Charles: Hello everyone. Thank you for joining us for the Nuix Investigate power user webinar. My name is Charles Klein. I am product manager for Nuix Investigate, and I am joined today with my colleague Gareth Bernard, who is one of our solution consultants, and he is going to do some talking about cross collaborative casework and how you can use the features in Nuix investigate to set cases up and to work collaboratively in your organization.
A little about Gareth: he’s worked in digital forensics and investigations for more than a decade. He’s previously worked at a UK based service provider, and he’s done hundreds of cases for law enforcement, government, legal, corporate, and defense. He’s also had roles such as analyst. He’s done R & D as a technician. He’s also done CCTV analysis, been a lab manager, and he’s been with Nuix for about three years now. I’ve worked with Gareth quite a few times on projects and he’s really knows his stuff. So I’d like to introduce him now. Thank you, Gareth.
Gareth: That’s great. Thanks, Charles. And welcome everyone to the webinar. We’re going to talk, as I said, a little bit around Nuix Investigate, but specifically how we can utilize this technology to collaborate more within our teams.

So we’re looking at Nuix Investigate: what it does, where it sits. Why is specifically iInvestigate beneficial to your investigations, to your workflow? This is going to be just a handful of slides just at the start of this. And then we’re going to just propose a hypothetical scenario and look through some some demo data that we have within Nuix Investigate itself and go through a bit of a demo about how this kind of cross collaboration technique you can actually go forward and benefit you.
Then at at the end, we’ll have some time for some questions. So if anyone has any questions, please please direct them into the chat, and then we should be able to pick those up at the end, and answer those for you at the end. So Nuix Investigate. Hopefully you know a little bit about the product already, but if not, then essentially it is an assistant products for our kind of core piece which is Nuix Workstation, Workstation being the kind of powerhouse that does all the processing and deep dive forensic analysis.
Nuix Investigate kind of sits alongside it as a weapon to face front end for for doing your investigations. It’s still utilizing the Nuix engine in terms of being able to do the searching across that you’re used to, being able to filter on your different file types and named entities and the like, but also allows multiple people access to the case at any one time. And you can define that access based on different security settings, different feature settings. So you can configure your case based on item and feature security for particular users.
You’ve also got a dashboard view allowing you to put in multiple different analytics to allow you to see your data in perhaps a more meaningful way than just looking at [indecipherable] on a screen.
In a Nuix lab environment, you would have your Nuix Workstation set up for the purposes of processing. You can also do all your analysis and review within Workstation if you need to, but it’s only allowing you one user at a time to be able to look at that information.
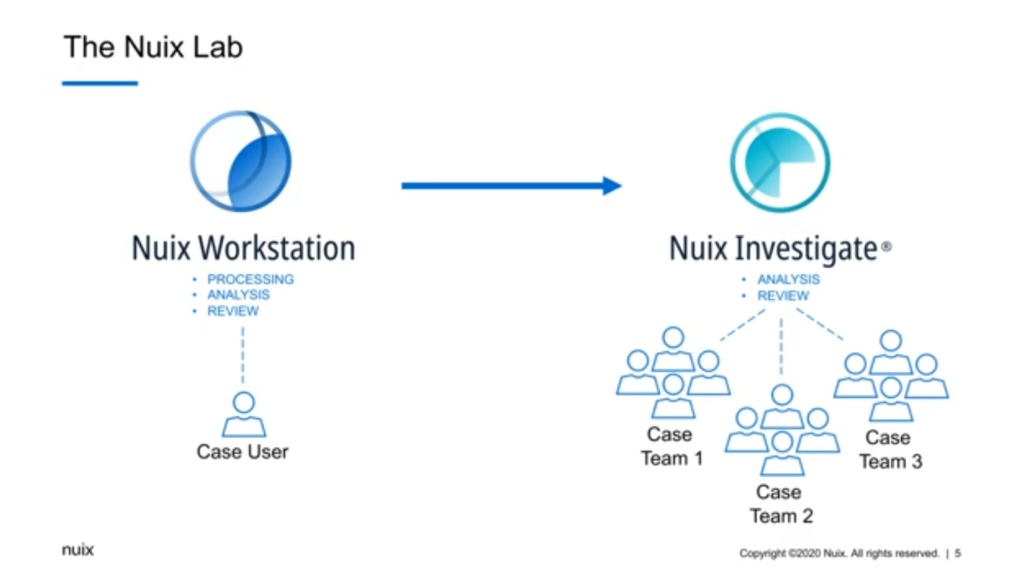
Nuix Investigate, sitting alongside, [indecipherable] the processing which Workstation will do, uou can do your analysis and review, and you can also spread that out across multiple individuals and multiple case teams. So not just multiple people, all doing the same kind of job, but other teams that are potentially doing different jobs.
And that’s really important, because investigations — whether you’re looking at it from a law enforcement angle, or a corporate, or an ediscovery or GDPR angle — investigations are often very large in scope. The digital part of an investigation may actually be quite small. There might be a lot of things behind the scenes: people talking to each other, various different other machinations going on that aren’t necessarily part of what would be considered to be a digital case. So we need those people to talk to each other. You’ll probably find that any work you do nowadays anyway, you’re working in teams and you’re cross collaborating in certain ways over various projects. So this is not a new concept to any of us.
