Modern forensic data acquisition in enterprise environments requires constant evaluation of approach, methods, tools and tactics. Multiple different ways of acquiring both logical and physical images from remote sources in corporate environments have been developed throughout the years, from deployment of physical resources to any number of remote acquisition methods. And with remote attacks and vulnerabilities being uncovered almost daily in some of the most unlikely corporate environments, incident responders need a tool that will quickly and effectively acquire the data they need to respond and track down these incidents in a forensically sound manner. This is the need that AIR from Binalyze seeks to fill and does so quite impressively.
Binalyze is based in Europe and has been in the enterprise forensics space for four years. AIR is their main product and is designed to acquire PC or Linux-based systems in the enterprise environment. The main focus of AIR is to acquire and analyze efficiently, because in breach incidents, time is of the essence. AIR is designed to be deployed in remote locations, so if the information security hub is in London and the company has offices in New York, Paris & San Francisco, the endpoint client can be deployed across the end-user spectrum to facilitate monitoring and collection, should an incident occur. This makes response convenient and fast!
System Requirements
There are up to two sets of system requirements for the use of AIR because there are two points at play – one for collection, which is called the “console,” and a target system, called the “endpoint”. The system requirements are quite light, however, and should be easily met by any modern system in use today.
The Console requirements are:
- CentOS 7 / Ubuntu 18.04 and above
- 4 cores CPU
- 8 GB RAM
- 256 GB storage
The Endpoint requirements are:
- Windows XP or a newer operating system (Server or Workstation) or
- Linux OS (Debian, Ubuntu, Redhat, Centos, Fedora)
- 2 GB+ RAM
- Minimum 2 GB free disk space
Deployment and Acquisition
The first element in the chain of monitoring and collection that needs to be in place is the presence of the Endpoint client, which helps facilitate all of the features of AIR. This client should be installed on all Endpoints where there is a potential for monitoring of activity and collection.
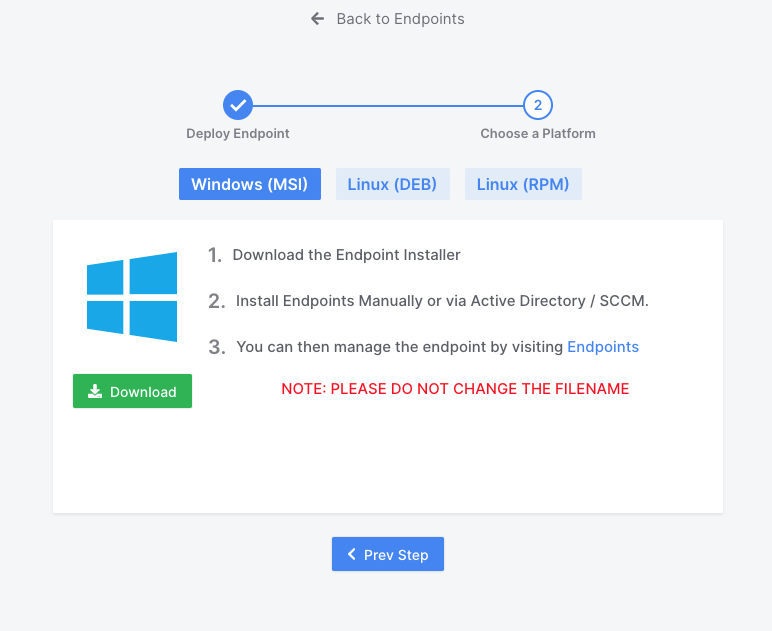
Binalyze AIR approaches collection from a somewhat different perspective, but a modern one nonetheless. The approach is such that we do not need to collect the physical medium to obtain all of the relevant data and this approach is a very viable one, particularly when we’re likely not dealing with deleted or unallocated data in breach incidents. The focus is on activity logs, registry files, email, RAM and any logical data that can help us identify what happened and who may be responsible. As such, the acquisition is geared toward this approach.
