Chris Hargreaves: Without further ado, we can start the formal program and I’ll hand over to Serge Droz – I did my best there – for the first keynote of the week. Thank you.
Serge: So, this technology is working. Thank you very much for having me. Good morning here in the beautiful city of Oxford. I’m going to talk today about global incident response. You all are kind of, how shall I say, working on the foundations of this. You provide the evidence that then helps incident responders to actually react to whatever you find.
And that is something that has changed a lot in the past and also is not obvious to work at all, because as we know, the world is not just a happy community. We’re reminded thoroughly these days that this is not the case. And I’d like to talk to you a little bit about how these things work, what are the challenges and what are the changes, what has happened in the past 20-30 years when it comes to global incident response.
Maybe a little bit about me. I’m kind of in my second life. In my first life, I was a researcher in astrophysics which really seems like a totally different life. Job prospects in astrophysics are really horrible. So you made a wise choice going into computer science and forensics, a lot better job offers.
And for about 20 years, I’ve been working in incident response. Today, actually until tomorrow I work as the Head of Security at ProtonMail, an organization with a lot of interesting customers, so to speak. And again, a big part of that work is about collaborating with others to kind of find the bad guys.
I mean, the current kind of high topic thing actually ties back to Oxford where a bunch of teenagers who were suspected of being Russian nation state actors turned out to be Oxford teenagers had some of the biggest companies in the world.
Now, before I kind of go into how this works, I’d like to introduce you to a quite odd but fairly important and big incident. Who’s ever heard of the DigiNotar case? So, quite a few people. DigiNotar happened pretty much 10 years ago, 2011, and I still find it a very, very fascinating incident because it was actually kind of a game changer in the world of instance response.
2011 not only hosted DigiNotar, the big incident, it also hosted the Arab Spring, a time where the world thought, “Okay, things are going to change. Finally the authoritarian regimes are going to go away and the people will go and get their rights.” And among them here are the Iranians protesting against the government.

And governments, when something like this happens, while they do it all over the place, they like to read what the people say. They want to know this, they want to control this. So governments tend to attack crypto. They try to break crypto and it’s not something that’s confined only to authoritarian dictators, it’s something that seems to be popular and popping up all the time in the UK, but also the EU is talking about back doors. Remember I think in the nineties, we had the clipper chip who was supposed to have a back door. It’s all very difficult discussions.
But one thing that’s for sure is the governments and state are just like to listen in. And what’s one way to listen in? Well, most of the internet connections that we have today and that we had 10 years ago are really web connections. You read email on a web mail service or just Gmail, and that is kind of hard to break, but you can break it.
So how does this work? Well, every website you see the little padlock and excuse me, if you all notice, if not, I’ll just run you through briefly how SSL works. So for a website to kind of say, “I am the website I am, and let’s talk encrypted.” It provides a certificate and every website has its own certificate.
Obviously, web browsers can’t know all of these. So there’s what’s called a certificate authority that web browsers know about that attests, “Well, hey, I actually know about this certificate and I guarantee you it’s okay.”
And you see this here for Twitter, for example, where you have the DigiCert Global Root CA which is hard-coded into the browser, and then it chains down to Twitter.com. So if the browser encounters a certificate from Twitter, it can actually check, “Hey, this has really been signed by DigiCert.”
So that’s all fine in theory, except that the web browsers have some 150-200 of these Root CAs in them. And not all of them are really up on par. So one way to actually intercept this is to create a false certificate.
And how do you do this? Well, you hack one of these certificate authorities. You think that doesn’t really happen? Well, it did happen quite a lot at the time. One of the big providers, Komodo has been hacked by a guy called the Komodo hacker several times and affected were among others, email providers, such as Gmail.
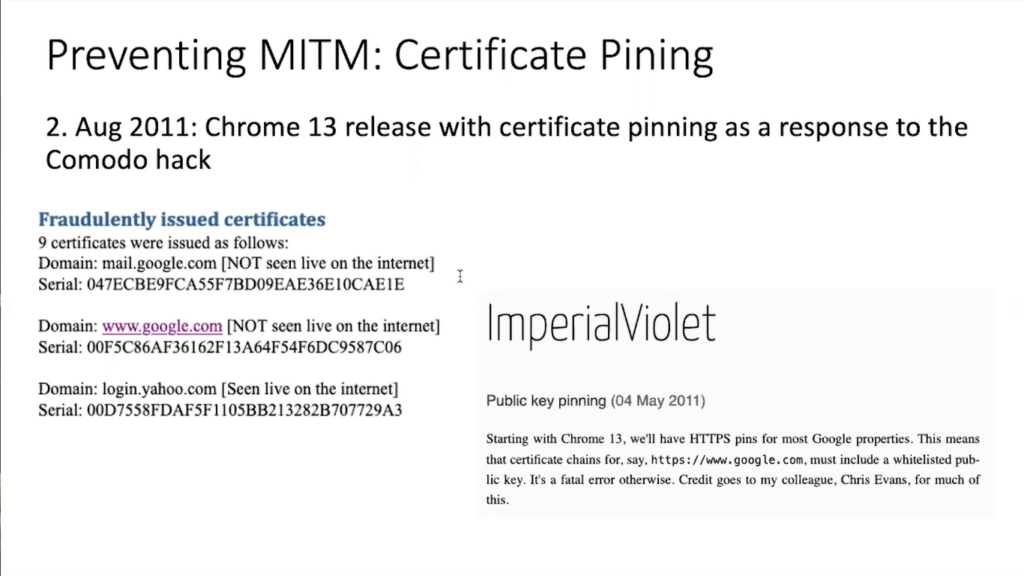
So, two guys at Google said, “This is really bad, but we have one of the most popular browsers, Chrome, and we know what certificates we have. So how about we teach Chrome to only accept certificates that we know are generally requested by Google and don’t come from some hacked certificate authority?”
That’s what’s called certificate pinning. And there are various problems with certificate pinning and we’ve given up on this and introduced other mechanisms. But at the time that seemed like a good idea.
And this was introduced on August 2nd, 2011. And I mean, just think of this: two Google users say, “Okay, let’s introduce this. Nothing can go wrong.” and they just did it.
It didn’t even take a month for this to trigger. On August 27th, an unknown user from Iran said, “Hey, is there something wrong with Gmail? My Chrome is giving popups and saying something is not good.”
Who pays attention to an internet user from Iran complaining about an obscure alert that probably 99% of the internet users don’t understand? Well, the people that paid attention to that were the German CERT-Bund: the German national incident response team. They noticed this post and started analyzing this.
And what they found out is that the certificate in question, the certificate that that user was presenting, or that was presented to that user claiming to be from Google, actually came from a Dutch certificate authority: DigiNotar.
So what the Germans did is they said, “Well, okay, DigiNotar is the Netherlands, that’s not us. We’ll just hand this over to our colleagues of GovCERT.nl” – that’s now NCSC.nl – “and then they can take care of that.” They did look into this. They got in touch with DigiNotar, and they got in touch with Google to kind of find out what’s going on here.
