Binalyze DRONE is a remote digital forensics investigation solution that provides you with the capability to quickly understand your network by acquiring and analyzing data across all endpoints in minutes.
With each release version, we are adding new improvements and enhancements based on our product roadmap as well as some of your great quality feedback.
Today we are releasing v1.7.0 and here are the release highlights:
- Linux support
- Added Regex and Wildcard support on keyword search
Let’s dive into the new feature set.
Linux support
This was a popular request from a large number of our users and customers so we incorporated the feature into our roadmap right away. With this release, it is officially available.
The following distributions are supported and it will be extended to support more distributions in the upcoming releases.
- Debian 7+
- RHEL 7+
- CentOS 7+
- Fedora 21+
- Ubuntu 14.04+
- Pardus 17+
Below is a list of analyzers that are supported on Linux:
- Generic Webshell Analyzer
- Vulnerability Analyzer
- YARA Scanner
- Process Analyzer
- CronJob Analyzer
- Package Manager Analyzer
- Shell History Analyzer
Regex & Wildcard keywords search
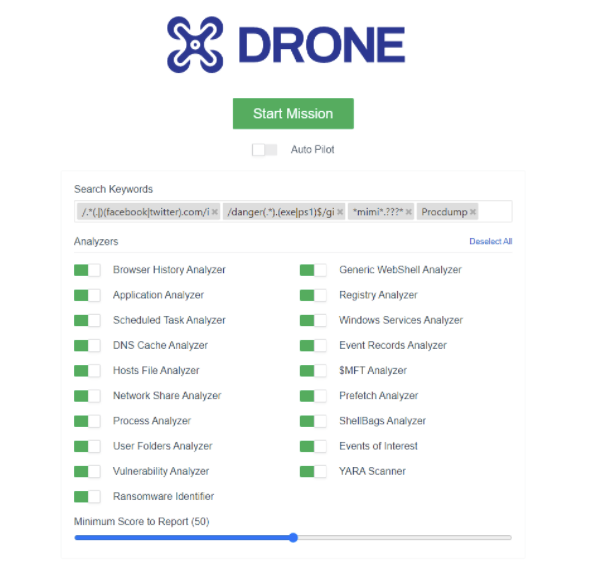
With this version, we are further enhancing your analyzing capability by adding regex and wildcard keyword searches that will help you get more detailed investigation results. Below you can find inputs and examples on how to use both of these keyword search methods in DRONE.
Regex Keyword Search
If you input a string that contains regex between forwarding slashes, Drone accepts it as a Regex pattern and searches with the regex engine.
For example, you want to search for a certain pattern on your MFT, and let’s say you want to find the “exe” or “ps1” files that contain the name of the “danger”. So if you provide a regex pattern like /danger(.*).(exe|ps1)$/gi then you may expect to find all the MFT records like below if they existed in your MFT;
- danger-v1.2.3.exe
- danger-vx.x.x.ps1
- verydanger.ps1
- Dangerrrr.exe
As you can see in the above example, regex closure must be in the forward slashes and after the last forward slash, you can also add Regex flags. Supported flags are;
- (g) Global: Don’t return after the first match
- (m) Multiline: ^ and $ match start/end of line
- (i) Insensitive: Case insensitive match
- (s) Single line: Dot matches newline
- (U) Ungreedy: Make quantifiers lazy
Syntax
The syntax of the regular expressions accepted is the same general syntax used by Perl. You can find more details here https://pkg.go.dev/regexp/syntax
More Examples
Search for unwanted host file entries;
/.*(.|)(facebook|twitter).com/i
Drone reports examples below in case if you have these entries;
- www.facebook.com
- www.twitter.com
- facebook.com
- twitter.com
Search for event log that contains mimikatz;
/mimi(katz|lib).(exe|dll)/i
Drone reports if you have an event log entry that contains the below keywords;
- mimikatz.exe
- mimilib.dll
Wildcard Keyword Search
If you put an asterisk sign or question mark in your keyword search, Drone accepts it as a wildcard search and uses the wildcard engine to search matches.
For example, you want to search for a certain pattern on your MFT, and let’s say you want to find the file name that contains “danger” and ends with a dot and 3 more characters (possibly an extension). So if you provide a wildcard pattern like *danger*.???* then you may expect to find all the MFT records like below if they existed in your MFT;
- danger-v1.2.3.exe
- danger-vx.x.x.ps1
- verydanger.ps1
- dangerrrr.exe
- Danger.png
- DaNgER.txt
Syntax
Compile creates Glob for given pattern and strings (if any present after pattern) as separators.
The pattern syntax is:
`*` matches any sequence of non-separator characters
`**` matches any sequence of characters
`?` matches any single non-separator character
`[` [ `!` ] { character-range } `]`
Character range:
c matches character c (c != `\\`, `-`, `]`)
`\` c matches character c
lo `-` hi matches character c for lo <= c <= hi
More Examples
Search for an unwanted host file entry;
*.twitter.com
Drone reports examples below in case if you have these entries;
- www.twitter.com
- mobile.twitter.com
Search for an event log that contains mimikatz;
*mimi*.???*
Drone reports if you have an event log entry that contains the below keywords;
- mimikatz.exe
- mimilib.dll
About DRONE
DRONE is among the first solutions in the digital forensics software market that is built on a foundation that empowers users with much faster speed and simplified user experience, clearing the way from heavy and time-consuming traditional digital forensics solutions.
You can use DRONE for:
- Fully remote endpoint assessment
- Ultra-fast Early Case Assessments
- Automated Compromise Assessments
- Rapid keyword searching of forensic evidence
- Anomaly Detection on endpoint forensic data
- Support for Sigma rules
- Decreasing preliminary analysis time to minutes
- Supporting analysts with less experience to make informed decisions
How to get DRONE?
If you would like to try the DRONE, please visit www.binalyze.com/drone.