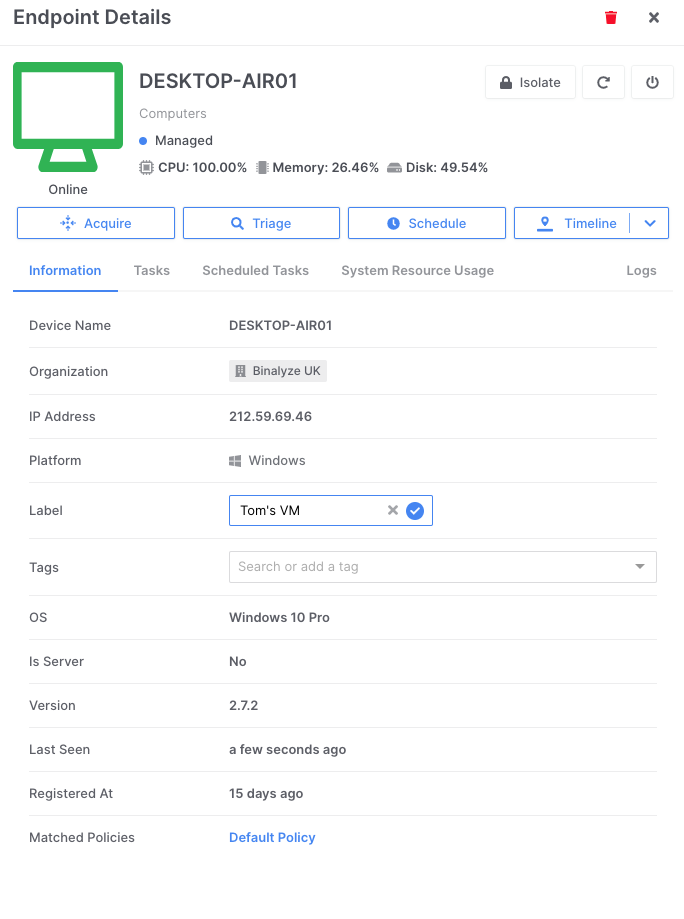
The GUI is simple to use and almost self-explanatory. We choose the endpoint(s) we are interested in collecting, as shown in the example below, and assign them a name. This could be any custom name or case number or incident designation. Notice, too, that we are able to immediately identify the name of the remote computer, view the operating system and see an overview of the current workload of the system.
Some great features that accompany AIR’s acquisition workflow are:
- Users can utilize a local or remote evidence repository. This means if the collection arm of the information security department is in a different location from the analysis arm, the image can be sent directly to the party responsible for analysis
- Images can be compressed and encrypted for ease of secure transfer
- Images can be prioritized and customized. Users can choose to collect the MBR, shellbags, event logs, web history registry and multiple other predefined parameters (see below)
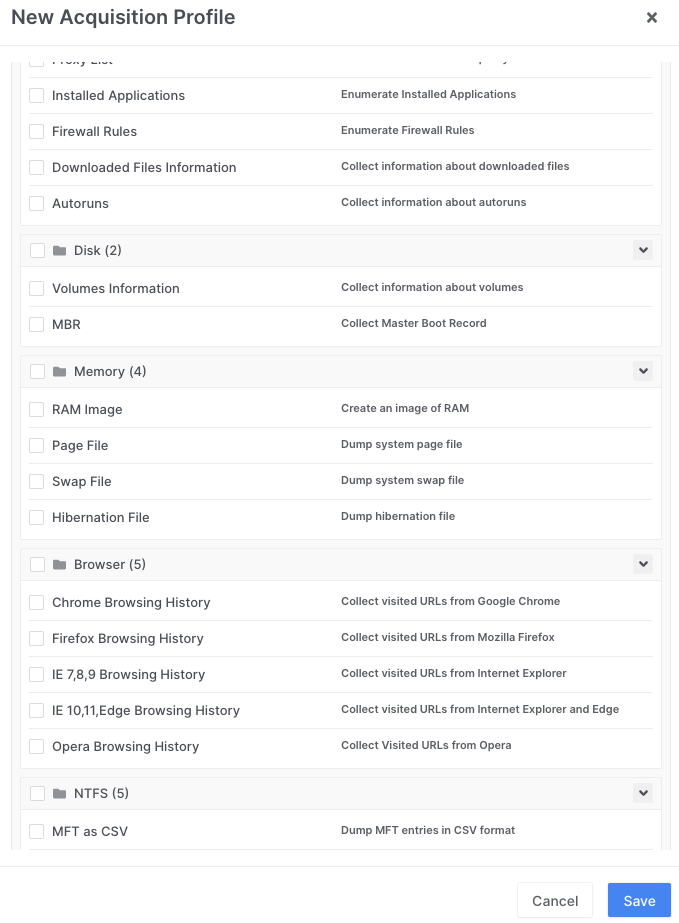
- Custom profiles can also be created. This helps when dealing with repeated threats or threats which may have a similar footprint with minor variants
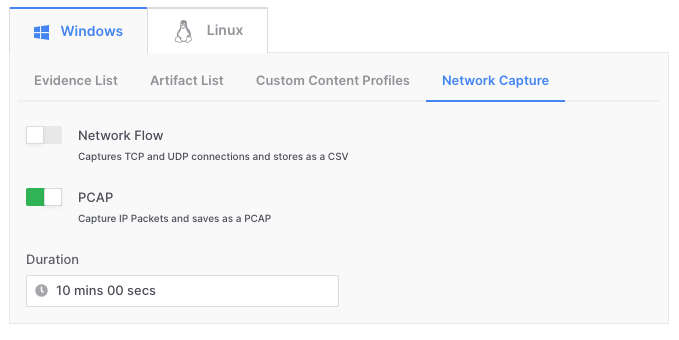