But us being able to look at that information in a digital form collaboratively potentially is. Big data as well is… it’s much larger than a single person can really deal with anymore. As Charles said, I’ve been in the digital investigations industry for more than a decade. So I do remember a time where there was any investigation would probably be a single person and a single computer or device. That doesn’t really exist anymore. You’re looking at terabytes of data across multiple different sources. So you need the additional support of multiple people. And no one person is a master of everything. We can all utilize different strengths and specialisms better when we work together as a team.
So let’s have a look at a scenario. Now I appreciate this is going to be a slightly more law enforcement focused scenario. That’s just simply because it’s one aspect that we might be looking at in terms of digital investigations, but you can apply this this kind of model and this idea to any type of investigation, however you want to be looking at it.
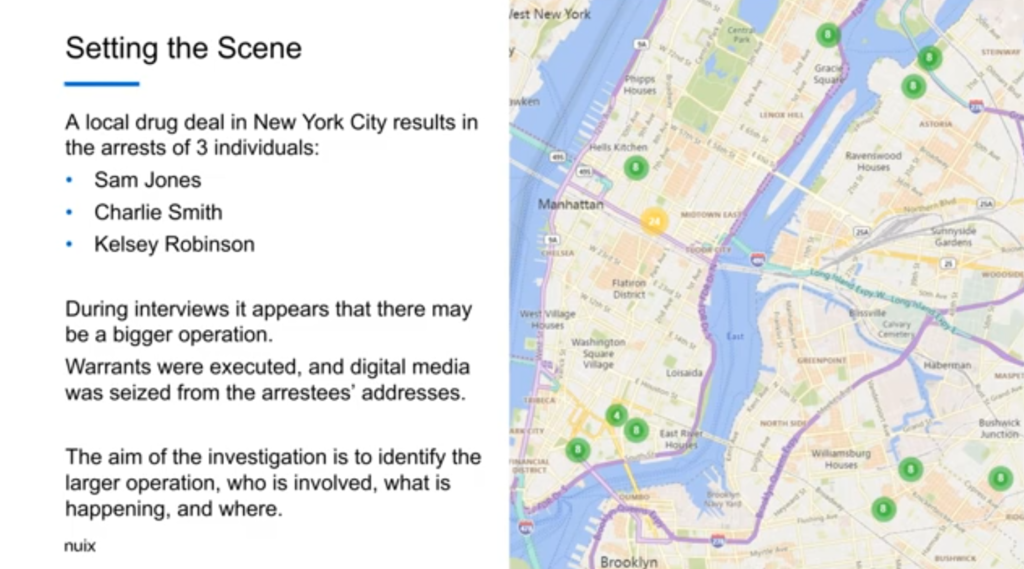
So we’re setting a scene very simply. There was a local drug deal in New York city that resulted in the arrest of three individuals. Three names here: Sam Jones, Charlie Smith, and Kelsey Robinson, for argument’s sake. Now, as the investigation continues, and during interviews, there seem to be more going on than just the simple drug deal that was identified. So warrants were executed. Digital media was seized from the addresses. And so we have a fuller case, filled with with various devices. And the aim of the investigation is to identify if there is a large operation, who is involved, what’s happening and where that’s happening.
So the investigation itself: I’ve kind of devices demo to show you a case, the idea of maybe five different teams that would integrate with with this data, with this information. So we have an early case assessment team that essentially goes in to exclude irrelevant items, to run specific workflows and assign items; a communications officer who is looking at communications data to identify connections; a forensic investigator who perhaps has more access to areas of the case, knowing their forensic background; a reviewer who’s looking over documents and coding them as such; and perhaps a case manager that is reviewing the status of a document review.
So I’m going to share my screen now, and hopefully this comes up okay for everyone. So I’m just in the web front end login screen for Investigate. Now I’m just gonna make that full screen just so it’s a little bit easier. So we’re going to start off with our early case assessment team. So we’re going to log in with any case assessments user. And we’re going to think Diamond Data, that’s the case that we’re actually going to be looking at in this instance. We’re going to search across the case and look at this dashboard that you set up, change this over to our ECA view.
