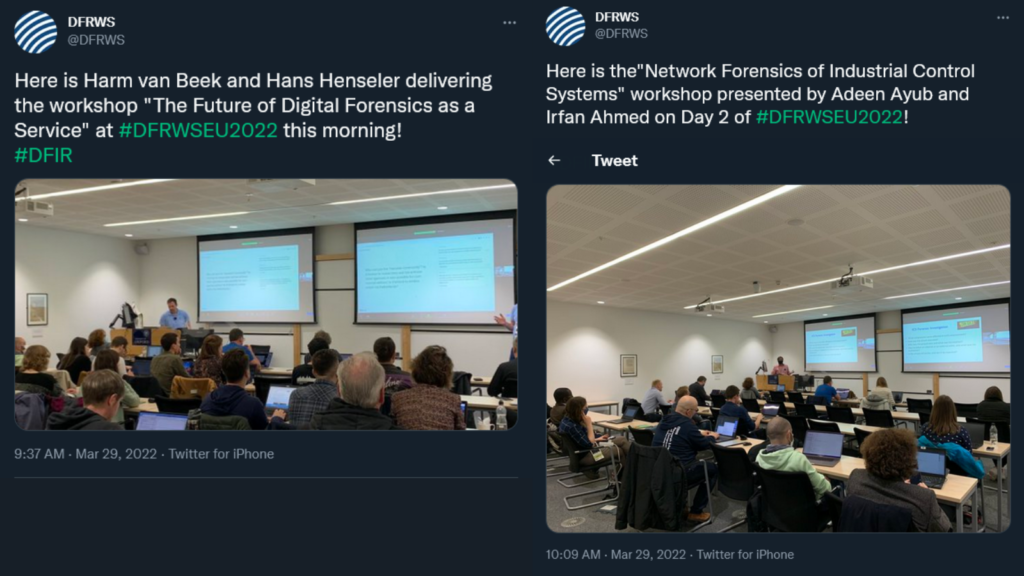
In the day’s afternoon session, Radek Hranický, Ondřej Ryšavý, Nelson Mutua offered “Cloud Application Forensics” while Adeen Ayub and Irfan Ahmed focused on “Network Forensics of Industrial Control Systems.”
The latter is part of a broader body of research by the Security and Forensics Engineering (SAFE) Lab at Virginia Commonwealth University. Focusing on the packets of network traffic between control center and field sites via communication infrastructure, this workshop allowed attendees to run their own analyses to find evidence of different kinds of attacks, including malicious control logic injection, password compromise, and physical compromise, on the proprietary programmable logic controllers (PLCs) that run industrial control systems.
Paper Sessions
DFRWS’ main program consists of full paper presentations. Four sessions covering file system, memory, programmable logic controller, and network forensics were offered, along with two sessions on forensic methods and emerging areas.
File system forensics
The first paper session of the conference focused on file system forensics and consisted of two presentations. First, Aurélien Thierry delivered the introductory talk: “A Systematic Approach to Understanding MACB Timestamps on Unix-like Systems,” his paper coauthored with Tilo Müller.
Their research seeks to fill a gap in timestamp research, which currently focuses exclusively on Windows operating systems. To that end, their paper provides quick-reference tables summarizing timestamp behavior, which can be unexpected and non-compliant in both common operations and edge cases.
Next, Jens-Petter Sandvik spoke about “Quantifying data volatility for IoT forensics with examples from Contiki OS.” Authored together with Katrin Franke, Habtamu Abie and Andre Årnes, the talk continued research delivered at DFRWS-USA in 2021.
Telling the audience that triage can be more precise if examiners can focus on devices where evidence still exists – versus having been overwritten – Sandvik described the results of experiments helping the team to address a quantitative approach to evidence volatility.
Memory forensics
In “Extraction and Analysis of Retrievable Memory Artifacts from Windows Telegram Desktop Application,” Pedro Fernández-Álvarez presented research conducted together with Ricardo J. Rodríguez, which focused on finding artifacts left in a Windows system’s RAM from an encrypted mobile app – in this case, Telegram.