- Packet captures can be acquired in real time and customized for interval (see below)
Data acquisition time is naturally dependent on variables such as network speed, size of acquisition data and method of target medium, however acquisition of our test image was very fast. This is another reason why logical data imaging is generally more desirable in this environment. Binalyze also offers a free imaging tool for users called Acquire, but it is also built-into the AIR platform.
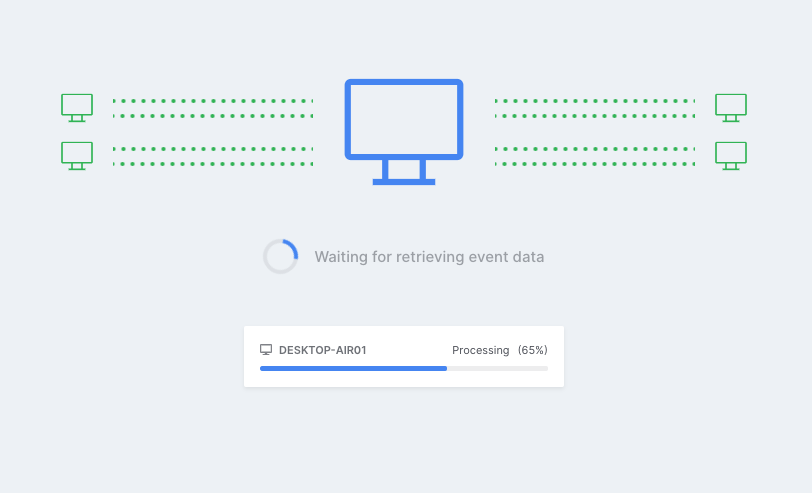
Once the image is complete, it can be stored in either binary, native or CSV format, depending on the type of data and the user parameters at the time of collection. This would have obvious benefits in e-Discovery applications where an entire PST/OST or MBOX needs to be collected from a particular user or server and ingested into culling and analysis software.
Other AIR Tools
Several very useful features are included with AIR and more are slated for addition into the tool. The first one of these is the ability to triage endpoint evidence. This is particularly useful in cyber security environments because it allows the construction of rules for the triage that are very user-friendly.