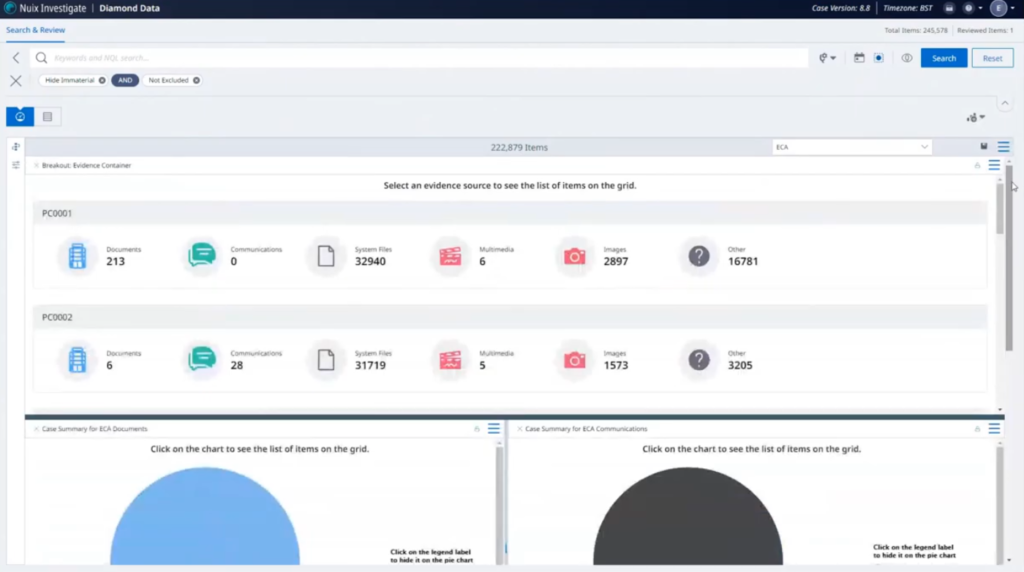
So here we’ve got some things set up so we can see an overview of the case itself. We’ve got a number of different items within here, and we’ve got documents and communications. We’re probably going to allocate those out. Got a lot of system files and things… we probably don’t really need those for the purposes, this investigation. So maybe we’ll exclude those from some workflows.
And down here, we can see just a representation of items that have been put into folders for the review by other teams. At the moment nothing is in folders, so we don’t have anything there. And we don’t have anything that’s been searched and tagged across. So let’s go open up our grid view, look at our search filters.
So we’ve got our documents review communication, this review here, but I think before we want to do that, we want to start excluding some items. So want to go into my workflows and to exclusions. And I’m just going to run this. This will exclude any system files and other files that we saw in it. While that’s running — so it might take a few moments — I’m going to filter my documents for review.
Let that load up in, be a grid view. And I’m just going to assign this out to our documents folder.
Okay. That’s great. And the exclusion has finished running as well. Let me do the same thing for our communications, and we’re going to assign that to our communications folder. I’ll just add that in.
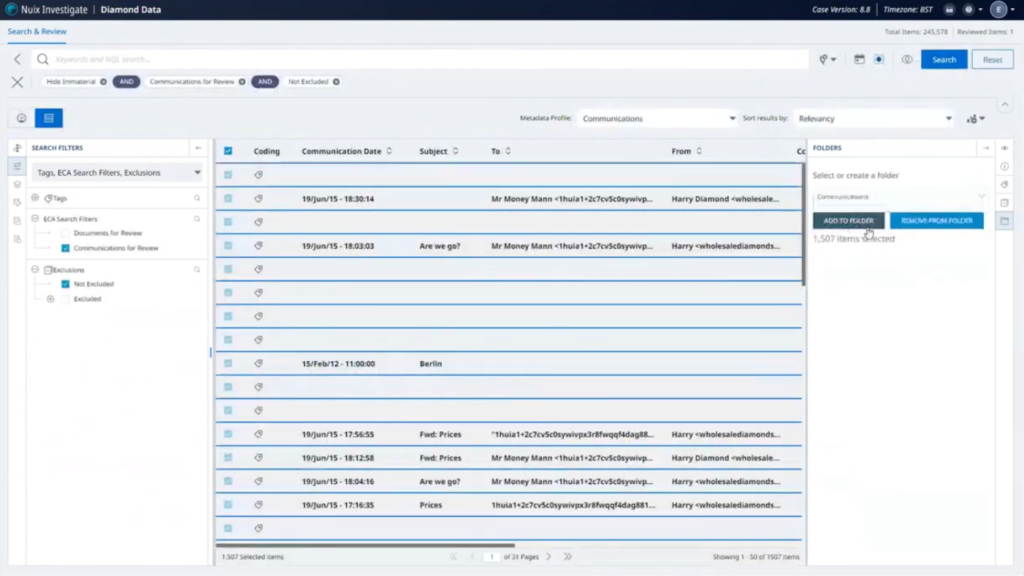
And then one last thing we’ll do is, on the workflows, we’re going to do our search and tag. Now, this is just a set of search keywords that we’ve set up as part of a general case that we’ll run. We’ll just run that across the whole case and tag any any relevant items.
Let’s go back to our dashboard and refresh how that looks. So on our ECA look, let me just refresh our various views here, let those all repopulate.
Okay. So we can see these loaded in now we’ve got communications in the folder. So all the communications in the case now are in the communications folder. There’s some documents that are still not within a folder. This may be documents that are not considered reviewable in the strictest sense. So we might want to look at those in a later form. This breakout has now updated our system files and other have gone to zero because they’ve been excluded from the case. So what we’re looking at is the important data now.
And then we have an overview of different search terms that have resulted in keyword hits that have also then been tagged. So that’s the early case assessments officer’s job done for this moment. So I’m going to log out as them. And we’re now going to go in as our communications officer, we’re just going to log in the same way.