The presentation included a video demonstration of Memory Extractor, a process memory acquisition tool, and IM Artifact Finder, an extensible framework to analyze those contents and obtain forensically relevant memory artifacts including account owners, user contacts, or conversation content. Both tools are open source.
Then, “Defining Atomicity (and Integrity) for Snapshots of Storage in Forensic Computing” revisited quality criteria for forensically sound memory acquisition, and proposed a new way to visualize memory towards acquiring a snapshot from a single target system.
Programmable Logic Controller Forensics
Following Adeen Ayub and Irfan Ahmed’s Tuesday workshop were a pair of papers from the same VCU team. Notably, they both won conference awards:

“PEM: Remote Forensic Acquisition of PLC Memory in Industrial Control Systems,” winner of the Best Paper Award, proposed a new memory acquisition framework to remotely acquire a PLC’s volatile memory while the PLC is controlling a physical process.
By injecting a harmless memory duplicator into the running control logic of a PLC to copy local memory contents into a protocol-mapped address space, the framework eliminates both the need to disassemble or power cycle a suspect PLC and the risk of acquiring only partial memory. The PEM framework was tested on a gas pipeline testbed, demonstrating its effectiveness identifying a new control-logic attack on a physical process.
Then, Best Student Paper Award winner “Memory Forensic Analysis of a Programmable Logic Controller in Industrial Control Systems” described PLCs’ heterogeneous hardware architecture, proprietary firmware and control software, all of which challenge security engineers to employ a unified framework for memory forensics.
To that end, said presenter Muhammad Haris Rais, researchers began to analyze the memory of specific PLCs, focusing on their functional layer rather than reverse engineer the firmware, towards finding a generic framework applicable to all PLCs.

Network Forensics
Two papers focused on communications between devices, rather than devices themselves. “SSHKex: Leveraging virtual machine introspection for extracting SSH keys and decrypting SSH network traffic,” authored by Stewart Sentanoe and Hans P. Reiser and presented virtually, described a new tool called SSHkex.
SSHkex is a low-overhead way to leverage virtual machine introspection (VMI) to allow direct memory access to a virtual machine (VM), including data from an encrypted secure shell (SSH) process. The presentation included a live demo of a monitored connection to a live server.
Then, “Knock, Knock, Log: Threat Analysis, Detection & Mitigation of Covert Channels in Syslog using Port Scans as Cover” offered a threat analysis and indicators of compromise for a novel information hiding method used by a covert command and control (C2) channel.
Coauthored by a team including both offensive and defensive security researchers, the paper’s theoretical threat scenario described adversarial use of port scans as cover, and the widely used syslog as carrier, for data infiltration. The authors also proposed a novel detection scheme relying on deep convolutional neural networks as a classification engine, in order to identify and prevent hidden threats.
Forensic Methods
Perhaps building on Tinaztepe’s keynote regarding 40-year-old methodology, three papers described new ways of looking at digital forensics.
First, “Prudent design principles for digital tampering experiments” was a critical retrospective of mistakes made in previous research. Pointing to real-life cases of digital tampering and the need to explore how it was possible, Janine Schneider presented research coauthored with Linus Düsel, Benedikt Lorch, Julia Drafz and Felix Freiling.
Schneider spoke about the lessons learned from revisiting and comparing the variables, planning, and design of both tampering and detection tasks from past studies. She offered qualitative results based on both experiments and interviews with forensics professionals, and provided advice on conducting future studies.
Notably, three lessons learned included the need for straightforward task descriptions and the involvement of experts on empirical studies, though Schneider acknowledged that recruiting them is difficult because of small class sizes and even limited capture-the-flag datasets.
To that point, “ForTrace – A Holistic Forensic Data Set Synthesis Framework” introduced a new holistic framework designed to simultaneously generate persistent, volatile and network traces. The ForTrace framework seeks to fill a gap in digital forensic training data stemming from privacy, secrecy, or intellectual property rights issues.