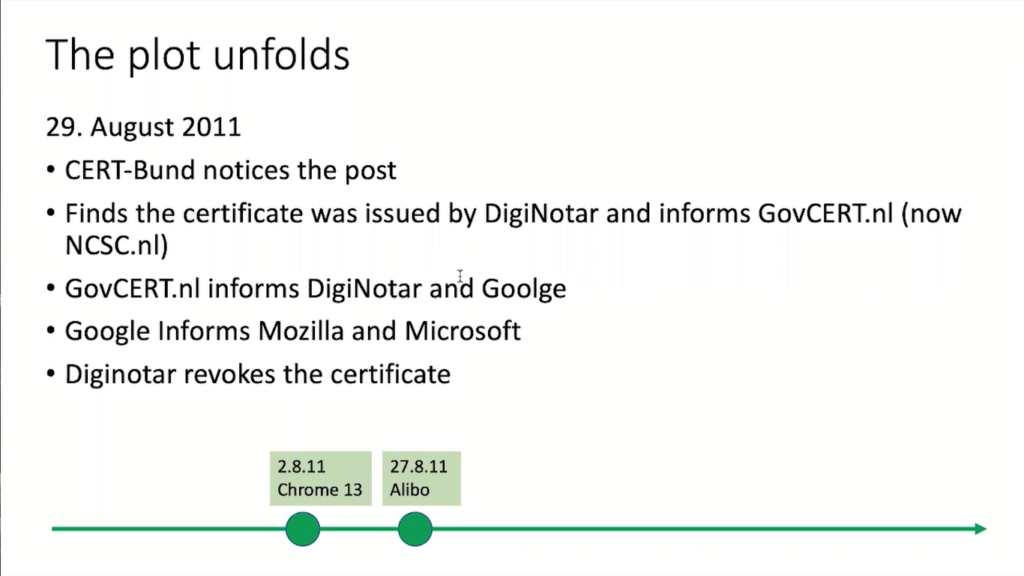
Now, a Google intern started informing Mozilla and Microsoft. What’s kind of interesting to know is that the list of certificate authorities in the browsers is actually maintained by Mozilla. So most of the other big browser producers use Mozilla’s list. So that’s why Mozilla came into the game too.
Now, Diginotar just revoked that certificate saying, “Nothing really happens.” and really downplayed the breach. So they said, “There was one incident and nothing really has happened.” but somehow that just didn’t really feel right.
So the Dutch government hired Fox-IT, which was at the time a Dutch, now it’s a British forensics company that is kind of pretty good. Is anyone from Fox here?
[audience member]: I used to be.
Serge: Used to be. It was really amazing, Fox, and they did a really cool report. Maybe you know more about this incident than I do, that may well be.
[audience member]: I participated in the evidence collection.
Serge: Okay. Maybe you should come here.
[audience member]: Just a collection of the evidence. Really interesting.
Serge: In any case, what Fox found out is that in fact, the web service had been hacked kind of two months before that incident. And because the firewall at the DigiNotar wasn’t really as tight as it should have been, access to the backend databases was possible. And that’s what was used.
So that actually had been discovered, but DigiNotar just revoked the certificates and didn’t really do anything else, which seems to be a fairly typical behavior, which is kind of bad, but on the positive side means job security for us. And that was enough to run a full analysis. And it really became one of the biggest analyses.
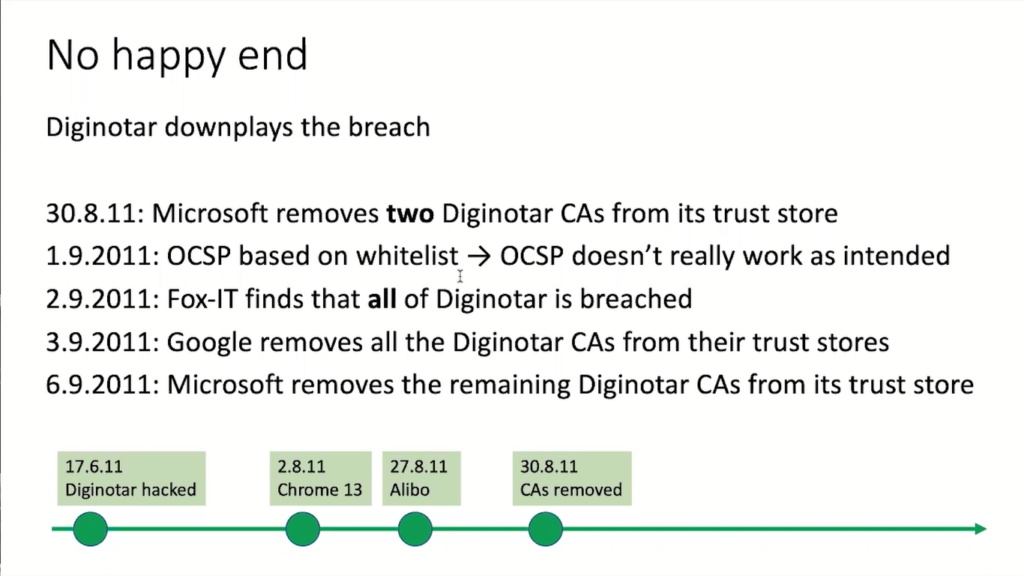
So DigiNotar was actually running more than just one certificate authority, they had I think six certificate authorities for different types of customers, and as things unfolded, Microsoft started to remove two of the commercial CAs, and that’s kind of a really big thing.
Also, it was decided to use this online certificate status protocol, OCSP to kind of only allow certain whitelisted certificates to go through, but that somehow doesn’t work because OCSP, it’s a nice idea, but it doesn’t really work out.
Now, at Fox, the kind of main finding of Fox-IT was really that all of DigiNotar was kind of breached. And why is this a big issue? Because DigiNotar was running the certificate authority for the Dutch government. So every single server in the Dutch government that used the certificate, and that’s not only for websites, that’s also for machine-to-machine communication potentially could have been compromised.
This is a big issue. And they really created a kind of, I’d say a crisis in the Netherlands. My colleagues at GovCERT.nl still seem to be a little bit traumatized about this.
