Host: All right. Hello everyone. Welcome. Welcome to our first webinar, I believe, we’ve had with VFC. It’s a Teel Technologies VFC project. Just to be able to bring people to be aware of Virtual Forensic Computing and how it is able to assist you with your investigations and being able to recreate the environment of the suspect’s computer on your own desktop in that way.
So here we have Tom, who’s going to be telling you guys more about it, and I’d like to welcome him to unmute himself and begin speaking.
Tom: Hello everyone. I hope everyone can hear me, and I hope everyone’s doing well. Yeah. Just to briefly introduce myself, I’m Tom and I work for a company called MD5 here in the UK. I’m still relatively new to the industry. I only started in February. But I’m hopefully going to get across some of the benefits of Virtual Forensic Computing, which is VFC, the software that we offer here, and just how it can help and benefit you in supporting a successful investigation.

I don’t know if there’ll be time for questions at the end or anything like that, but I have got my contact details at the end of the presentation. So if you do have any questions, just drop me an email or give me a call, I’m happy to help. So we will crack on with the presentation now.
So firstly, just a quick introduction. The main tagline of VFC, for me and for everyone, is that VFC enables the investigator to see the digital data through the suspect’s eyes. And basically you can see what they see. You can see what they saw at the time. On the right hand side, you can see some of the customers that we’ve we’ve got already not just in the UK. We are in Europe, we are already in the US, and we are in Canada, Australia and some quite big names there as well. You can see the FBI, Interpol, and the Canadian police as well. And on the left-hand side, you’ve got the sectors as well. So we do law enforcement, we do government and we do the corporate side of things as well.
So onto the next slide. So VFC produces a forensically sound replicate of the target’s computer in a matter of seconds. So there are two ways to be able to virtualize that virtual machine. So one way is that we would need the hard drive. We do know that we can’t switch a laptop or a computer back on, but what we can do is we can remove that hard drive. So once that hard drive is removed, we can then connect it to a write blocker. And then what VFC will do is, it will create that virtual machine using the data from a variety of sources on the hard drive, and then we would use VMware to emulate that.
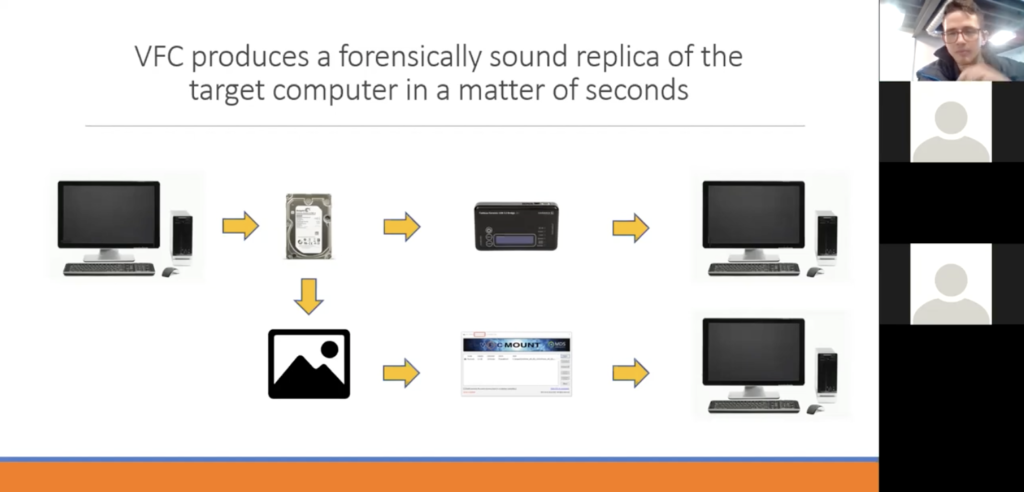
Another way to create a forensic image is to use in a standard forensic imaging tool. And once that image has been created, we would use a mounting tool to mount it into VFC. Since version five, VFC Mount has been built into the software, so we have our own mounting tool. And since the release of VFC 5.2, we also have a mounting tool available as a standalone bit of software. So you won’t need VFC to use that. So if you want to go check our website out, which is at the end of the presentation, you can download that mounting tool for free, and you can use that without any license or anything like that.