By extending the data synthesis framework hystck, lead author Thomas Göbel explained, the open source ForTrace can widen scenarios for training and improve ground truth datasets, all without the complexities of manual dataset generation. He called for more collaboration from the community to help with the effort.
Finally, in “Identifying document similarity using a fast estimation of the Levenshtein Distance based on compression and signatures,” lead author Peter Coates discussed the difficulties in defining confidence around identifying when two files are similar, rather than identical.
The proposed solution is an algorithm that compresses documents to hash-value-like signatures, thus allowing efficient, accurate signature comparisons where the outcome is the estimated Levenshtein Distance. The research additionally introduced a significance score for users.
Emerging Areas
The final two papers explored digital forensics issues that are not yet well understood or researched. First, “A Live Digital Forensics Approach for Quantum Mechanical Computers” demonstrated live data collection on real quantum systems to produce a quantum forensic methodology.
This is no small feat given that data, once in a quantum state, cannot be evaluated without collapsing – destroying – the data. The method described essentially reverses the flow of a fall of dominos by implementing basic gate reversal: not observing a qubit’s value, but undoing the gates applied to the qubit to get back the value you started with.
On a somewhat less abstract level, Tiffanie Edwards presented “BlockQuery: Toward Forensically Sound Cryptocurrency Investigation,” research she conducted together with Tyler Thomas and Ibrahim Baggili.
BlockQuery is a proof of concept blockchain query system for Bitcoin. It can detect transactions generated by Hierarchical Deterministic (HD) wallets that many publicly available tools cannot find. By operating on a local copy of the blockchain instead of a third-party server, BlockQuery guarantees completeness, confidentiality, and information integrity.
Short Presentations
Ongoing or recently completed research not yet published as a full paper is often offered in short presentation format at DFRWS conferences. This year, six of these presentations were offered:
- “Towards a working definition and classification for automation in digital forensics” described an ongoing PhD project in automation and AI. Researcher Gaëtan Michelet talked about basing his team’s work on the highly contextualized definitions for automation in business processes, and their plans for refining their definition, selecting rubrics, and creating a common glossary for terms relative to automation.
- “What can you tell us about your password? A Contextual Approach” followed the thread of Aikaterini Kanta’s ongoing research. Kanta reiterated the need for user context in password-cracking and described her team’s plan to fully automate their password cracking tool.
- “Bridging the Gap: Standardizing Representation of Inferences in Diverse Digital Forensic Contexts” started a discussion on inferences, their importance, and how to formalize their representation in digital forensics. Timothy Bollé talked about how the formal representation of inferences in the CASE ontology could ultimately support multiple hypotheses to avoid biases.
- “Toward Graph-Based Network Traffic Analysis and Incident Investigation” described the need to create data associations for use during network traffic analysis and incident investigation. Milan Cermak focused on robust graph data visualization of the kind that’s commonly used in criminal investigation, allowing analysts to get a broader context of incident data in a way that works for the human brain.
- “Distant traces and their use in crime scene investigation” discussed “Distant traces and their use in crime scene investigation.” Starting with a physical crime scene – a fire – Manon Fischer described how IoT devices such as “smart” plugs and thermostats store “distant traces” remotely, and could be used to help reconstruct a fire’s origin, cause, and timeline. Fischer also discussed the legal aspects of remotely stored data, which her future research will address.
- “The Wisdom of the Heap – Mesh It up by Weaving Data Structures” presented some early stage research from Trufflepig Forensics’ Aaron Hartel and Christian Müller. They talked about the volatility of data in memory as data structures change version to version.
Poster and Demo Session
Jens-Petter Sandvik returned to the stage to introduce four posters: two online, two physical.
- Roman Schell presented ARCE: Automatically Generated Test Data Sets of Instant Messenger Applications, a playbook created and used for a simulation. His poster received the DFRWS-EU Best Poster Award.