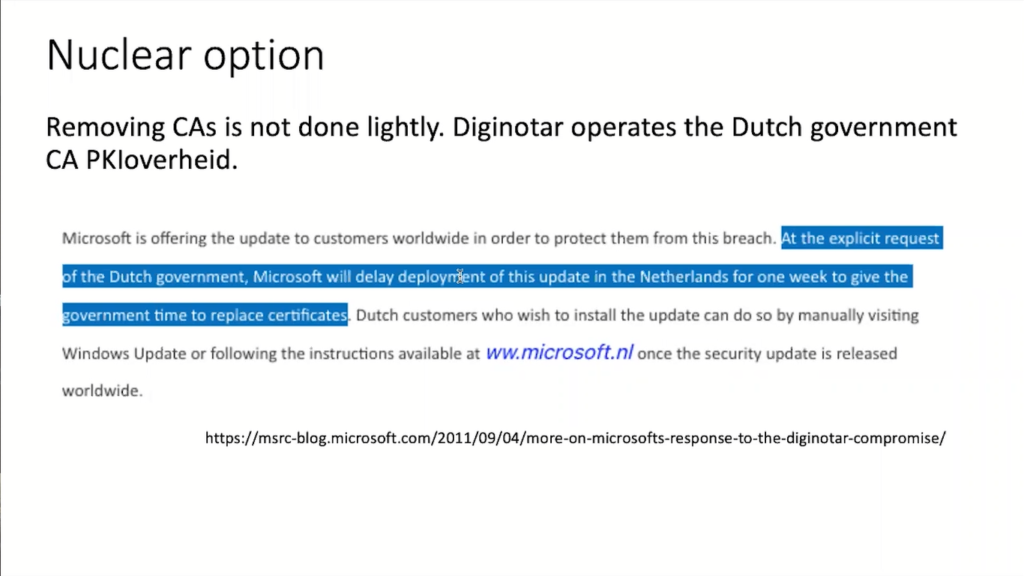
And then, in early September, Microsoft really started to remove all the remaining DigiNotar certificate authorities from the browser. I mean, just think of this. This is kind of a nuclear option. If you remove this from the browser, you cannot serve on any of these websites anymore. You cannot buy a train ticket, you cannot fill in your tax return, because every time you do it, there’s a pop up saying, “You’re accessing an unsafe site.” So this really is a big thing.
And then something happened that has never happened before. Microsoft published, you can still find this online, said, “At the explicit request of the Dutch government, Microsoft will delay deployment of this update in the Netherlands for one week to give the government time to replace the certificates.”
So for the first time a government has actually approached a private company saying, “Hey, we need more time. Please delay the security update.”
That really was amazing. And a good friend of mine worked at Microsoft at the time and told me about the discussions they had. They were really kind of perplexed because Microsoft is a US company. They feel strongly about security and now another government approaches them. What should they be doing? These were kind of the discussions to be had.
And it turns out it’s not as easy to do these types of things. How does Microsoft decide you in an Netherlands are not valid? Looks at your IP addresses. because plus minus, that’s mostly what it has and looks, where is the ISP located? Is it located in the Netherlands or somewhere else? There is a Caribbean island that has a French part and a Dutch part, but only one ISP.
So that proved to be kind of a challenge. And I still don’t know what they actually decided to do. Maybe they just delayed it for two days there, whatnot.
But just to kind of tie today, today, we have all this talk about, well, we should, we should block Russia and all these calls for censorship and blocking IP spaces. It’s not as easy as it sounds, and it wasn’t easy 10 years ago and it certainly hasn’t become easier today.
What about the victims? So what OCSP actually does allow you, is to see where certain certificates are used. And that was done. You find all these statistics from in Fox-IT’s report.
And what was found is that nearly 800,000 of these certificates had been used and mostly from Iran, which gives you kind of a hint of what this was about. Well, if you want to tell your CEO that security actually is important, a month later, DigiNotar was bankrupt, didn’t survive that security or at least violation of trust.
Now, the question of course is who was it? And until today, no one really knows this. So on Pastebin you can find these paste by a guy called the Comodo Hacker who claims “I’ve been this,” but no one really knows who this is.
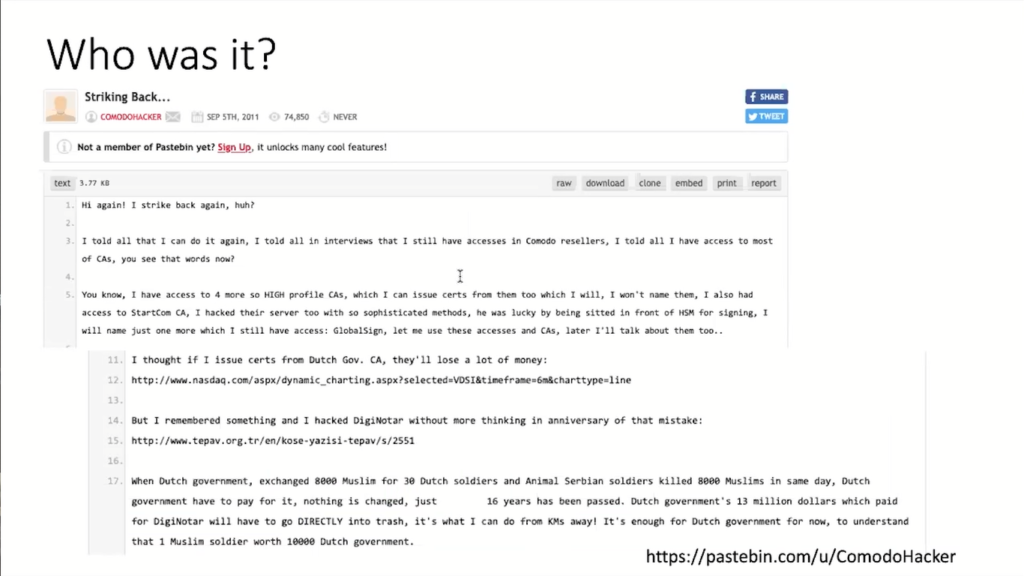
Looking at the victims, it seems to me that it probably was an Iranian state actor who wanted to read the email of his or her citizens. And kind of an interesting side remark, I told that exact story at the UN meeting, and caused a diplomatic incident. The Iranians were very upset about this because they feel the West always accuses them. Why am I saying this? Because all of this has a political dimension.
Now, what were the consequences of this breach? Well, obviously the rules for CAs have been tightened. Today, I think CAs still occasionally get hacked, but the security requirements are much stronger. We’ve been working towards things like certificate transparency, which kind of replaces certificate pinning.
And obviously for my Dutch colleagues, it’s been an enormous boost. I mean, finally the government realized that the security faults are not just some kind of strange nerds that sit behind computers in the basement all day, but that they actually do important work.
But what I’m really interested in is how did the information flow in this incident? There are a lot of interesting technical things and we could go into the forensics, and you know all of this much better than I do, but how did the information flow? And I think that’s interesting to look at.
So it all started with this Iranian user kind of posting something to the bulletin board, which was then kind of more probably by accident noticed by the German Cert, CERT-Bund who then informs GovCERT.nl.
GovCERT.nl had a really busy week. It needed to talk to Google, it needed to talk to DigiNotar, Fox-IT which is a private company. It also had to liaise with the Dutch government because all the politicians had no clue what this meant. So something had to be done, they needed to be coached, they needed to explain to them what this means.
They also were talking to industry; Microsoft, Google, Mozilla, and to the general population, to the people in the Netherlands to whom they had to explain, “Hey, look, if you get a popup like this, that’s what it means, and it doesn’t mean the government is hacked.” and so on.