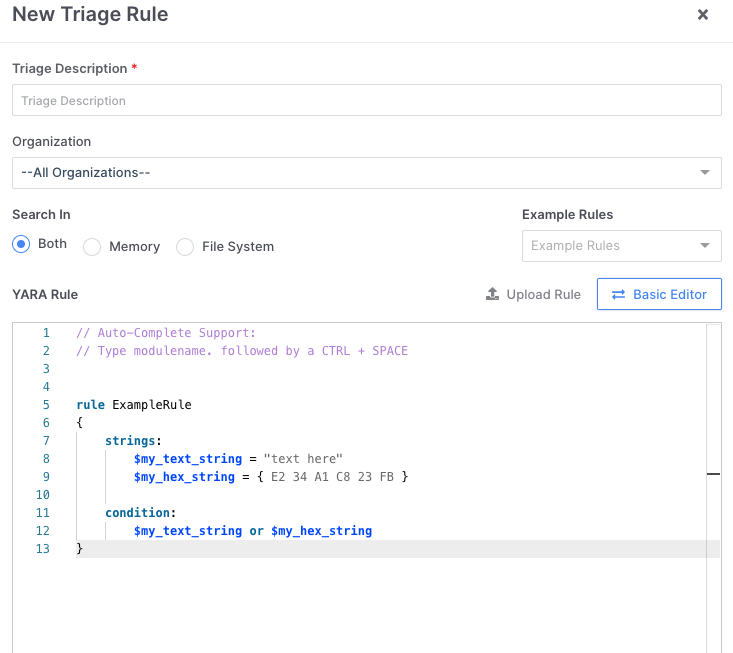
The triage feature allows quick assessment of the memory (RAM) of the endpoint machine, the file system or both at the same time, to try and identify the key areas of vulnerability and try to track down bad actors using the data. Custom triage rules can also be coded into the tool for a more targeted approach to the acquisition and analysis.
The Timeline feature is another highlight built into AIR that is constantly being honed, updated and refined based upon user input. Currently, the Timeline feature includes the ability to:
- Collect all pieces of evidence that have time stamps from multiple sources into one timeline analysis
- Limit collection of evidence to a particular time frame
- Flag events in the timeline
- Add milestone events as notable in the analysis
- Search for particular files or events and filter for a specific type of event
- Allow multiple analysts to log in and view the same timeline events and put more eyes on the data, increasing collaboration (this is permission-based)
The Timeline feature in AIR is designed to cut-down analysis time and increase teamwork in incident response to increase efficiency and effectiveness.
Reporting in AIR
Reporting in AIR is simple and effective. The AIR report opens in your default web browser as an HTML report and is navigable through the table of contents on the left-hand side of the browser window:
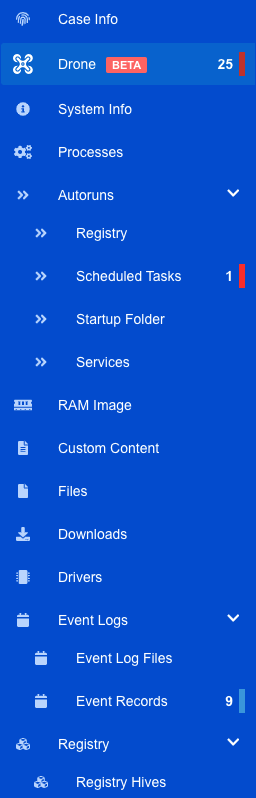
As you can imagine, the reporting for any given category provides an exhaustive listing of which artifact we’re analyzing, the source file, dates, times and other relevant metadata. Categories such as event logs and registry being automatically parsed for the user in this report has obvious advantages to help streamline analysis and get the work done faster. It’s a very intuitive and easy-to-use feature within AIR.
In Conclusion
Over a decade working in the digital forensic space has seen tools come and go, many of which claim to be an all-in-one solution product, but fail to deliver on their promises. In the case of AIR from Binalyze, it’s clear the time and effort went into creating a product that would fill multiple needs in the enterprise-based incident response space by creating a tool that is easy to use, fast, efficient, intuitive and robust. If you’re looking to add to your current toolbox of enterprise incident response and cybersecurity forensic data acquisition & analysis, AIR from Binalyze could be just the solution you’ve been seeking!
About The Author
Patrick Siewert is the Principal Consultant of Pro Digital Forensic Consulting, based in Richmond, Virginia (USA). In 15 years of law enforcement, he investigated hundreds of high-tech crimes to precedent-setting results and continues to support litigation cases in his digital forensic practice. Patrick is a graduate of SCERS & BCERT and holds several vendor-neutral and specific certifications in the field of digital forensics and high-tech investigation and is a court-certified expert witness in multiple digital forensic disciplines. He continues to hone his digital forensic expertise in the private sector while growing his consulting & investigation business marketed toward litigators, professional investigators and corporations, while keeping in touch with the public safety community as a Law Enforcement Instructor.