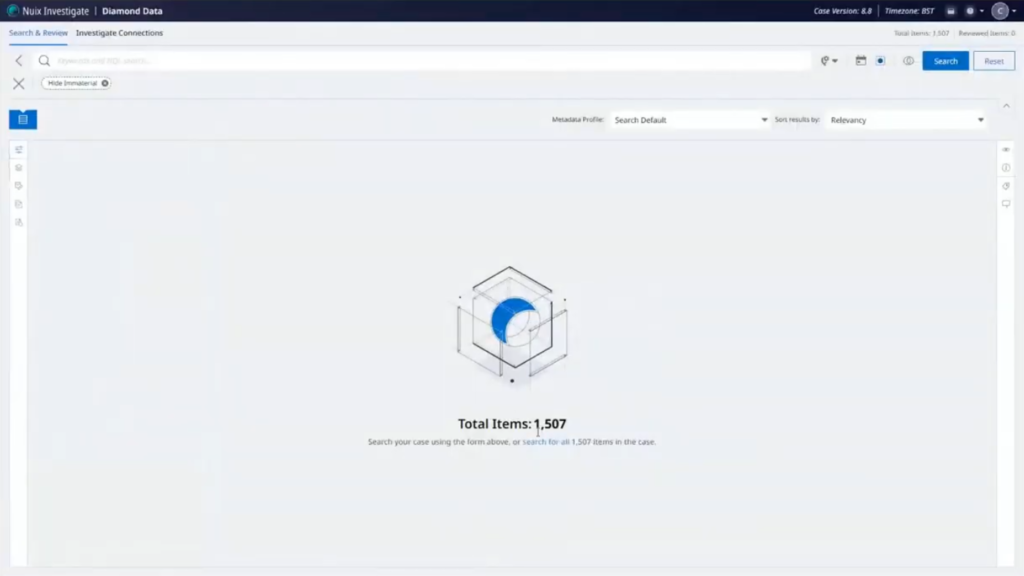
They only have the Diamond Data case available to them. So we’ll go straight into that one. And now we’re looking at it much more stripped down view. They only have the communications folder with updates that are available to them. All we’re going to see is the communication states. So emails and chats, conversations from from mobile phones… I’m going to select these and send these out to our canvas view, to look at the different connections. This will bring out all the different connections and how they’re connected into each other.
We’re going to want to filter down on a little bit of this. Specifically, we have three suspects. We have three phone numbers. So I’m going to start creating some people objects. So this makes a little bit more sense to us as we’re looking through it.
So I’m going to filter on this phone number to start with. Great. So we’ve got three options there for us. We have a phone number, and we’ve got deleted messages, got iMessages specifically. So I’m going to create a person here. So this is the phone number that relates to our first suspect, Sam Jones. So we’re going to create that person. Great. So that’s there.
I’m just going to filter it on the other keyword now. So that’s the phone number relating to Charlie Smith. Again, similarly, we’ve got a few options there, so we’ll select those, and we’ll create the Charlie Smith entity. Great.
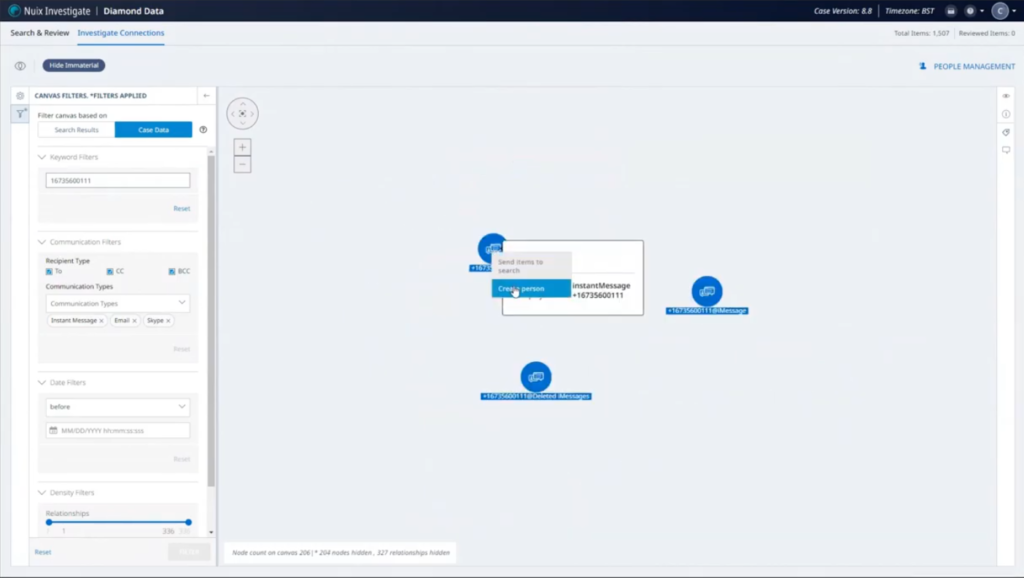
And one last person that we had available, and that was our Kelsey Robinson. Search… yep, a few more items. Going to put in the name here, give that a high level of confidence and create the person. I’ll just reset that view. And we see now we’ve got some purple objects here that now relate to those specific individuals, but at the moment, this is a bit messy. We’ve got all the communications within this case here. There’s a lot of communications where there’s only one piece of communication going elsewhere. We’ve got things like junk mail messages with no additional context, that might be not that interesting.