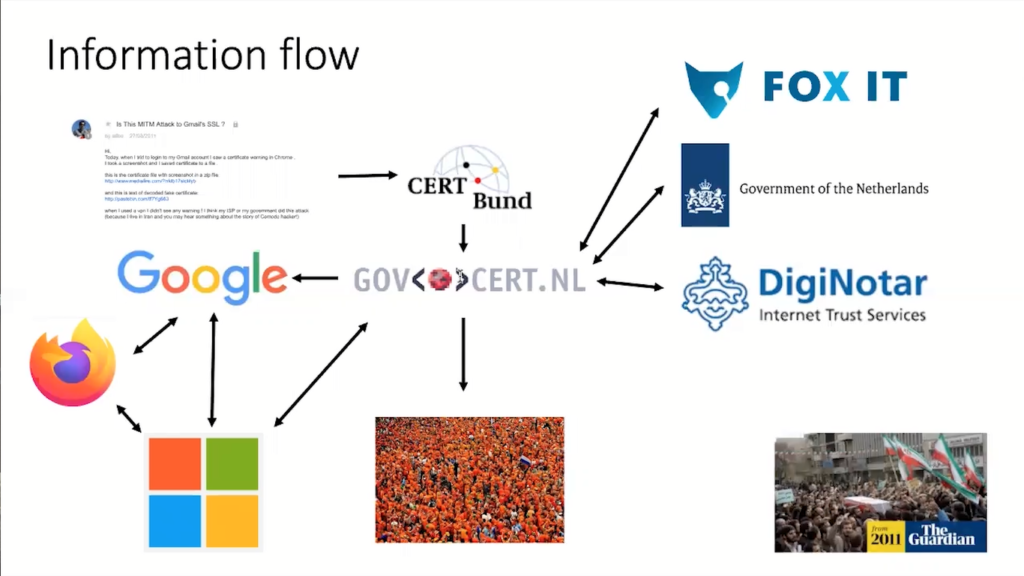
So there’s a lot of information flowing around. And again, the tax sector, Google, Microsoft, and Mozilla, they were having phone conferences to align their actions. It was Google that had actually informed Microsoft.
The only people left out were Iranians. They were victims of that attack because, why? Because we are not allowed to talk to these people. Iran is under comprehensive sanctions and most Western security teams would run into legal problems if they were to talk to these people.
And that caused a second diplomatic incident because it’s US sanctions. And in the very same talk, the Americans were upset too, because they blamed their sanctions.
Now, what are the learnings from all of this? I think for me, always amazing in these 20 years, someone has an idea like these two Google guys who say, “We are going to pin certificates.” Sounds kind of like a small thing. And it helped us uncover one of the largest incidents that ever happened in the Netherlands.
And this is something in my career that I’ve always kind of experienced is, some people get together, they have an idea, they start working on it, and it certainly seems to create an opportunity to create a lot of value.
That’s why I feel in-person conferences are so important. The interesting part doesn’t happen right now in here. The interesting part is going to happen tonight over dinner and a beer. I often call this the beer-to-beer network. That’s when we start talking and we start developing ideas that then may evolve into something really cool.
What’s also important here is that incidents are never really only a technical issue. The technical part there was really easy. It was outdated software on a web server and a badly configured firewall, that’s it. But what it meant is that an entire country came down, the trust in a lot of infrastructure was shattered, and so there were all these non-technical aspects that we technical people tend to forget. sometimes.

Obviously there were a lot of stakeholders. This is not something that just Fox-IT could have solved, or the Dutch government could have solved. There were a lot of people that needed to play to each other and notably people that didn’t really have a prior or strong relationship. So incident response, I guess at the end of the day is really complex. And that’s what I’d really like to look into in the remainder of the talk.
How do we actually, on a global scale, co-operate? Work together? There are different models of governance, but let’s look at what governance actually means.
To the left you see a picture of how the internet looked at the beginning of the sixties. It had four nodes and I’m pretty sure each of the administrators had each other’s landline phone number. If an incident happened, it would’ve been fairly easy to do something about this.
But you see, today is a massive network with thousands of connected networks. The internet is the network of networks, and you don’t have everyone’s mobile phone number or fixed net landline phone number to talk to.
And managing this and making sure this actually remains kind of stable and it remains reasonably secure is not a trivial task and sometimes actually quite surprisingly that it still works.
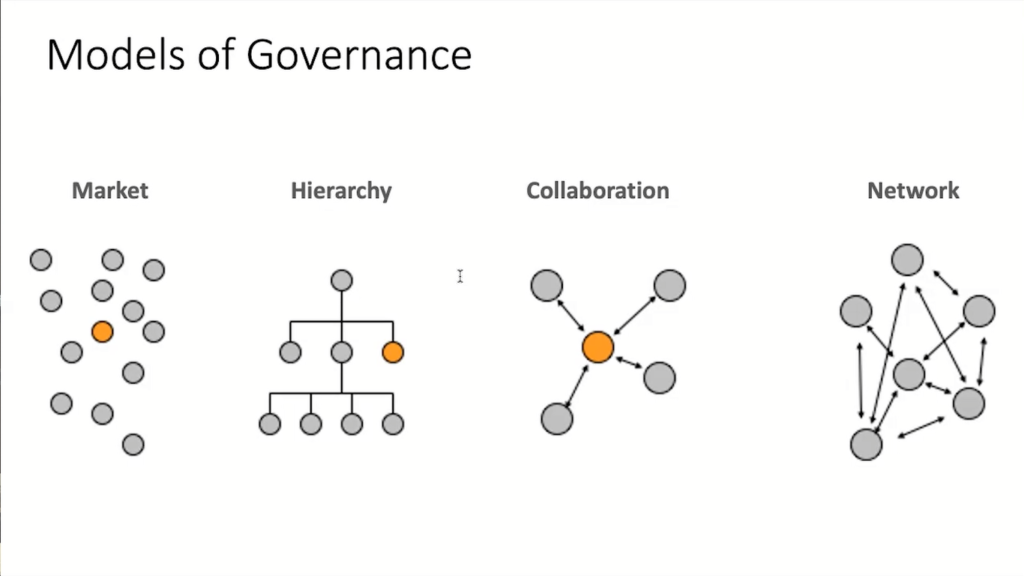
Now, what are different models of how you can manage such complex systems? Well, kind of the most popular one is the market system. That’s where our global economy is built up from. You pay someone to do a job for you.
On the internet, at least in security, that’s certainly not going to work. I don’t think that the Dutch government could have paid Microsoft something to delay a security update. That’s just not how things work. And as soon as you move away from kind of like-minded states, it becomes even harder.
Then a lot of people advocate a hierarchical model. That’s something that a lot of states, for example, would like to have and promote this in ITU, the International Telecommunication Union.