- Martin Lambertz showcased the fsstratefy framework, carrying forward Simson Garfinkel’s work to generate used file systems without incurring the costs associated with hard drive purchases. The purpose is to study variances in metadata between implementations, in order to learn how often data fragmentation occurs, generate test data for recovery techniques, and come up with ground truth for what is and isn’t overwritten.
- Francesco Servida recapped Manon Fischer’s presentation on the physical analysis of damaged IoT devices and the traces they generated before and during an arson fire. Servida also said his team is working on a resource to help analysts evaluate and manage devices found on heavy-damage scenes like the one described in the paper.
- Janice Rafraf talked about the regulation of illegal imagery and, in particular, a digital forensic keyword search strategy to get a better sense of how and when searches for this imagery are performed.

Lightning Talks
Offered at each DFRWS, these three-minute presentations are a way for attendees to talk about research or other issues that don’t require a longer talk or slide deck. Four talks were presented during this session:
- Christa Miller, managing editor of DFRWS media sponsor Forensic Focus talked about its platform’s support for educators and students of digital forensics.
- Bruce Nikkel and Mark Scanlon called for peer reviewers from industry and law enforcement, as well as academia, to support paper submissions to the journal Forensic Science International: Digital Investigation.
- Felix Freiling invited applicants to a summer school at the Nurnberg Center of Justice and hosted by the cybercrime.fau.de program (editorial note: this 18 April deadline has already passed). He also promoted some new positions in research training group for grad students looking for PhD positions.
- Holly Duns, a digital forensic analyst at the UK Home Office’s Defence Science and Technology Lab (Dstl), called for interns and collaborative partners to assist research on new and novel technologies supporting law enforcement investigations.
Social Events
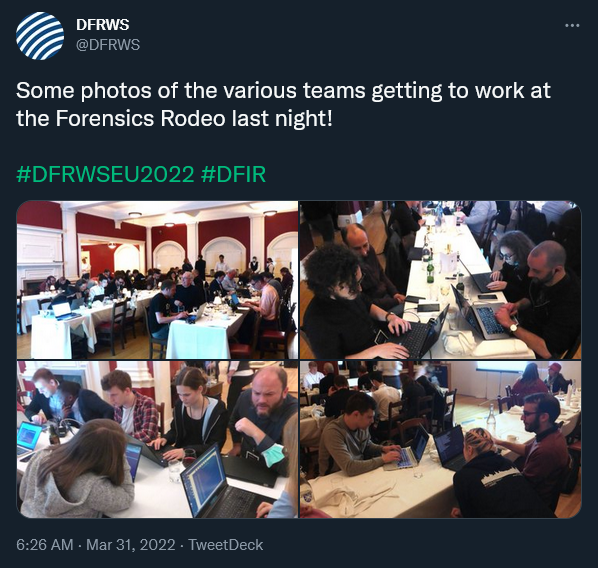
No DFRWS would be complete without the Forensic Rodeo, a 90-minute capture-the-flag style forensic competition. The “flags,” small pieces of text obtained from an encrypted disk image, are submitted by teams to score points after solving a particular task. This year’s Rodeo was held on Wednesday evening in a hybrid format.
Thursday, a virtual lunchtime Birds of a Feather session brought together researchers working on a wide range of topics: IoT, malware, memory, and network forensics, as well as resilience. Some of the biggest challenges discussed included:
- Making sense of metadata without weakening encryption, so that law enforcement can be functional but not intrusive.
- Uninformed policy without understanding technical nuances – in all sectors, but especially in disadvantaged countries and regions of the world.
- The need for educators with digital forensics expertise – and for the budgets to pay them appropriately.
- The collision between different groups ‘ interests and rights concerning the data, including who owns the data.
- The underresourcing – and underresearching – of digital forensics, and the operational limitations arising from these challenges.
BoaF attendees also brainstormed nonprofits and nongovernmental organizations that might be able to help with these challenges.
DFRWS-USA, which will be fully virtual, is upcoming July 11-13, while DFRWS-APAC, running September 28-30 as a hybrid event, has an open call for papers through May 2. Visit dfrws.org to learn more!