So going into our relationships filter down here, we’ll just filter by a minimum of five relationships we want in our view. Okay, so that’s great. That’s cleaned things up much better for us. So we can see up here, this kind of cluster of individuals. We know these people are talking to each other.
So we’ve got some conversations between Charlie and Sam, actually quite a lot, and we are going to take one of these and see what’s been discussed. Okay. So we’ve got things to talk about. We’ve got white powder. We have your gear here. So they’re talking to each other about the kind of selling and dealing of drugs. And we know that was a likely scenario. And let’s have a see what Charlie and Kelsey are also talking about? Yeah, we’ve got similar kind of thing here, obviously white powder, et cetera.
So we do some more investigation into the additional people that are talking to these three individuals. And maybe we’ll find more people to talk to you, more people to interview that night. And one thing that comms officer is aware of that perhaps no one else on the team is, is that during interview Charlie Smith, for reasons not known to other people kept referring to himself as ‘The Geezer’ quite a lot, potentially just from watching a lot of average gangster flicks.
So they’re actually going to search for that in case there’s any kind of communications that seem to relate to that. And in this instance, there is we have a Diamond Geezer 94 at Skype accounts. So we’re going to add this to the Charlie Smith entity here. Perhaps we have a low level of confidence where we don’t know a hundred percent this is the case, but we’ll just save that in there. Let me reset.
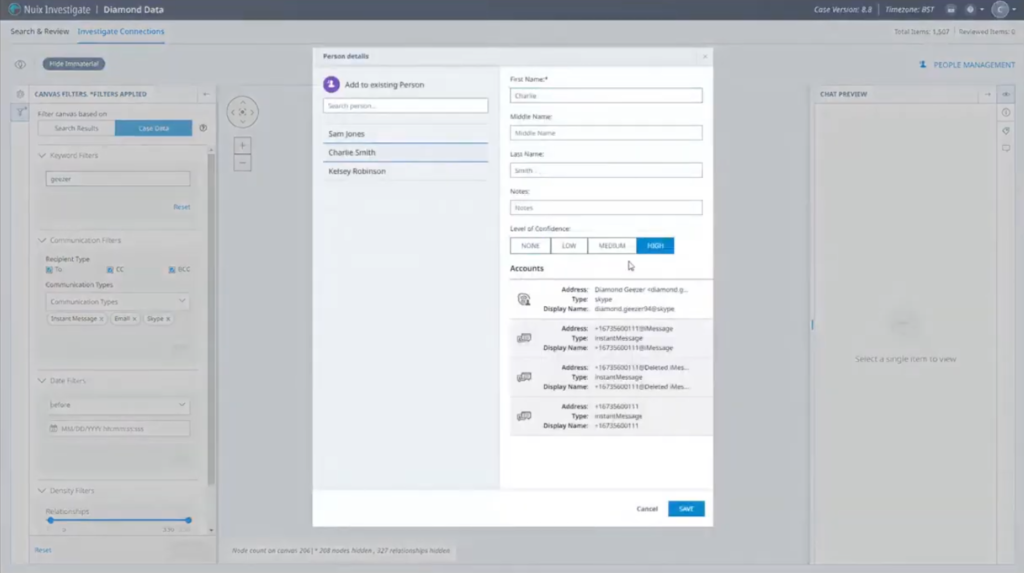
I’m going to show you now, if I go back to the standard search and if I was going to do other work on this case, I need to send all these items back to the canvas. These things do persist. So these areas, these people that I’ve created, are now persistent across the case.
I’m just going to reset that relationships filter back to five, and getting that redrawn. So it’s a little bit easier to see.
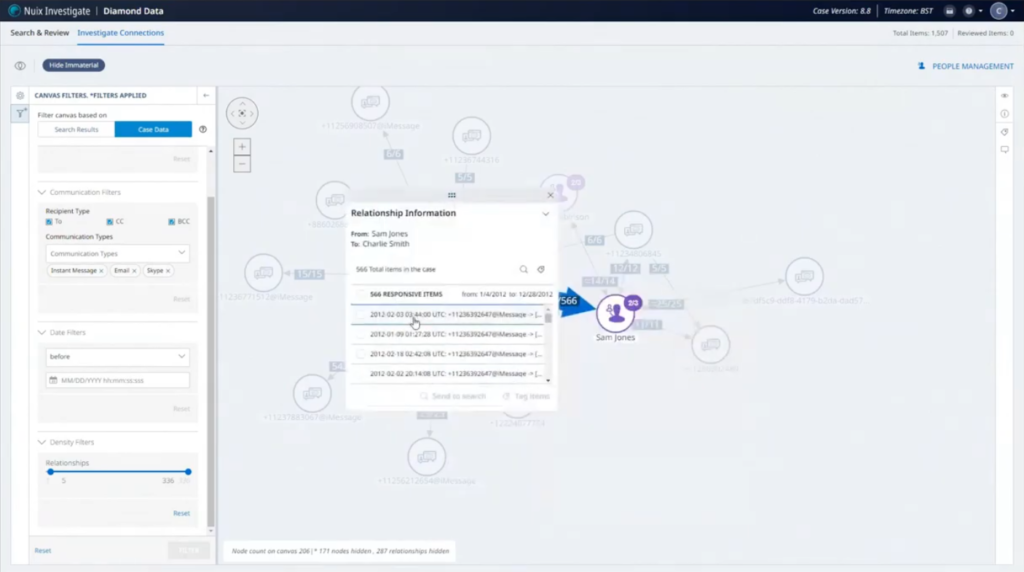
Okay. So we were looking at the conversation between these people and now we’ve added the Skype account to Charlie Smith, if I expand that out, we can see the different accounts we have within here. Now you’ll notice that there is this other Skype account that’s now attached to it. We click on here and look at the conversation between these individuals, and we’ll scroll up. We’ll have a look and see what they’re talking about here. So we’ve got this Moneyman contact. I scroll down, we’ve got some very large amounts of money being discussed, more than a local drug dealer would probably be invested. We’ve got a name called Albert coming up, a website from Cody Holdings. Okay.