About at the same time, there was an ITU kind of congress about internet governance. And a lot of the states, mostly led by Russia and China, were really vouching for a hierarchical model, the internet to be regulated by the United Nations or the ITU, but come on, that’s not going to work out and it would be a really boring internet. And West really pushed against this. So this never happened.
Then there’s this thing about collaboration, but collaboration is good, but it just doesn’t scale.
And lastly, there is this thing called network governance that no one really understands. And this is a network, not in terms of fibers, but really in terms of human relationships. And I’d like to read you the definition. “Network governance is achieved through relatively stable cooperative relationships between three or more legally autonomous organizations based on horizontal, rather than hierarchical coordination, recognizing one or more network or collective goals.”
So what does that mean? It means that a couple of organizations start getting together and start to work together over extended periods of time. On eye level, they don’t typically have contracts, they don’t have NDAs or MOUs or whatnot. They just work together because they share the same goal.
Now, this may all sound kind of like a really strange flower power hippie kumbaya singing, certainly never going to work, but it does work. Elinor Ostrom in 2009 received the economy Nobel prize, because she could actually demonstrate that this network governance is really effective when it comes to very, very difficult and challenging problems with a lot of stakeholders.
Elinor Ostrom did not investigate cyber, the work that led to her Nobel prize was about sustainable water supplies in very dry regions where she found that communities that use the network ordinance model had the best water quality at the best price. So this does work, but what does it really mean?
Now, if you go back, that really is a network. CERT-Bund and GovCert.nl don’t have any formal contracts or anything, they just know each other. They probably know each other because they’ve been out drinking beers together and they have a working relationship.
And the same goes for all the security folks at Google, Microsoft and so on. So these are typical kind of properties of these kind of global networks.
And even today, all of these stakeholders do work together in very informal ways. There’s different types of trust groups where they’re in and so on. You can’t really document this because it’s something that’s very fluid. It keeps on changing, people drop out or people come in, but it is something that people have to learn.
Now I mentioned the word trust group, and it turns out that trust is one of the most important things that you need to have in a network governing model. If you’re not trusting the other side, you have a problem. If Microsoft were not to trust the Dutch government and said, “Hey, we need to have all the paperwork. Let’s get the lawyers together.” They will wait for weeks for this to be done.
Remember in network governance, you work on eye level, you don’t have legal bindings. And that means trust. You are going to talk about things that are unpleasant, you talk about mistakes you’ve made, if you’re approached by someone who says, “Hey, I think you were hacked,” that’s not something you want to see in the headlines. You need to trust these people to work together. So trust is actually one of the most important ingredients we have here.

Trust is not something that you can buy. Trust is not something that you just say, “Okay, we’re going to trust each other.” It’s something that you have to build up. And there’s a couple of dos and a couple of don’ts.
So I think a very important part is to understand roles and responsibilities. In the introduction, we heard about law enforcement working with this community. Now, law enforcement often has very, very different objectives and it certainly has different rules from what we do as incident responders. We want to kind of stop incidents whereas law enforcement wants to arrest people and that’s not always the same thing.
And we have to trust each other that we don’t kind of spoil that relationship. But it’s important to understand that the police do something else. The police have different standards from an incidence responder. Telling someone to shut down a web server is not the same thing as arresting someone for hacking a web server. These are different roles and responsibilities.
It does help to have strong contacts. It’s really important that you know these people before a crisis happens. And that’s why, again, it’s important that you talk to each other, that you build up these networks.
And typically you build up these networks and working networks by having a shared history of collaboration. You start working on something simple, maybe I don’t know, a phishing site, whatnot. And then as time evolves, trust grows, then you can start working on more and more complex and challenging issues.
Another thing that’s often kind of underestimated is the use of the same terminology. When I talk to people, say in Africa and ask them, “What are your biggest challenges? They usually say, “Oh, well, it’s when we ask a Western company or one of the big tech companies, we never get an answer. And that really is very, very difficult for us.”
When I ask the people from the big tech companies, “So why do you never answer these things? These questions coming in from those teams?” they say, “These questions never make sense.” And that’s not because they don’t make sense. That’s because these people use different terminology. They use the term phishing for something else.
And this may seem silly, but I’ve seen so many incidents where there was just really a misunderstanding of what the issue was. So building up terminology, building up standards so that you know what you talk about avoids misunderstandings. The world is a big and complex place and therefore we have to make sure we understand each other. That seems to be hard enough among friends sometimes, imagine how hard it is among people you barely know.
There are also a couple of don’ts. Don’t have hidden agendas. That’s never going to work out well.
Don’t expect too much. If you approach another organization and say, “Hey, can you help us?” don’t demand this. Kind of the intellectual property crowd, they always show up very demanding. “We found that one of you users downloaded the music file. We demand that you do X and Y and Z.” I mean, most people can say, “Well, you know what? Go away.” That’s not how it works, that’s not how you build trust.
Don’t be in the wrong department. The United Kingdom placed its national CSERT with its intelligence services. And that wasn’t a very smart move because that very same intelligence service has hacked Belgacom kind of just a couple of weeks before. And most people go, “Oh, why should we talk to you?” So be very, very careful of where you put your incident responders.
And then obviously make sure you have good policies. And that’s something that’s really very dear to my heart, because first the form of incident response and security teams, which brings together all those teams have been numerous times burned by bad policy.
Right now we again have sanctions against Russia. And I’m not going to argue if the sanctions are good or bad, but the result of these sanctions was that we had to suspend all our Russian colleagues. Now that just doesn’t make sense. It’s like, you don’t sanction medical supplies, so we also should not sanction incident responders.
It’s important that you have people all over the world you can work with. Obviously the trust to the Russian colleagues is maybe not as high as the trust to, I don’t know, the German or British colleagues, but we do work together.
I mentioned first, the form of incident response and security teams. You really bring together people from around the world. And that includes teams from places like China. Why? Because also the Chinese and the Russians are victims to cyber crime. They’re not per se in favor of crime, even though Russia, sometimes one has its doubts.
But the idea is that we can kind of work together in a global internet and that’s what we need. We foster a lot of collaborations, we foster a lot of special interest groups, we have about 16 special interest groups about various topics from CVSS, the standard that most of you probably know is something that comes out of these two others like metrics or where we try to talk about how can we measure the effectiveness of incident response and detections. Those are things FIRST does.
And last but not least, and something I’ve been very, very active in is how policy makers understand the internet.
Now, that is how it’s worked for the past 30 years. FIRST has been around for 30 years. It started as a handful of teams, it’s now grown to over 600 teams and we kind of think, “Okay, here we are. We kind of know how this works, we know how the internet works.”
Yet we’ve heard it in the introduction that over 50% of the crimes have a kind of digital side to them. I’m not sure what I would call this cyber crime, I would maybe call this digital crime. I mean, fraud is fraud. Doesn’t really matter if it’s through an email or a paper letter. I remember times where we got kind of handwritten letters about somebody wanting to have money with some heartbreaking story, not unlike the emails you get sometimes today. So that’s not really cyber crime.