Once the virtual machine is created, using VFC you can create a standalone copy of a virtual machine. This can then be used without VFC, as long as the computer has VMware. And this essentially gives you a portable copy of that suspect’s computer. So you can have a play around with it, if there isn’t a better term for it, to have a look in all the files, to have a look at all the settings, et cetera, without any consequences to that original forensic image.
VFC doesn’t do anything you can’t do yourself manually. However, what VFC does do is, it saves you a lot of time, and it does present that evidence in the easiest format and the easiest way possible. VFC does all the hot fixes in the background. I like to say that VFC has a lot of experience in building the virtual machines and overcoming problems, such as the blue screen of death or driver errors, and all this is done with the click of a button. So it saves you a lot of time as well.
Anyone can use VFC. I like to use myself as an example, like I said at the beginning, I haven’t even been in the industry for a year yet. But all you need is basic computer skills to use VFC. Everybody knows what a computer looks like, if you’re in this industry at whatever level, you’ve worked with a computer before. And if you’ve got those skills, you’ll be able to use VFC.
It’s also important to point out that VFC is also ACPO compliant. And it does adhere to the ACPO principle one as well. So it is up to standard. And I’ll be touching on this later as well, that it does only take minutes from start to finish once you received that hard drive. So then having a play around with that suspect’s environment, you’re looking at minutes instead of hours, potentially days.
So on to the next slide. So you, as in a virtual machine, can help explain the technical evidence. This is where I think VFC is absolutely fantastic. So you can put the screenshots and screen capture videos into reports, into your technical evidence. What VFC does do is that it helps maximize the credibility and the impact of that evidence by demonstrating and illustrateng the confusing narrative that can be present in court.

Basically, in court a technical report can confuse the judge and jury with the jargon included in that report. If pictures are embedded in the report, then this will help illustrate and explain in a more general sense. 99.99% of the time on the jury, you’re not going to get people that are clued up on the industry in terms of phrases used, in terms of the jargon used. And you might get people that are going to get bored and not take anything on board.
Text reports are subject to interpretation as well. Not just from the jury and judge, but from the analyst creating the report. So the point of the judge and the jury reading the report are screenshots of the actual desktop is black and white. There’s no interpretation and it’s right there in front of you. And as the saying goes, everyone knows the saying, a picture paints a thousand words. Anyone who’s seen a computer screen before understands and can identify a desktop.
VFC is also useful in identifying a timeline of events. And you can see clearly when a computer was last booted up, to things such as when files were last edited.
So all this brings us to saving time. So like I previously touched on, embedded screenshots into the report will help reinforce the credibility. Also it helps saving time on writing up a report as well, because you have actually got that evidence in data format. You can actually use VFC live in court to play screen capture videos as well, to help explain unfamiliar concepts. There have been cases in the past where this has actually been done. So I’m not just saying that as if, like, you could try this; it has actually been done so you can definitely do it.
You can also show a suspect their own computer, especially in interviews. Everyone knows that you’ll get difficult suspects that might not want to provide any information and might deny everything, but if something there is black and white in front of them, that is their own, it’s very difficult to do that.
Also, I’ll touch on this a bit later as well, but you can remove and bypass the passwords with the in-built password tools that we’ve got in VFC. Again, this leads back to, if you have a difficult suspect unwilling to give correct passwords, VFC will be able to get around that, again with just a click of a button. And we all know that time equals money. And so where you are saving that time, saving those hours, saving those days, creating minutes instead, you are saving money in the timeline as well.
So onto the next slide: gathering the evidence. There’s loads of different ways you can gather evidence. Before I go into it as well, I can imagine that you’re all thinking of different ways that you can search a computer, or search a desktop, of all the different places you can see that evidence.