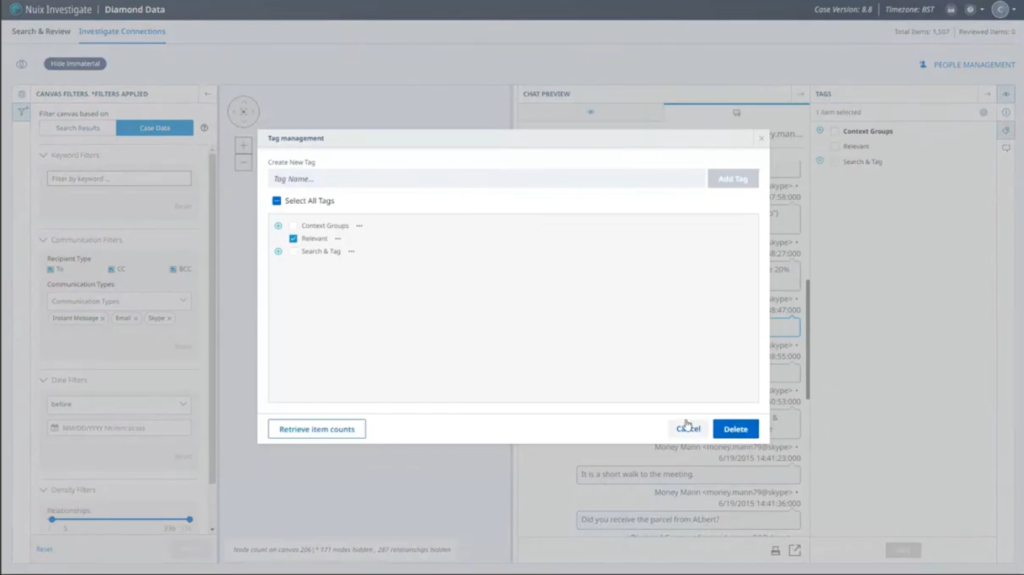
There’s an Excel spreadsheet. That could be quite interesting. The comms officer doesn’t have access to that at the moment because of permissions. So what we’re going to do is… we can see there’s talk of Sierra Leone going on here. So very, very far from New York local drug deals. So we’re going to tag this. Just set up a new tag. I’m just going to call that ‘relevant.’ Then we’re going to save that tag for there. And we’re going to add a comment to this particular item. We’re going to tell whoever’s looking at this app to check out the spreadsheet mentioned in this chat. Also search for ‘Sierra Leone.’ That’s great. Comment’s been saved successfully. Commes officer second, can go away and do whatever work he does.
But at the same time, we’re going to now log into our forensic investigator account. And with that, we’ve got few cases available to them. Open our Diamond Data case again.
Okay. So this this individual has — or his team, rather — has access to all the information within the case, multiple different ways of looking at that data. We’ve got a search filter here for putting out anything that’s been newly tagged or commented upon. And so we have a singular item that we just put a tag in a comments against. They can have a look through here. Just have a look at what the comment is, because we’ve got this right here, checking the spreadsheet. You mentioned that. Okay. Great. Sierra Leone. Okay, cool. So the investigator is going to have a look through this chat now and see, okay, great. There’s the Excel spreadsheet. So let’s copy this out, we’ll reset the search, and let’s search across our case for that spreadsheet. And maybe we’ll get lucky and maybe it exists… and it does. Perfect.
So we’ll have a quick look at what that looks like. And we’ve got some prices and things in here. Actually that’s not super useful at this moment. Let’s look at the PDF version. That’s gives us a bit more context. Okay, cool. So this looks like a price list for diamonds for various cuttings. That’s something we find new and interesting, and we don’t need to tag this. It’s already been tagged by the individual. We’ll put another comment on it just to say this is relevant, so if they need to look at it at a later time…
Now we’re also told to look at Sierra Leone. So let’s reset that and do a quick search of Sierra Leone. And we’ve got a number of documents and items that have come up here. We’ve got the chat we were looking at before. What have we got here? If we look in our preview… some article from Stanford about blood diamonds and the history of diamonds. Interesting.