But where are we going? Well, the big headlines really are cyber war. I haven’t seen the cyber war, but this thing is making the headlines.

And these headlines are forming the minds of people. They’re forming the minds of politicians who then come out with rules and regulations and that was one of the consequences.
For example, Russia now complains about ongoing cyber attacks on its infrastructure. Now, you can say, “Okay, this is just Russia saying what Russia says,” but think a little bit about it. What Russia here really says is, “You are attacking our critical infrastructure, and under international law, if you attack critical infrastructure, you are very close if not above this line of unarmed attack.”
And what international laws allows you is to defend yourself against any time of what’s an armed attack in any way feasible. That means kinetic. So, and Russia has hinted this a couple of times during this conflict. At the beginning of the conflict, there was an attack on the Russian Space Agency and they said quite clear, they treat this as an armed attack.
What that mainly means is they can legitimately shoot back a missile to you. And so this has implications and we should keep these things in mind.
Now, what are governments actually doing on the internet? So cyber war, war is something that governments wage, civilians can’t wage a war. It’s international law that defines what an armed conflict is and so on.
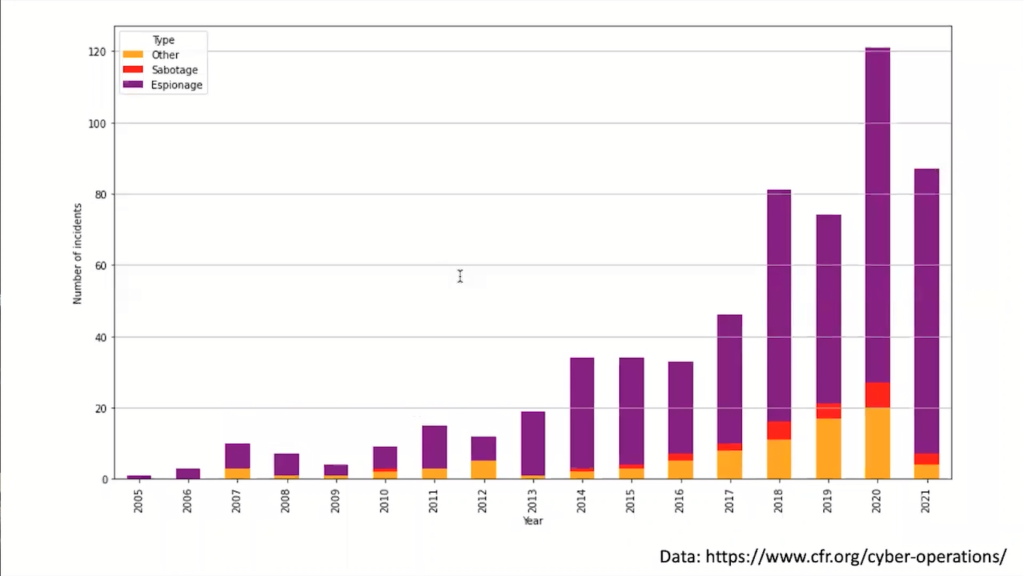
But if you look at what actually governments are doing on the internet, it’s mostly espionage. So there’s a little bit of sabotage if you look at the last couple of years, but it’s mostly espionage. Why is it espionage? Because espionage is actually totally legal. No law that says spying on someone else is not okay.
And if you ask states, “Hey, don’t you think we should kind of put a stop to this?” They always say no. There’s no way states would ever agree on abandoning espionage.
And it’s kind of understandable because as a state, you actually want to know what the other side is thinking, because that puts you into an advantage that allows you to plan, it allows you to kind of, if you know, what the others do, you can act accordingly. That’s much better than being surprised.
And that’s one of the reasons why very few people actually are against espionage. Now, kind of before we had the internet, that was kind of, okay, it was kind of the spies and we have all the cool spy stories. The real life is probably not as exciting as in the spy stories, but that’s plus minus how it worked.
How does it look today? Look at the Exchange vulnerabilities that we discovered last year. There’s the Hafnium group attributed by Microsoft. This was a series of vulnerabilities in the Microsoft Exchange service that were used to compromise mostly government organizations. And it just came briefly after the Solarwinds thing, which again was mostly government agencies spying on each other.
I mean, I would prefer this not to happen, but it does happen and it’s always happened. The problem though, is this Exchange stuff is, once it was known, the opportunity was seized by criminals, and mostly ransomwares operators jumped on these vulnerabilities and abused this at a tremendous stage. It’s kind of just that they started using this opportunity.
So what you could argue is that this was a state-sponsored espionage operation, which is not per se illegal, but it created huge collateral damage. It allowed criminals to break into hundreds and thousands of networks to actually paralyze hospitals during a global pandemic. It caused this huge collateral damage, and that violates the principle of proportionality.
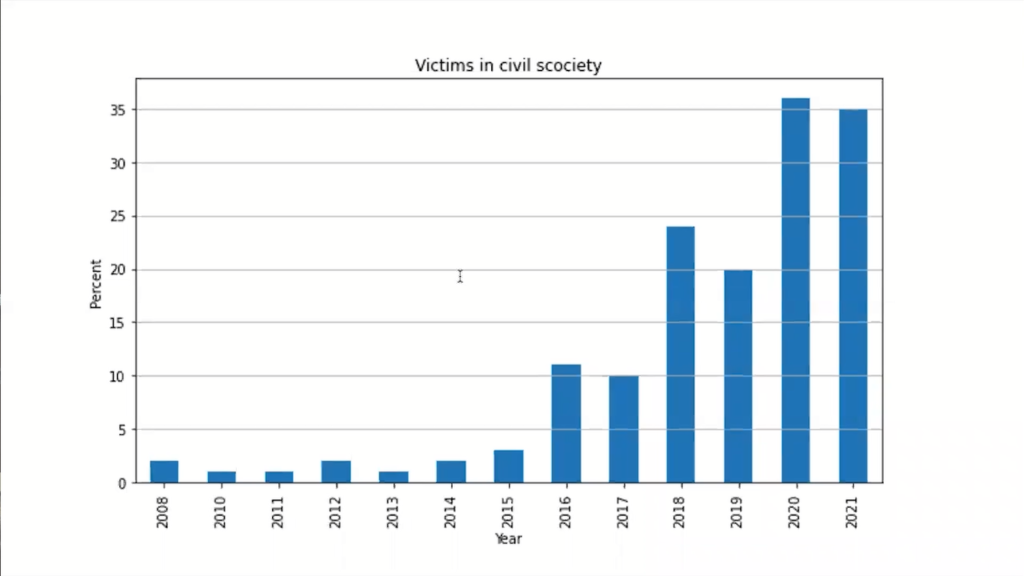
So it probably is not legal under international law. And this is really what the concerning trend is. If you look at the victims of state-sponsored operations, until 2015, there’s always been a little bit of collateral damage. If the spies start shooting at each other, they’re bound to hit the civilian.