So you can check the jump lists to see what has recently been added and accessed. You can see all the file properties, you can see where the files were created when they were last modified, if they were modified, and when they were last accessed. Again, this can be done manually with different types of software. There’s no getting away from that, but VFC lets you view this in the easiest way possible, without any interpretation, without missing anything, which is what everyone wants, at the end of the day. People want to be able to do things in the best, easiest way possible without any interpretation getting in the way.
You can also check things such as the wallpaper, I know this may seem a bit silly. But there have been cases in the past where there has been indecent images as the actual screensaver of the suspect’s computer, which obviously again, that is obtainable using different software, but it is so easily obtainable and presented using VFC. Again, there’s no way you can get around that is black and white. You can see it at face value. You can see it for what it is.
You have peer to peer software. You can have a search on that, to see if anything’s mid download, mid upload, or if anyone’s sharing any sensitive data. You can also go into the settings in the software and see if they’ve been changed. Obviously if they have been changed, this would show intent, which can go towards providing the evidence in court.

Again, cleaning software, someone may track to cover their tracks. Again, this would show intent. You can have a look at all the settings. You can have a look at when it was last set to clean the computer, the hard drive. Again, that would obviously go towards the evidence that you present.
You’ve got hidden files. Someone may have created those hidden files. Again, this can be easily obtainable using VFC. I’ve already said it, you can do it using other bits of software, but VFC puts it in such a simple format to gain that information from, and you can actually see what the suspect will have done for themselves in the way that they would have done it.
Again, these settings show intent. So whether there’s something in there or not at the time you are searching for it, if those settings have been changed, quite clearly, something has gone on in the past, whether that is legal, illegal, or something of that nature.

We have antivirus software. This can be checked to see if any recent scans were done, to see if anything’s in quarantine. You may get someone saying that “I didn’t put this image on this computer. Someone else put this image on this computer, that virus put this on the computer.” We can see if a recent scan has been done, actually no, no malware or any viruses on your computer. So you’re shooting them down straight away, and basically verifying what they’re saying is incorrect.
Onto the next slide, again, this is gathering evidence.
Host: Tom, Can I interrupt you really quickly? We just have two questions and I wonder if you can address them.
Tom: I can certainly try my best.
Host: One is: Can VFC remove or discover a BitLocker password?
Tom: There is a way we can get bit round BitLocker passwords. I’m not 100% sure personally how it’s done, but if those people want to take my details at the end, I will get back to them and give them a bit more information on it.
Host: Yeah, I can take their name too, so we can get an answer to them later on.
Tom: Perfect. It’s definitely achievable. It definitely can be done. How it’s done, I don’t know personally, but I will definitely get that information and feed that back to them.
Host: And then, second question, can VFC virtualize a Linux machine?
Tom: It can indeed. The reason… as far as I’m aware, it can do pretty much everything. So you’ve got Linux, Solaris, Windows, it can do pretty much all. I do know if it can’t, we fix it pretty much straight away, so it can. So again, we are constantly developing VFC. It’s not just something that we’ve created and left alone, it’s something that we are constantly developing, constantly trying to improve to meet everyone’s needs. So, yeah. Linux, as far as I’m aware, we’ve never had a problem with that. It does build that virtual machine and have no issues.
Host: Okay, cool. Sorry for interrupting.
Tom: No, it’s all right. No problem.
So yeah, onto the next side. So using existing software on the machine. Again, I’ve mentioned that this is just another way of gathering that evidence in a more corporate sort of environment rather than maybe a law enforcement environment, and this may be more applicable to that side of things.

So this applies to any sort of software that requires a license. With VFC, the software can be used as long as it had an active license when the machine was last used. So an example is accounting software, for example, Sage and Quickbooks. Should the computer be seized within an active license, VFC will create the virtual machine from the point it was last started. This is where VFC comes into its own. Some cases may be 12 months old and beyond before the hard drive can be examined with VFC. The virtual machine is booted up at the point of the computer and laptop was last used. So that won’t be an issue.