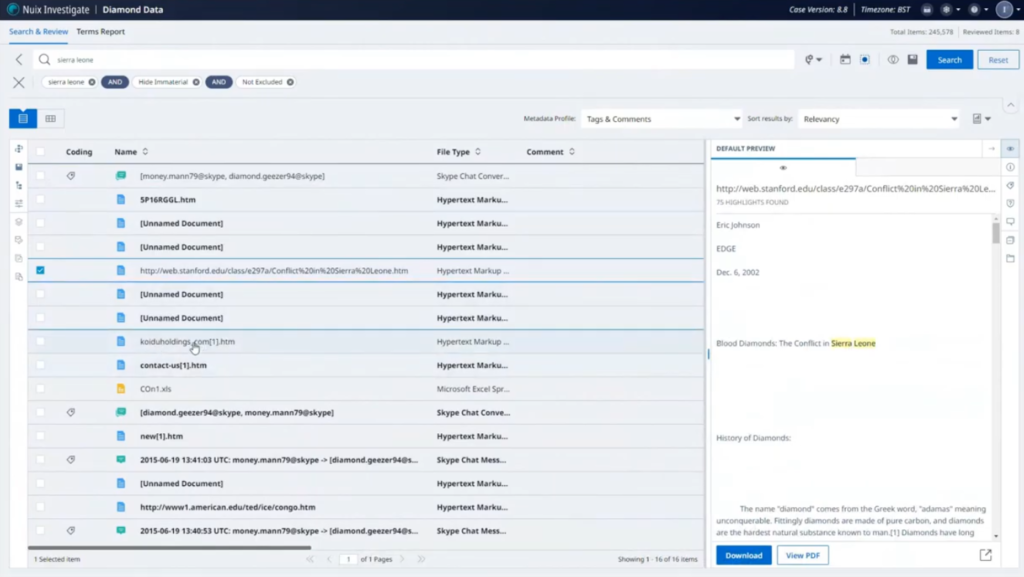
Okay, Koiduholdings.com. That was related to in the chat. This looks like a diamonds mining or selling website, and so we’ve got a cached small amount of webpage there. Also got an Excel spreadsheet here. Don’t know much about that. Let’s bring the PDF view of that as well. So we’ve got this list of countries, Sierra Leone is in there, and we’ve hit upon what we’ve been looking at. And some mines. Okay. So these might be locations, names of diamond mines. Okay. We’ve got a list of people here, and this could be useful. Some contact information. We’ve got some email addresses… okay, great. This is definitely something we’re going to want to tag. We already see that a relevant tag has already been created, because the comms officer did that. So we’re going to save that against that particular item.
And we’ll just put a comment about it, just in case anyone’s looking at that particular item again, they’ve got a bit of information surrounding it. Okay. So the comms officer and the investigator have got to work quite closely together and carry on. But in a kind of separate track, our document reviewer, or team of document reviewers, will be looking over the documents that have been allocated to them from the early case assessment.
So we’re going to log in now as our reviewer and see what their kind of experience of this case is like. So they only have 1200-odd items to look at, documents that have been assigned to them. We’re going to go to our search filters, look at documents that haven’t yet been coded. So out of the 1200, we can see at the bottom here, 684 items still remain that haven’t yet been coded.
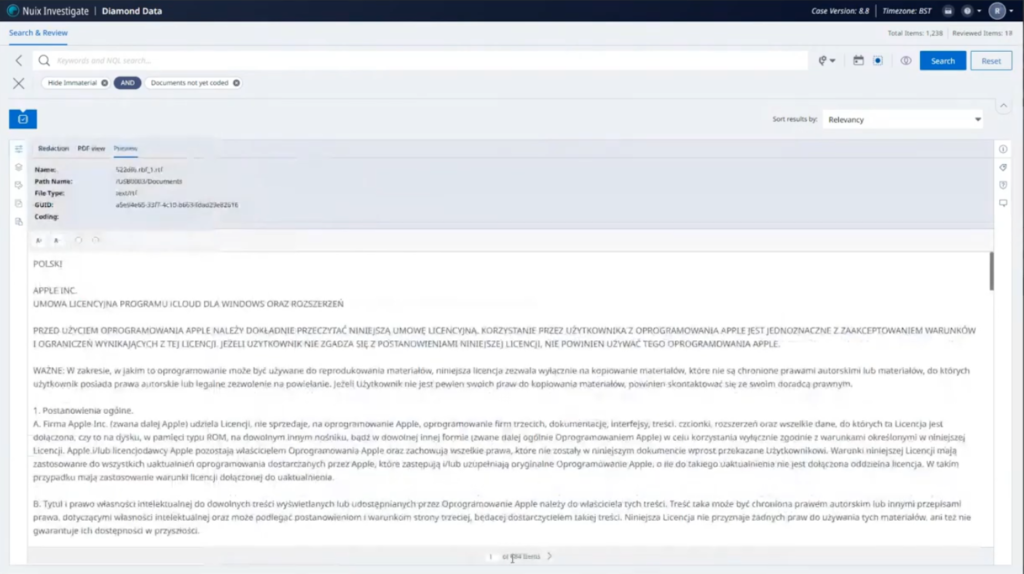
We’ve got some secure fields here, some kind of coding information that we can do for each of these items. This one looks like it needs translation. So let’s choose translation. Doesn’t contain any redactions. Let’s go on to there. We’ll do the same thing here. Probably going to find quite a lot of these. For argument’s sake, let’s just say that these aren’t relevant. Let’s say this one needs to be for further review.