But after 2015, we see a massive increase. Today’s 35% of the victims of state-sponsored operations are civilians. This may be in the form of victims of ransomware if the attack is taken over by criminals, but it may just be civilians that are actually attacked. Think of the Pegasus software, which is a huge problem where states attack civilians. And that is really quite a concern.
So what is the international community? Because this is now really international law. State operations are governed by international law, at least since 2013. Between 2004 and 2013, a United Nations governmental group of experts, which is a group of handpicked states who sat together, debated about: does international law hold in cyberspace?
And it does. So it took them quite a while to figure this out, but they all agreed that international law holds in cyberspace. So whatever a state does you in principle have to follow international law, but what does that mean? What’s a kinetic attack or the use of force on the internet? Is ransomware use of force?
Most international lawyers would argue it’s not because you don’t really damage any hardware. You destroy information, but information is not tangible, so it doesn’t fall under, you can’t violate it. Is turning someone else’s power grid off use of force? Well, it’s not, because you turn can turn it back on. It’s only when things break conventionally that the use of force is really illegal. So no one really understands what this means.
In 2017, actually it was 2015, the states in this United Nations group of government experts put out 11 norms. Think of norms as kind of recommendations of things you should stick to, but that aren’t exactly law. If you drive your car on a highway, it’s probably not illegal to go below the speed limit, but no one really does it. And if you try to do it, you really get into trouble. That’s what the norm is.
And a couple of these norms are at a very, very high level, but a couple of these norms are very, very important to us. And that’s kind of amazing that the United Nations comes out with a recommendation that really directly applied to our daily lives.

So one of the norms says, “You have to consider all information.” Now that sounds good, but what does it mean? Well, it essentially means, or so people say is that in an incident, you have to do a proper forensic analysis to understand what the incident was. You can’t just go for the newspaper headlines.
That’s up to you. You have to deliver this forensic analysis. So depending on what incident you are involved in, it may end up in front of an international criminal court.
Another thing is that you’re supposed to report vulnerabilities you find. And again, kind of that makes sense, but does it really happen? The UK has a vulnerability equities process where it describes in detail how it decides when to report vulnerabilities to the vendor affected and when it decides to keep them for themselves.
A recent example: Log4j. It actually was discovered by Alibaba, a Chinese company. Alibaba found this vulnerability realized its impact and informed the Apache team of this vulnerability. Alibaba is now in trouble with the Chinese garment, who says, “You should have informed us first before you gave this away.” And they faced really serious trouble. You do not want to be in China and be in trouble with the Chinese garment.
Another recommendation really was that states are encouraged not to attack each other’s incident response teams. So the UN already hints at incident response teams kind of having a special privilege position during a conflict. In the last year, 2011, the same group again reiterated that incident responders should be kept out of politics.
And this is really important because right now, what we see is they’re dragged into a conflict that makes it very, very hard to work together. And it may seem kind of like, “Okay, the Russians are really having this horrible war started. We should not talk to them.” but not talking on certain basic principles makes life harder because Russia is still connected to the internet and we need to talk to these people.
And just keep in mind, one of the companies affected by these recent sanctions is Kaspersky, which is a Russian AV company. So you can argue, “Okay, well, there’s enough other AV companies.” but let’s face it, Kaspersky is the only serious AV company that ever looks at US-state-sponsored actions, US APTs, none of the others really do this. So we are going to miss something here.

But what do these norms mean for us? That’s kind of a matter of debate. Talked to you about the sanctions. So I’m not going to spend more time on this. This is a bit of a problem. But the point is that these things that are discussed at the UN will have a direct impact on the work you and I do every day.
I mentioned the sanctions and export controls, and I want to just clarify what this really means. The problem with sanctions is that they’re often vague. They have good intentions.
So the current US and EU sanctions are really about crippling Russia’s kind of private sector. Essentially take Russia’s money away so they can’t finance their war anymore. But it prohibits certain transactions and the exchange of technology.
But what is the exchange of technology? If we talk to a very expensive lawyer, he says, “Everything is technology. Malware is technology.” Well, does exported malware contribute to the Russian economy?
I have my questions. It’s dual-use technology. If you read all the agreements, every piece of malware is actually dual-use. If you read the agreements and take them literally, you’ll need to have an expert license if you want to exchange a piece of malware as a friend outside the country.
So this is a bit of a problem. And even the United Nations realized, “Well, maybe we need to talk to the private sector. We need to talk to the experts who actually understand what this means.” And what they use is what’s called a multistakeholder approach. It’s a big word, but essentially means we try to talk to all the affected parties.

And that’s something new. The UN doesn’t really usually do this. The UN has two ways of functioning. It either has the states that bring in experts and then negotiate, that’s what’s happening in this UNGGE; or they have research institutes like UNIDIR, who aren’t concerned about the weaponization of technology that then makes recommendations.
FIRST was actually allowed and given a space at these negotiations, and a lot of the wording about CSERTs and the roles about incident responders really came from us kind of making the point here, here is how we work and that’s why it’s really important.
Now, again, if we take a step back and ask the question, “What does all of this mean for us?” We started out with a very, very technical incident. It’s kind of certificate pinning. It’s something technical. Most people using the internet don’t understand this. And we ended up with the United Nations.
This is really a lot to grasp, and sometimes it’s not really clear how we should act, because as soon as we get away from technology, we need to answer questions. Is it okay to share this information today with the Russian team, or is it not okay? Is it okay to disseminate this information? You found a horrible breach, is it okay to make this public? Is it not okay? You found a vulnerability and the vendor doesn’t respond. What are you going to do? It’s not always an easy question.
So what FIRST has done is kind of worked out a code of ethics. We call it EthicsFIRST, and we kind of tried to base this on human rights. Human rights are kind of non-negotiable rights, which give you the right to privacy, the right to safety, very abstract, very basic, But you can summarize this as, “Be a nice person.”

And we try to figure out what does this mean for the technical community? So EthicsFIRST formulates a set of what we call duties; the duty to be trustworthy, that duty to to respond. I mean, how often have you reached out to someone and have never gotten a response? And we acknowledge dilemmas.
So if you have some spare time, go to ethicsfirst.org and read through this. It’s really only one or two pages. And the aim really here is to kind of help technical people to make the right decisions when it comes to something where it’s not really clear what the right thing to do is
When I started 20 years ago in cybersecurity, I thought, “This is really cool.” It was super technical. We analyzed PCAPs, we had all these cool incidents and the longer I’ve been working in this, I find the more complex this becomes, because the world has become more and more connected and decisions that we make as technologists often will have an effect later on. That’s kind of very difficult to anticipate.
Do I have a recipe to solve this? Sadly, I don’t. I think what we can do is to stay in conversation, talk to each other and make sure that the other sides understand this. And if I look at this room, there are a lot of people here that do forensics, and there are a lot of people here from law enforcement.