In order to aid within the investigation, VFC also allows you to set the virtual machine to a specific time and date as well, to keep you within that license. So there’s no panic or anything like that, of that license running out. You can use it. Again, you can use that version of the software rather than having to download the latest version and it not transfer over properly. You’re using the specific software that the target’s computer used. So again, to that tagline, you’re viewing it as what that suspect would have viewed it, how that suspect would have used it, sorry.
VFC is also useful when it comes to proprietary databases and software. VFC can utilize a software and databases that are created and are developed in house. For example, a company I used to work for before this one had a specific bit of software for the service that they offered, which there’s none like it anywhere else. Now, using other software to try and use that would be near impossible. With VFC, using the software that they created in-house, you are viewing it as they would have last viewed it and played around with it as they would have been able to. So you don’t need that software installed on your machine because it’s built into that virtual machine.
A feature as well as of VFC is that you can drag and drop any file from the virtual machine. So for example, if you want to export any databases from Sage or QuickBooks into an Excel format, you can simply just drag that from the virtual machine onto your own desktop. And then you can use that in evidence or pass that on to a solicitor or something like that, for them to have a look at, which obviously then counts towards reports and investigations.
As well, I’ve touched on this, a suspect could say that malware has altered the hard drive, malware put the files on there for them. You can actually use VFC to clean install malware and use that virtual machine as a sandbox environment. So you can install that malware onto it, see what it does, without impacting the host machine or the original hard drive. And so you can get down to the nitty gritty to see if the suspect is telling the truth, at the end of the day. You can also see website history, bookmarks, favorites, what’s been last accessed, just to add to that investigation as well.
So onto the next slide, restore point forensics. So you can rewrite rewind the virtual machine using restore point. The best way I can describe restore point, which quite a lot of people listening will already know, is that it’s like a checkpoint in a game. For example, if you have cleaning software installed and you suspect this may have deleted crucial evidence, then you can use restore point forensics to restart a virtual machine to a risk previous point before the software was downloaded. However, this is dependent on the settings. Again, if the settings have been changed, this would obviously show intent, which goes towards the report and the investigation.

There is a case that that MD5 actually conducted and had a hand in before I started, around terrorism. There was a case where a hard drive was checked and it seemed clear, but MD5 did use VFC to boot up the virtual machine to a previous restore point, and this showed applications and links to known terrorist sites, which obviously again, is put in an easy format for you to be able to gather that evidence and present that evidence in court.
And onto the next slide. So in-built password bypass tools and password reset exploits give rapid access to the user’s desktop. So there are two password tools built into VFC. So we have the generic password reset tool and the password bypass tool. So what GPR is, which is the generic password reset tool, what that does is it permanently removes a password from multiple accounts. It also converts Live ID accounts to local accounts, and then it also can activate admin accounts as well. So it gives you access to those admin capabilities, et cetera.
The password bypass tool can remove the password for one session using an exploit to make Windows believe it has the password. So they are similar in what they let you achieve, but there’s two different ways of doing it. You can remove that password, or you can just bypass that password. A new feature of VFC 5.2, which has only been out just short of a couple of months, I believe, and it means that you can also select an option to convert Live ID accounts to local accounts and to reset all the passwords while the virtual machine is being built.

Again, VFC saves you time in the first place. We’ve managed to develop VFC where it saves you even more time. So it gets rid of those passwords without you having to do anything. Again, this is an automatic, you have to take a couple of boxes, but it is as simple as that. Yeah, it’s just such a big time save. And this is what VFC is all about.
So just to summarize, before I go into a couple of case studies where VFC has been used and come into its own. So benefits of having VFC: you’ve got triage, you can quickly see if a hard drive is required or not. This can be done in the field as well. There’s no disguising the fact that there are triage tools out there that are specific for this task, but VFC gives you enough information to see whether you need a hard drive or not to take it back, to see if it’s worth taking, which I’m more than happy to provide a demo to people afterwards, if they want to get in touch with me, we can start a demo out so I can show you how that can be done.
Avoiding errors. Like I said near the beginning of the presentation, VFC has a lot of experience in overcoming errors in building a virtual machine. VFC knows what it’s doing. Human error is removed from the process. And then obviously that leads to maximizing that credibility of that that evidence as well, which is obviously the next item.