Let’s say this one was relevant. It contains some information about drugs, and we’re going to put a redaction on it. So I can have a look at the PDF views of these particular items. I can now choose a markup set, and I can redact certain information so that when we come to export that out, that’s going to be redacted. So that’s great. So the reviewer would continue doing that until they had finished their assigned documents. While that’s going on, the case manager could be looking in to that case. To see how far along reviewers and the case as a whole is getting on.
So we’ll log in again. And now they will have their dashboard view available to them. And we’ll switch that over to the case review dashboard and have a look at some of these analytics.
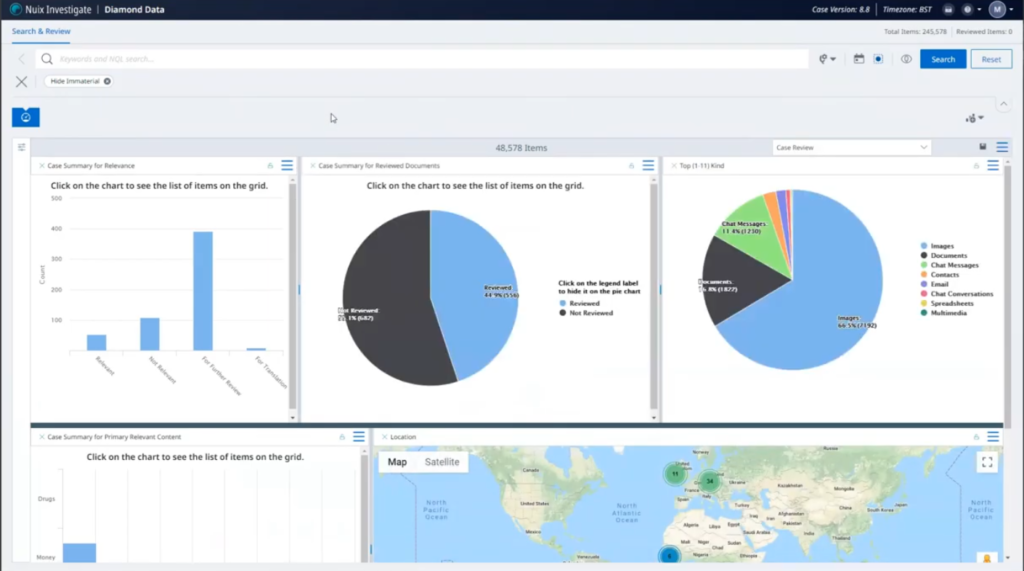
So these analytics are drilling in directly to the secured fields that have been set up for the reviewer to answer questions on. So we’ve got a chart of how many relevant versus not relevant. There’s a lot here for further review. Maybe we need to get somebody else in to look at that, to see the status of how many have been reviewed against how many have not been reviewed. I can see a makeup of the primary items within this particular case. There’s a lot of images of this case, actually. Maybe I need to get somebody in to do an image review. I can allocate all the images out as a review tool, in exactly the same way that someone was reviewing the documents.
We have items here: how many or primary relevant content has been added… money. So a lot of other… let’s see what that relates to and why they’re still relevant. And some location data here as well, if we wanted to look at where in the world things seem to be happening. And in this particular instance, we’ve got a lot of things happening potentially in Africa, in mainland Europe and in the UK.
So that’s essentially a real kind of like whistlestop tour of how a single case might be being viewed by multiple different teams. I think now we can go to questions, if there are any questions from that.

Charles: So nothing was posed for our live writing questions from the audience, but could you… do you mind talking a little bit more about those workflows and how they operate, we kind of went through that pretty quickly and some… like setting up those exceptions and stuff?
Gareth: Yeah. So a lot of it’s kind of… setting up some JSONs in the background, setting up various different tasks that can be done within automated features within Investigate. So the workflows allow you to perform bulk actions on items. So things like excluding or re-including items from the case, doing the search and tag, which we showed as well. You can also do things by… we could automate that adding things to folders action. So although I did that manually as the early case assessment, we can automate all of that as a single item for you to go into. You can also run scripts as well. So you still have the scripting features through the workflows themselves.
Charles: Very cool.
Gareth: Yeah. So they’re really flexible. They allow you to do a lot of really cool stuff within Investigate, that perhaps people just looking at the surface wouldn’t know necessarily that they exist. We’ve got a really well written documentation with lots of template guides and everything, to be able to construct them yourselves or, you know, contacting us and the support and the SET, we can help kind of build out those workflows for you, for the specific thing you need to look at.
Charles: That’s really great. Thank you, Gareth. Go on to the next slide.
So this is part of a series of webinars that we are doing here at Nuix. Got a couple up on the screen right now. If you are logged in to this webinar, you’ll probably also get an email sometime in the near future with other dates as we announce them. We have a lot more content, so stay tuned and thank you very much.
Gareth: That’s great, everyone, thanks for your time today.
Charles: All right. Thanks, Gareth. Bye.
Gareth: Thank you. Bye bye.