Flashpoint, a business intelligence agency specialising in the deep and dark web, recently published a report on the economy of criminal networks online. The report looks not only at where criminals go to communicate on the internet, but also how their communications are structured, and the ways in which online communication has changed the criminal landscape.
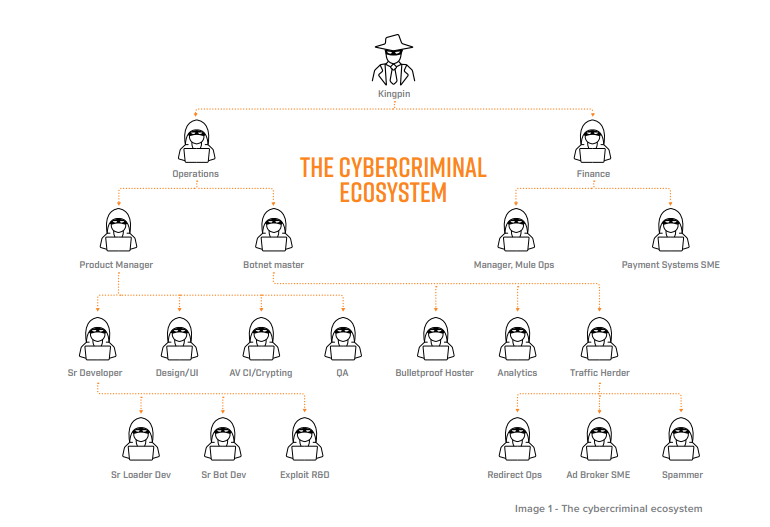
Far from the kind of jack-of-all-trades portrayed in TV dramas, today’s cybercriminals structure their operations much like a business, each person having their own specialisms and reporting to the people above them. This helps to ensure that every member of the network takes on tasks that don’t overwhelm them, and often also ensures that the level of communication is kept to a minimum. Each party is only in contact with the level directly above, thus decreasing the likelihood of breaking up the entire network if a single individual’s identity is uncovered by law enforcement.
Naturally, cybercriminals meet and communicate online, but this is not without its risks. In general, the preferred method of communication is through web forums or message boards, which allow members to talk to one another and also access previous conversations between other members, so that the site gradually becomes a resource for the criminal community.
Of course, this is a risky business, and law enforcement agents are constantly on the lookout for ways to take these forums down. For this reason, the message boards tend to move frequently, experience sudden unscheduled down times, and are precarious places to store data.
It can be challenging to find the ‘right’ communications platform for a criminal enterprise – such things as language, ease of use, and of course anonymity, must be taken into account. When Flashpoint’s researchers looked at the data, they discovered that the top places where information was being shared were ICQ, Skype, Jabber, AIM, Telegram, WeChat, QQ, WhatsApp, and Kik.
The findings differed by country – full details can be found in Flashpoint’s report, a link to which is provided at the end of this article. There were, however, some points that were relevant across all territories.
While forums are hugely popular in the cybercriminal realm, nowadays they tend to be used more as meeting places than as spaces in which to conduct business. Criminal A might meet Criminal B on Forum C, and the two might get to know each other’s preferences and abilities, but any communications regarding actual crimes will generally be held somewhere away from the original forum in which they met. The main reason for this is mistrust of forum administration – as accounts of police taking over and running criminal networking forums become increasingly popular in the news, criminals are in turn becoming more careful about whom they speak to and where they choose to hold their conversations.
Moving conversations to popular services such as Skype and WhatsApp, however, presents less risk to those who want to ensure covert communications due to a sense that their conversations are not being read and monitored by an anonymous administrator who may have ties to law enforcement. Of course these services are not foolproof either, and it is possible for criminal activity to be uncovered here, but where private messaging apps are involved, evidence from these communications tends to be uncovered after the fact, i.e. when a criminal’s device has been seized.
Of all the instant messaging services used, Skype was by far the most popular across the board. The global trendsetters seem to be the Russians, who are known in criminal networks for their technological prowess and so tend to lead the way in terms of deciding which platforms are going to be increasingly popular.