Screens are black and white. You know what you’re looking at. You know what a screen looks like. You can see the screenshots in the report. You can see videos.
Again, this is the first I’ve touched on that, but versatility and capability. VFC is designed to work alongside other forensic software. It’s not designed to replace. I’m not here to try and pull wool over anyone’s eyes. Other software out there is fantastic, but putting VFC alongside that obviously goes towards maximizing that impact and credibility of the evidence. And at the end of the day, that is why we are in this industry. We are here to put our point across, to make sure what we are present in is 100% fortified.
Again, a safety net. I haven’t touched on this, but I’ll quickly touch on this now. VFC creates a log of everything you do, and this can assist with the contemporaneous notes. Again, it also lets you create a standalone virtual machine that can be used to have a play around with, to explore that virtual machine without risk of harming the original VM as well. Which you can create multiple copies of that. So you, again, if you want to put two different types of virus on there, you can put that into there and see what both do without impacting that virtual original virtual machine or hard drive.
And the big one, which I’ve mentioned a few times, is time and money. We’ve talked about saving hours, days, throughout the timeline. Those hours and days that you spend doing it, VFC will be able to do it within minutes. We all know, again, that if you save time, you will save the money.
I’m quite passionate about this tool. I know I’ve got to be because I’m the one that oversees it. But when I say it is a must have tool, I really believe that. And like I say, I’m more than happy to give you that demo of how it all works and everything like that for you to see it firsthand, rather than me just try and force it upon you. I’d rather you see it for what it does so it can sell itself.
And then that’s pretty much the end of it. So I will go into a couple of case studies really quickly now. And it just gives you an example of a few things I’ve touched on and the benefits that I’ve touched on.

So this first case study is surrounded by QuickBooks. This is an example of how proprietary software is used in the real world. And this shows that VFC is art is always being developed. So bullet point 4, you can see there that when we launched each VM and bypassed the password, using the bypass tool feature with VFC, we were unable to bypass one of the machines. So we quickly fed that back to our software developer, and that was pretty much rectified straight away. So that problem will never be encountered again.
Again, exporting files and copying them from the virtual machine on your own desktop, onto your own data storage device. And that can be seen in the last paragraph when they then contacted the client and asked what information was going to be of relevance to their case, we generated custom reports within the virtual machine, and then we were able to, to feed them back to the client.
More details on this case study is available on our website; again, if you can’t navigate that, which I’d like to think people will be able to do, if you just want to drop me an email, I’m more than happy to go into more detail into it.

And then there’s this final case study, which is an extreme example, but I think it’s such a perfect example and I hope everyone else can see that as well, of where this can be used elsewhere. There was a case study done in Oklahoma City, and it was a cold case. It went pretty much dead. You can read it for yourself. No body was ever found, all evidence was entirely circumstantial. Based on evidence taken from the computer, cell phone, friend’s statement.
VFC was introduced within this investigation and it was quite obvious what happened here. They convinced the DA in this case to allow them to actually bring a laptop and project it into the court and let them build on the suspect’s computer, using VFC and VMware, and it made all the difference. The jurors were able to get past that technical report, get past the jargon, and see it for what it was. So booting up an image of the hard drive, you could see what it was. You can see highlighted that we were able to see how the icons were organized on the desktop. All of the internet history was clear, internet chat programs, emails; so easy for everyone to just digest that information.
As you can see from the non highlighted parts, you could see text files that taught them how to dismember bodies; roast full size pig carcasses; which obviously are all led to this case being solved in the end. And just a quick quote from our customer at the time: “Never before has Oklahoma County being able to successfully prosecute a no body case, and VFC was actually the software that drove this home.”
Again, I don’t want to force VFC upon you without showing you how it works. So please get in touch with me. I’m more than happy to get a demo. I’m happy to work around you. You just tell me when you want a demo and I’m happy to give you it.
And that’s it from me. So if you guys have got any questions, fire away, if not, thank you for listening.