And law enforcement really has a hard time today. And when I look at how covering the internet, people react today to all the challenges we have, there’s really two camps. There’s the one camp that says “Privacy over everything. We are not going to give in one inch, no one recognizes the challenges of law enforcement.” On one hand. And on the other hand, the fraction that says, “We’re going to break all encryption.” That’s not going to produce good solutions.
I work for ProtonMail. Privacy is very big at ProtonMail, yet there’s a clear understanding that privacy should not be a pass for becoming a criminal. And we have to walk this very thin line of where do we give up on privacy? Where do we give in the data?
We have to find solutions. Can we do investigations without violating privacy? These are all big questions that I don’t really have an answer to that we have to find an answer. I think the internet is becoming a lot more important than it already is. So a lot of food for thought. Thank you very much.

Frank: Test. Working. Thank you very much for this very interesting keynote. We have some more minutes for questions. Are there any questions from the audience? Online participants, if you have a question, feel free to type it in the chat, it will somehow reach me. Are there questions? Yeah. Right, I’ve gotta pass it on to you. I was supposed to repeat the question, but since you’re sitting so close.
Hans: Thank you, Frank. Thank you Serge for the great presentation, great keynote for the conference. And I actually don’t have a question, I just want to say that I recognise what you explained about Black Tulip. It was an exciting investigation to be part of with the forensics part of Fox-IT.
And I do underline your comment that it was a big shock to the Netherlands, to the government. I think that’s also when NCSE started after that. The Dutch government realized how relevant the certificate authorities are, and it was not just websites, I think it was the public prosecutors that were signing off legal bills that all came to a stop. So I just wanted to underline that.
Serge: Thank you.
Frank: Thank you, Hans. Probably one question from my side. So what can we do to support FIRST or how can we get like, even more engaged to support like this global perspective and to influence like the communication flow and and so on? So maybe like easy steps, if I’m sure that some people right now think, “Hey, this sounds like interesting work. massive influence on global decision makers. How can we contribute?”
Serge: Well, I think the easiest way and the best way is just to participate in these communities. FIRST has a lot of events, a lot of conferences. The next one that we are going to have is a very technical conference in Amsterdam. It’s a technical colloquium, maybe consider attending there. Attend our first annual conference, which this year is going to be in Dublin.
But talk to people. I think it’s very important that if you work in companies that have incident response teams with whom you work, stay in touch with them. If you are interested in this thing, there’s a lot of material you can learn about this, but not everybody has to become a policy maker.
But it’s important that you start understanding what are the challenges of others. We often say we are engineers and we understand each other, but much more often, I feel kind of like, really we don’t want to understand all the others. We just know we do it right, and the others are wrong. And if we can overcome this, at least in the engineering communities, much is gained.
Frank: And then a very specific question. You might interrupt me if you have a question, but on this one slide, you said that in starting, I think it was 2015, the numbers of the civilian impact went up significantly. Any idea why it went up so significantly? Why is there more impact on civilians?
Serge: That’s really an interesting question. I don’t really have a solid answer. I think there are two aspects to this. Before 2015, a lot of the espionage operations were really kind of the classical hacking thing. You try to guess someone’s password, you get into the network, or you find a vulnerability, get into the other state’s network, steal the information and take it out.
After 2015, we found a lot more of these Exchange type or Solarwinds type things that then had collateral damage. And the governments really got a taste of starting to spy on civil society. I think the first big incident, it was discovered that governments spying on civil society was 2009 was GhostNet.
When Citizen Lab — if you are really into, by the way, really into the last thing, read the papers of Citizen Lab if you want to understand the political implications of forensic work — what they found is that China had attacked the Dalai Lama and all of the people around him in his exiled government. And that was the first time he really saw a direct attack on civil society. It hasn’t gotten any better, but that’s where we are.
Frank: There’s one question.
Moderator: Yeah. We have a question from the online chat from Frederick Muellers. He’s asking specifically about cyber crime. He says, “How important do you think international agreements like the Budapest Convention and the hopefully soon to be UN Cybercrime Convention. And do you think that these can really make a practical difference for the fight against cybercrime?”
Serge: That’s a very good question. And so in fact it is today we only have one kind of international body of law, the Budapest Convention that allows law enforcement organizations to work together. The UN is having this talk committee who is running right now to come up with a global cybercrime convention.
I have my doubts that this is going to come to a good conclusion because there’s just so much diversity, but yes, I feel this is very important and very needed. A lot of people always complain about tech companies not kind of helping an investigation. This may well be, and I think the tech sector could do a little bit better, but I also see it’s tremendously difficult to get law enforcement going on certain cases.
When I approach law enforcement, usually I hear, “Oh, but this doesn’t have any relationship to Switzerland. So we can’t really do anything.” Well, that’s the point of cybercrime: you can do it from somewhere else.
And that is something where we really need to work, have to get a better understanding and also maybe start trusting each other a tad more working cross-border. And this really is my plea to private industry. I mean, everybody talks about information sharing, but we don’t really share enough information to make a difference. And we find it very, very hard to then take that little information and make it tangible for law enforcement. So yes, a lot is still needed there.
Frank: Any more questions? No? Then I think we are, there is one more. Yeah.
Moderator: This is actually a question from myself rather than from the chat, but I thought it was really interesting how you talked a bit about specifically, how do we help policymakers to understand the internet? You talked a bit about fostering collaboration through special interest groups and so on, and the tension between law enforcement and individual privacy.
And I was just wondering if you could talk a little bit to how individuals like myself who are just sort of starting out as researchers, as new PhD students, how we can really help make an impact on policy makers and their understanding of how the internet works and what legislation would be good for the global community?
Serge: That’s a very good question. At the end of the day, I think it boils down to sitting together with your local legislature when there is legislation that has an effect on cyber or technology that you reach out, that you explain.
In my daily work, I’ve found it very fruitful, and I can do this because I have the position of seniority right now, but sitting down with law enforcement on joint cases and having an informal conversation where we talk about the challenges, where we talk about how things work. I spent quite a bit of time at law enforcement offices explaining how we do investigations, how our systems work. These people don’t necessarily notice.
And at the same time, they actually explain to me how a proper forensic investigation that actually holds up in court needs to work. So it’s a lot about understanding how the others work. How does the law work? What does it mean? What is illegal? What is not?
And when I was kind of a student, I felt that looking back, I was quite naive and thought I knew what’s good and bad, and today I think I’m totally confused about this. But just trying to understand the others and engage with others. I find it always interesting to talk to lawyers that work in cyber, even though I know a lot of lawyer jokes, but it’s kind of, you have to build these bridges.
Moderator: Thank you.
Frank: Okay. In this case, I think we can go into the break. I think you are around
Serge: Yes, I’m around.
Frank: So if there are additional questions, feel free to use the break. Also keep in mind that we have our sponsors out there answering any questions that you might have and having some swag, I guess. And we continue here at 11. Thank you.