When deciding on a means of communication, criminals have many of the same criteria as the average person. It is important for the service to be easy to use, ideally with as few bugs as possible and a good balance between security and usability. While the popular TV trope of a cybercriminal navigating a complex web of code every time they want to communicate with their criminal buddies is well-known, it has little basis in fact. Criminals, just like the rest of us, want to conduct their business as quickly and easily as possible, without compromising too much on security.

Having said that, security and anonymity naturally remain of high importance in criminal communications. Depending on the level of technical knowledge and sophistication of the persons involved, such questions as whether end-to-end encryption is used; in which jurisdiction servers are located; whether users can verify contacts’ identities; and whether the code is open to independent review are popular concerns. Alongside these lie more basic questions such as the service’s privacy policies and how much information is collected from users when they sign up.
But it’s not just criminals who worry about things like this. Increasingly, members of the public are becoming aware of the privacy options they have and how to exercise them, particularly since Snowden’s NSA revelations in 2013. This makes it harder to distinguish between users who want to keep their communications private for the purposes of hiding criminal activity, and those members of the public who are simply not fond of the idea that their every move might be being watched.
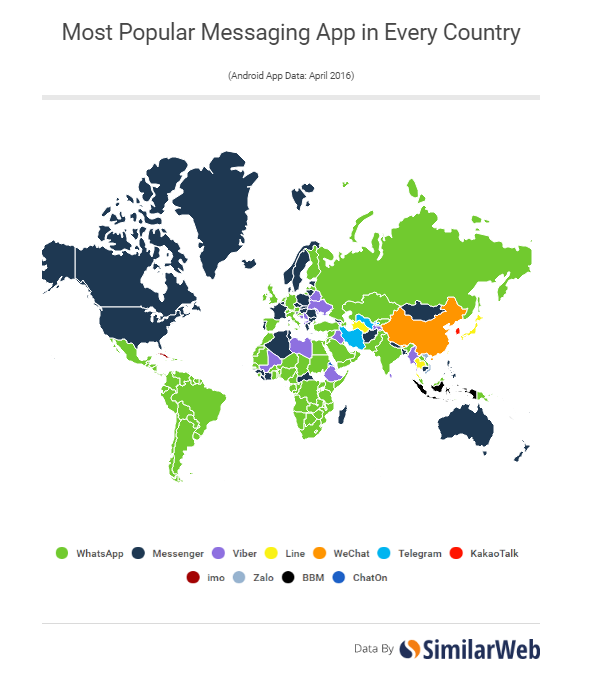
The overall findings of Flashpoint’s research seem to support this. In terms of how they communicate, criminals aren’t very different from the rest of us. They look for a balance between privacy and convenience; they follow trends and use what their friends and contacts use. Russia seems to be leading the way in criminal communications online, and this is perhaps the only way in which criminals differ from the general population. For example, the use of ICQ as a messaging platform has significantly decreased among the vast majority of users, while it has actually increased in usage among criminals. A study conducted by SimilarWeb in 2016, which showed the most popular chat applications worldwide, didn’t feature ICQ at all.
However, Flashpoint’s study found that this service is still popular in Russia, and is growing in use in criminal networks around the world. In late 2016, Mail.ru, which bought ICQ from AOL six years earlier, started to invest heavily in new features within the app, including photo manipulation and “Live Chats”, aka chat rooms which allow users to interact with other people based on topic or geolocation. The fact that these chat rooms are easy to use and feel relatively anonymous makes them a popular place for criminals to move their communications once they have initiated contact via a forum or other means of introduction.
Simply keeping an eye on which messaging services are popular in Russia and extrapolating criminal communications trends from this doesn’t seem like a useful or easy way forward, however. For now, it is generally more realistic to uncover criminal communications data in the course of a given investigation, rather than preempting it, in the vast majority of cases. It is also worth remembering, like the results of Flashpoint’s study showed, that criminals are much like the rest of us in their expectations and requirements: they are looking for technological solutions that are easy to use while also being as secure as possible.