Host: Yeah. We have a couple of questions and people seem to be writing them into the chat. I don’t know if you can figure out how to get there. It’s on the bottom bar.
Tom: Let me have a look…
Host: Or I can tell you them right now.
Tom: You may have to read them out to me. Yeah. Technology!
Host: One is, can I import a VDI into VFC?
Tom: I’m not 100% sure to be honest. I’d love to be able to answer that. I will have to ask our technical team on that one. Again, if you just want to drop me a quick email with that question. I’ll go back to our department and get all the information that I can.
Host: Yeah. Tom, why don’t we just send a follow-up email?
Tom: That’s perfect. Yeah, that’s perfect. That sounds great for me.
Host: Cool. Just going to make a note of that. And then the next question is: when using the password bypass or resetting option, are all files accessible without ownership restrictions?
Tom: Yeah. So you’ve got those admin rights that you can access. So you will be able to essentially view, like I say, view it as they would’ve been able to view it, so you can change the settings and everything like that. So there’s no restrictions in there. You can view essentially what you want.
Host: Okay. And there’s no more questions. I’m just going to leave it open for another minute, just in case. Yeah. But cool. Yeah. I really appreciate it, Tom. Yeah.
Tom: Again, like I say, I am passionate about VFC. I’m not just saying that because I’m the salesman for VFC, I’ve done so much research into it before I even started. I use it every day, even though I’m not a technical member of the team, I do use it every day to try and find new ways of how it can be used. Like I say, I know I only touched on it a little bit, it’s such a versatile tool. It’s just being able to experience it for yourselves which hopefully I’ve touched on today.
Host: Cool. And that shows. We’ve got one other question that came in. Would password bypass work with application protected apps?
Tom: No, I don’t think it does. I don’t think it can go that far into the system to get rid of those. So it’s the Windows Live ID that it can do, but apart from that, I don’t think it can access anything else, unfortunately.
Host: One question that the person is asking, when can we expect follow-up on the initial first two questions?
Tom: Go on, sorry.
Host: Can we just promise them sometime tomorrow?
Tom: Obviously there’s a bit of a time difference. So you should receive an email from me before you guys wake up. I don’t know what the time is here. It’s currently half past five in the afternoon here, so yeah. I’ll look at those questions straight away and feed back to you in our a.m. So you should receive them as soon as you arrive at your emails in the morning.
Tom: Perfect. And then more questions. So, hang on, folks, you’re welcome to stay everyone, or you can leave, do whatever you’ve got to do. But one is, will VFC work on cell phones?
Tom: No, it doesn’t work on cell phones, unfortunately. I don’t see why we can’t look into it in future. If there’s a demand there, then obviously we can look into it, but there’s nothing in the pipeline at the moment for that sort of thing. It’s strictly just laptops, computers, et cetera, at the moment. But I will feed that back to our software development team. Obviously, like I say, if there is a requirement for it, we’ll certainly look into it.
Host: Okay. And then here’s another one asking if it will–
Tom: Apologies. Apologies. Just to go back on that. I just had a quick thought: if the phone has actually been backed up on the computer, those files are accessible. And again, like I keep saying, you are viewing it as how they would have viewed it. So yeah, if the phone has been backed up on there, you can view the files that way. If it hasn’t, there isn’t something in place for that at the moment. But again, if you really think there is a market for that, then we’re looking to it and see what we can do.
Host: Cool. And then there’s someone asking if it will exploit shadow copies?
Tom: Not at the moment. But we are putting… I think there is something in the pipeline for that. So we are looking into it, and hopefully that won’t be too far away. So keep an eye out.
Host: Okay. And that seems like all the questions. Thank you, Tom.
Tom: No problem. Thank you everyone. I hope everyone couldn’t understand my accent because I know it’s not a typical British accent. So I hope I got all my words up properly for you guys.
Host: I got it clear. My mom is from England, so it’s no problem.
Tom: And if that’s it, I hope you all have a fantastic rest of the day.
Host: Cool. You too. Bye-Bye.















